Preface: If no open source software concept in our world, technology is hard to become common. Even though you concern cyber security. They can fixed it when there is vulnerability occurs.
Background: pfSense is an open source firewall and routing platform based on FreeBSD. pfSense can be installed on physical computers or virtual machines, and can act as an independent firewall and router in the network. It is equipped with a Web user interface for administrative tasks such as setting and updating, which makes it easier to use.
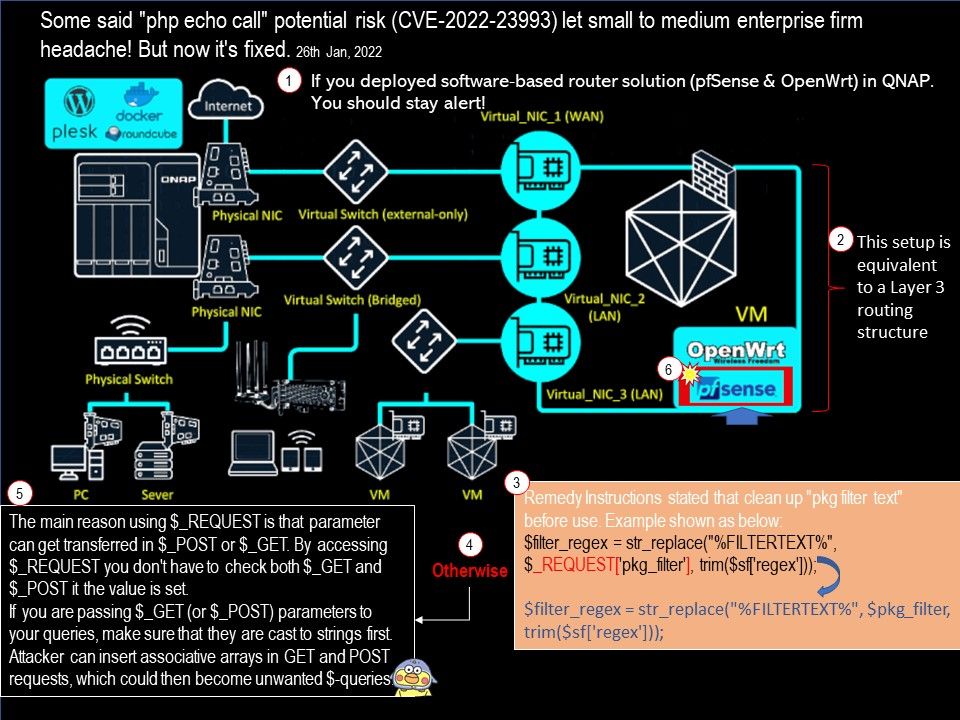
Vulnerability details: If you accept QNAP solution turn your NAS into a virtual router. This vulnerability found on pfSense this time remind you should stay alert. The following vulnerability was found:/usr/local/www/pkg[.]php in pfSense through 2.5.2 uses $_REQUEST[‘pkg_filter’] in a PHP echo call.
The main reason using $_REQUEST is that parameter can get transferred in $_POST or $_GET. By accessing $_REQUEST you don’t have to check both $_GET and $_POST it the value is set.
If you are passing $_GET (or $_POST) parameters to your queries, make sure that they are cast to strings first. Attacker can insert associative arrays in GET and POST requests, which could then become unwanted $-queries.
Official article, what remedies they did: Please refer to the link – Please refer to the link – https://github.com/pfsense/pfsense/commit/5d82cce0d615a76b738798577a28a15803e59aeb