Preface: What are backports in traditional Linux?
“Backporting” is the process of making new software run on something old. A version of something new that’s been modified to run on something old is called a “backport”. The Backports Project develops tools to automate the backporting process for Linux drivers. These tools form the backports suite.
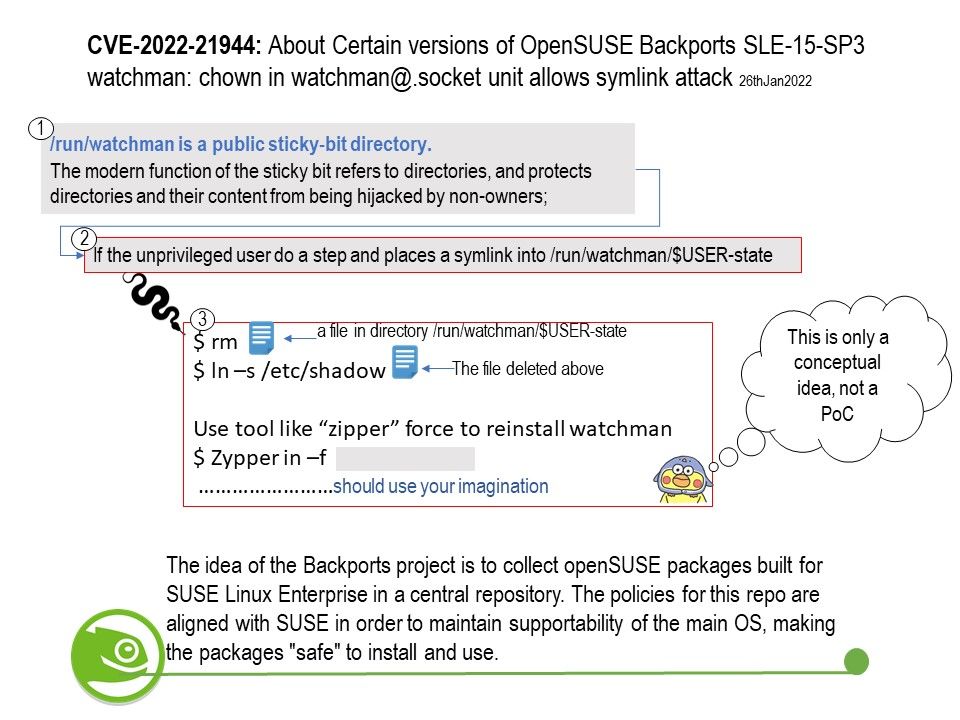
Background: The idea of the Backports project is to collect openSUSE packages built for SUSE Linux Enterprise in a central repository. The policies for this repo are aligned with SUSE in order to maintain supportability of the main OS, making the packages “safe” to install and use.
The openSUSE:Backports projects are built as “Maintenance” projects. This is a special type of project which not only contains the latest build of a package, but also a history of previous releases. It’s also how the openSUSE updates projecs are managed.
Vulnerability details: A UNIX Symbolic Link (Symlink) Following vulnerability in the systemd service file for watchman of openSUSE Backports SLE-15-SP3, Factory allows local attackers to escalate to root.
Below details is the explanation of Matthias Gerstner.
The problem here is that watchman should continue working as normal on the command line without using systemd. This means that an unprivileged watchman instance must be able to create /run/watchman/$USER-state. This is why /run/watchman is a public sticky-bit directory.
What does a sticky bit do?
The modern function of the sticky bit refers to directories, and protects directories and their content from being hijacked by non-owners;
Official announcement: Please refer to the link for details https://bugzilla.suse.com/show_bug.cgi?id=1194470