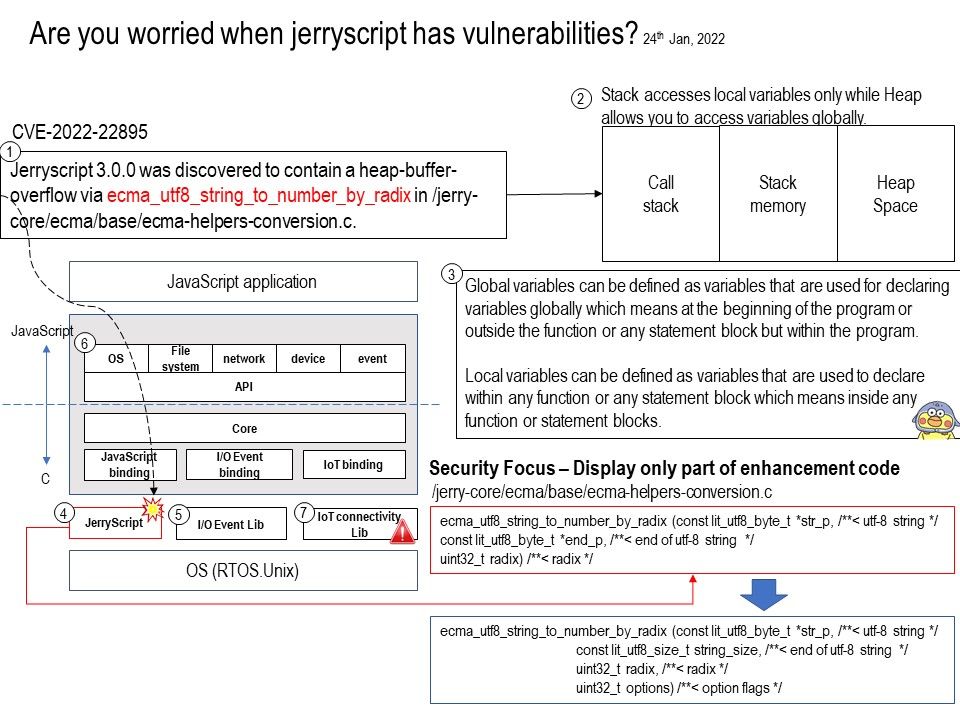
Preface: Did you know someone is behind your computer?
Background: WRH–300x series is wireless LAN router for microminiature hotel corresponding to 11bgn300Mbps which can enjoy the Internet with the speed of about 4 times of LTE line.
Ref: 11BGN, 11AGN, and 11AC are wireless standards supported by wireless products. Among them, 11BGN refers to the 802.11b, 802.11g, and 802.11n standards, 11AGN refers to the 802.11a, 802.11g, and 802.11n standards, and 11ac refers to the 802.11ac standard.
Vulnerability Details: Certain versions of ELECOM LAN Routers allows an attacker on the adjacent network to execute an arbitrary OS command via unspecified vectors.
Synopsis: The PPPoEd service is used to create Point-to-Point Protocol over Ethernet (PPPoE) connections on LAN Router. The PPPoEd daemon uses the mount system command to load and start a networking device during PPPoE connection negotiation. However, PPPoEd relies on the PATH environment variable to locate the executable file for the mount command.
Likehood: A malicious user may be able to create an arbitrary program labeled mount. Execute Hijack Execution Flow,doing Path Interception by PATH Environment Variable.
PATH variable to refer to the new mount executable. When PPPoEd checks the PATH variable to locate the executable for the mount command, it follows the PATH entry enter the new version of mount (arbitrary program labeled mount).
Affected Products: WRH-300BK3 firmware v1.05 and earlier, WRH-300WH3 firmware v1.05 and earlier, WRH-300BK3-S firmware v1.05 and earlier, WRH-300DR3-S firmware v1.05 and earlier, WRH-300LB3-S firmware v1.05 and earlier, WRH-300PN3-S firmware v1.05 and earlier, WRH-300WH3-S firmware v1.05 and earlier, and WRH-300YG3-S firmware v1.05 and earlier
Official announcement: https://www.elecom.co.jp/news/security/20220208-02/
.jpg?width=1920&height=1080&fit=bounds)
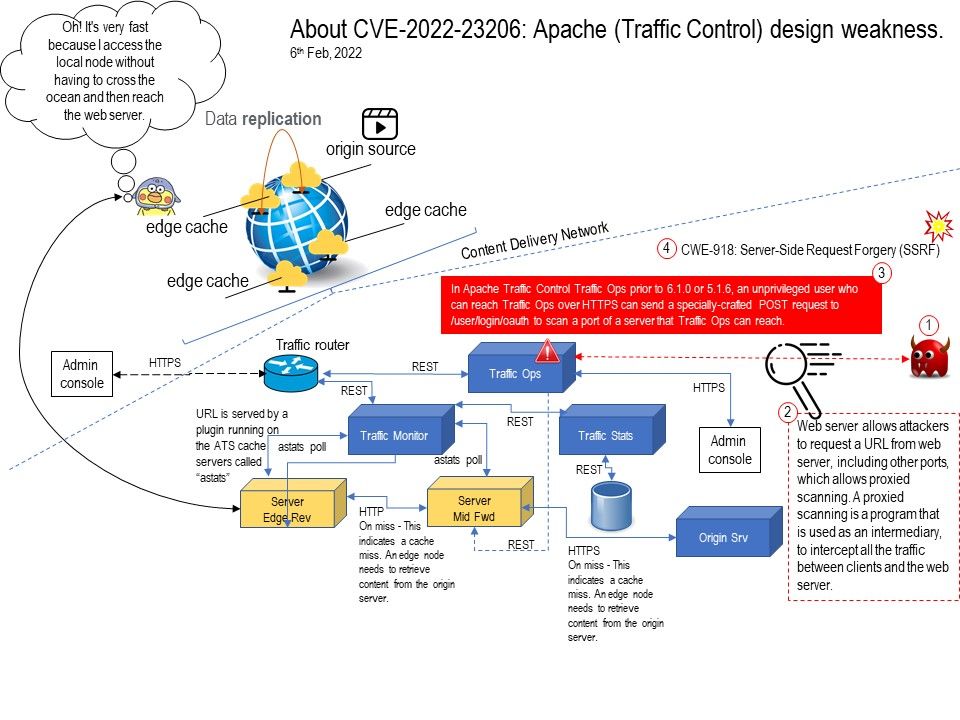
.jpg?width=1920&height=1080&fit=bounds)
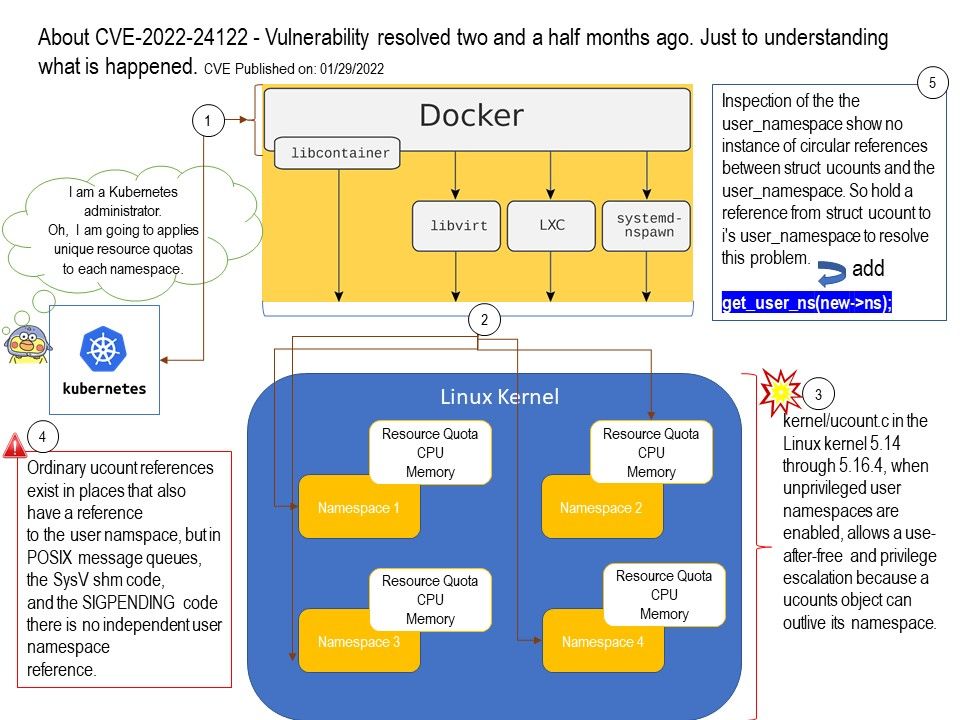
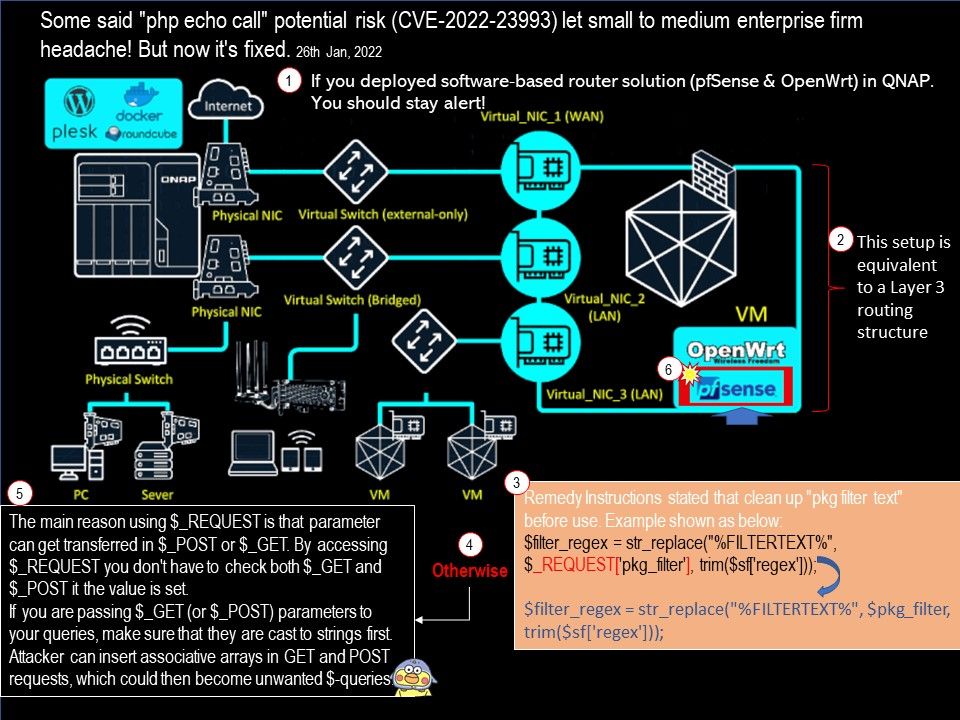
.jpg?width=1920&height=1080&fit=bounds)