Preface: NGINX Controller provides lightning-fast application delivery and API management for modern app teams.
Background: What is a Data Plane?
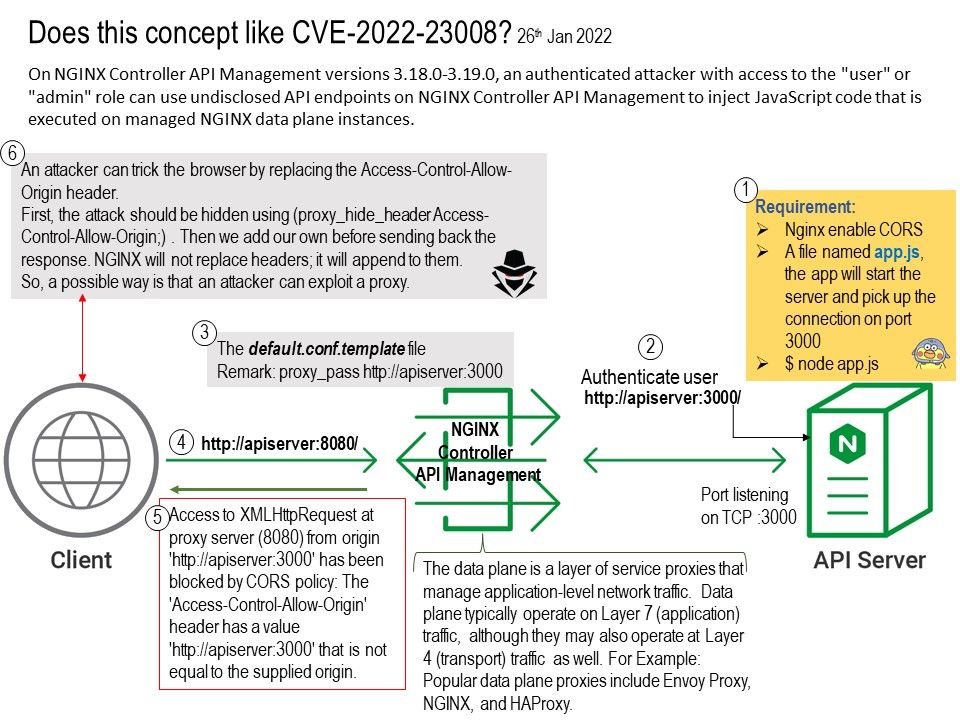
The data plane is a layer of service proxies that manage application-level network traffic. Data plane typically operate on Layer 7 (application) traffic, although they may also operate at Layer 4 (transport) traffic as well. For Example: Popular data plane proxies include Envoy Proxy, NGINX, and HAProxy.
Layer seven refers to a layer of security built into the open systems interconnect model. This is the highest level of security in the application level that supports end-user applications and processes. Defenses and attacks will be based on this area. So some experts firm will be focus layer 4 and Layer 7.
Vulnerability details: CVE-2022-23008 – Successful exploitation allows an attacker to read and/or write files on the NGINX data plane instance. The access to files is limited to the user running the NGINX process, typically the nginx user.
Does this concept like CVE-2022-23008? An attacker can trick the browser by replacing the Access-Control-Allow-Origin header.
First, the attack should be hidden using (proxy_hide_header Access-Control-Allow-Origin;) . Then we add our own before sending back the response. NGINX will not replace headers; it will append to them.
So a possible way is that an attacker can exploit a proxy.
If you are interested in the details, please refer to the attached diagram.
Vendor announcement: Final – K57735782: NGINX Controller API Management vulnerability CVE-2020-23008 – https://support.f5.com/csp/article/K57735782