Preface: The registration of CVE records is largely out of sync with the time of the event. Perhaps the new release of CVE record by today, however it was happened few weeks or months ago. But with reference of these vulnerabilities records. Vulnerability scanner can precisely provide a result to you after scan.
Background: Vim is a greatly improved version of the good old UNIX editor Vi. The core of VIM is written in C. Most of the files are .c and .h in the folder itself (not in sub folders).
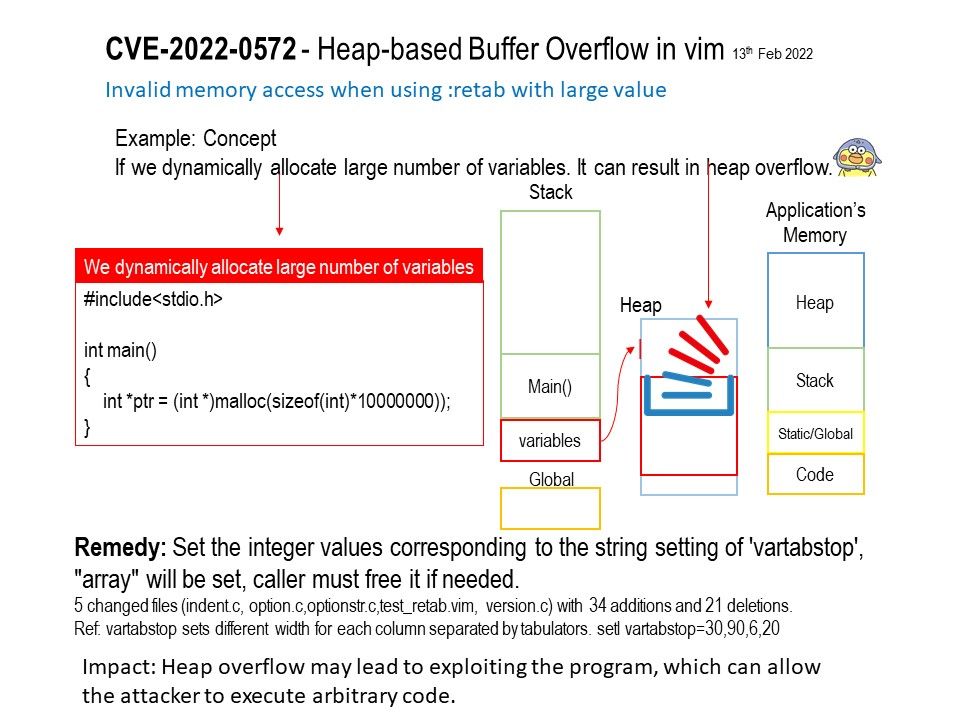
Heap is a region of process’s memory which is used to store dynamic variables. These variables are allocated using malloc() and calloc() functions and resize using realloc() function, which are inbuilt functions of C.
If we dynamically allocate large number of variables (refer to attached diagram). It can result in heap overflow.
Vulnerability details: A flaw was found in vim. A possible heap-based buffer overflow could allow an attacker to input a specially crafted file leading to a crash or arbitrary code execution.
What kinds of “arbitrary code” will the attacker typically run?
The attacker could get a simple directory listing by executing an “ls” on Linux/Unix. Furthermore, the attacker can examine your file system. Alternatively, the attacker could run commands to delete files, launching a data destruction and/or denial-of-service-attack. The attacker could also steal data, downloading sensitive files.
Impact: Heap overflow may lead to exploiting the program, which can allow the attacker to execute arbitrary code.
Official announcement: Please refer to the link for details – https://github.com/vim/vim/commit/6e28703a8e41f775f64e442c5d11ce1ff599aa3f