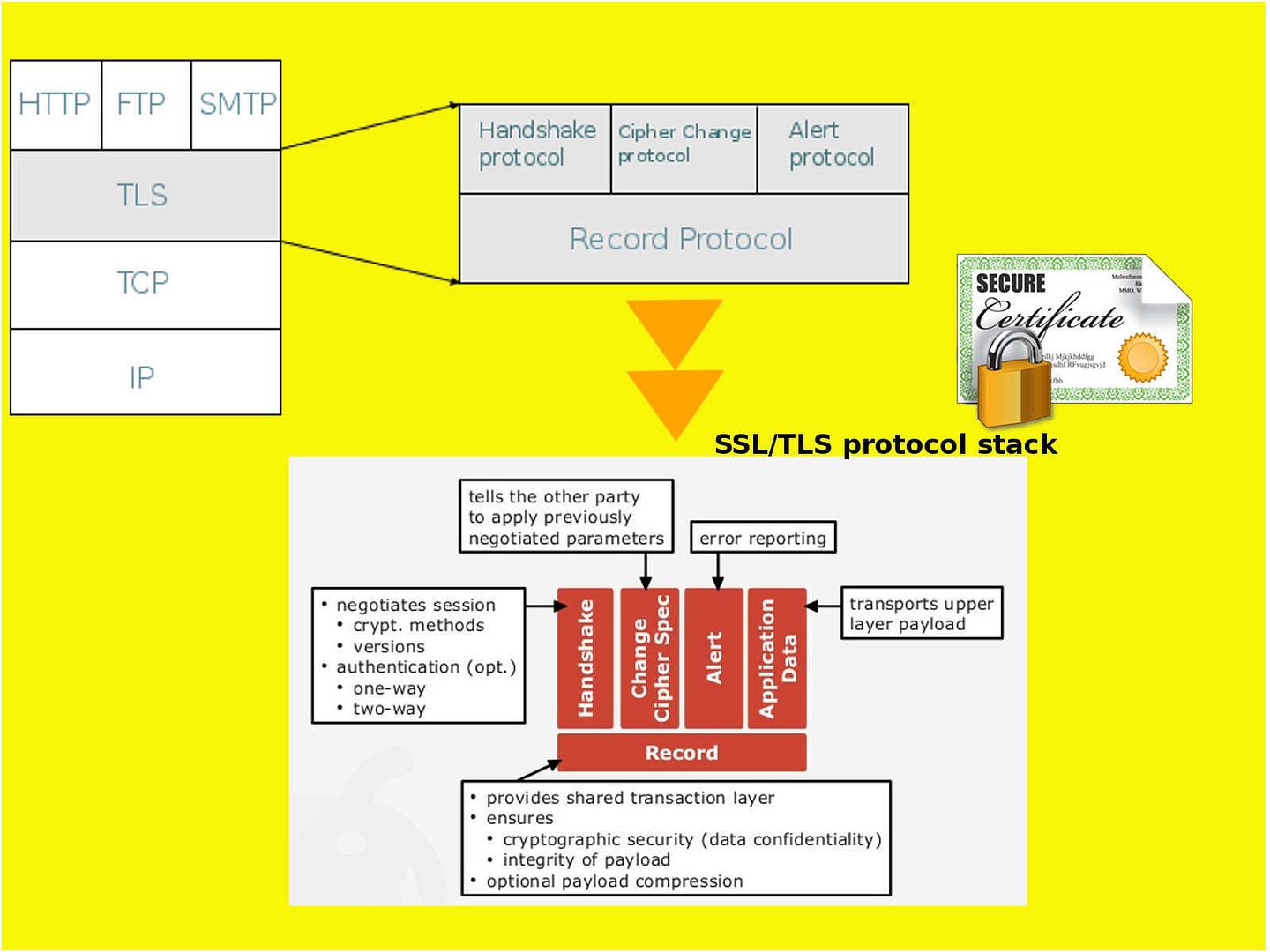
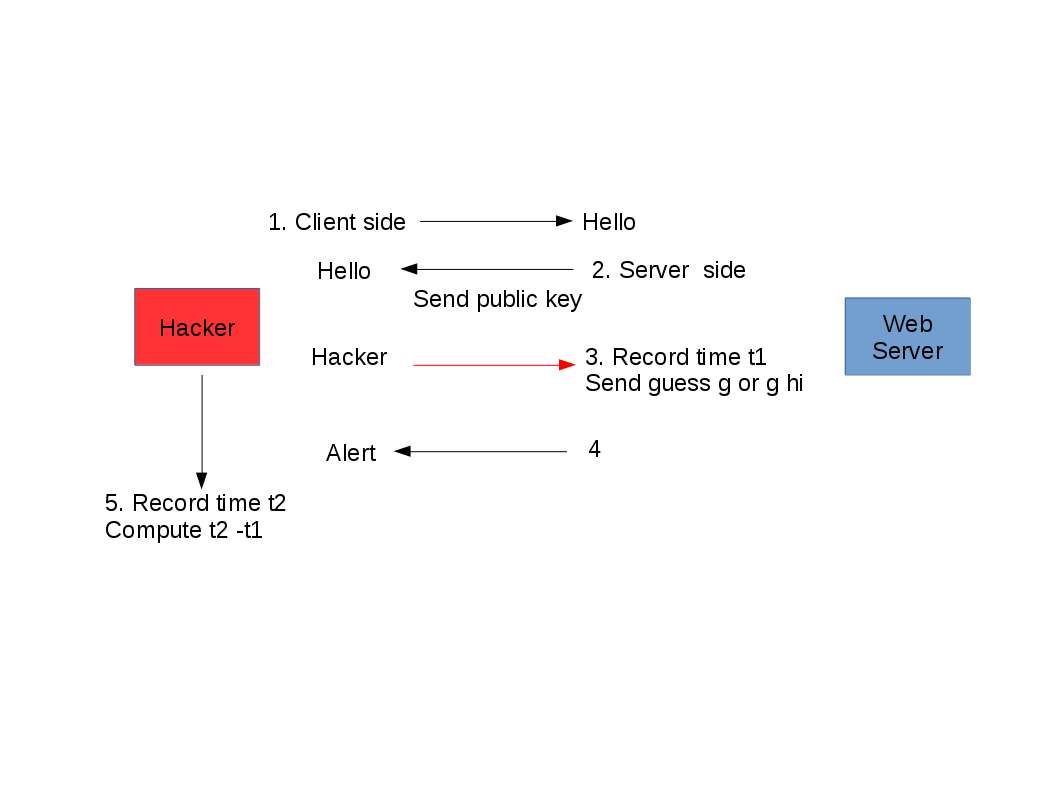
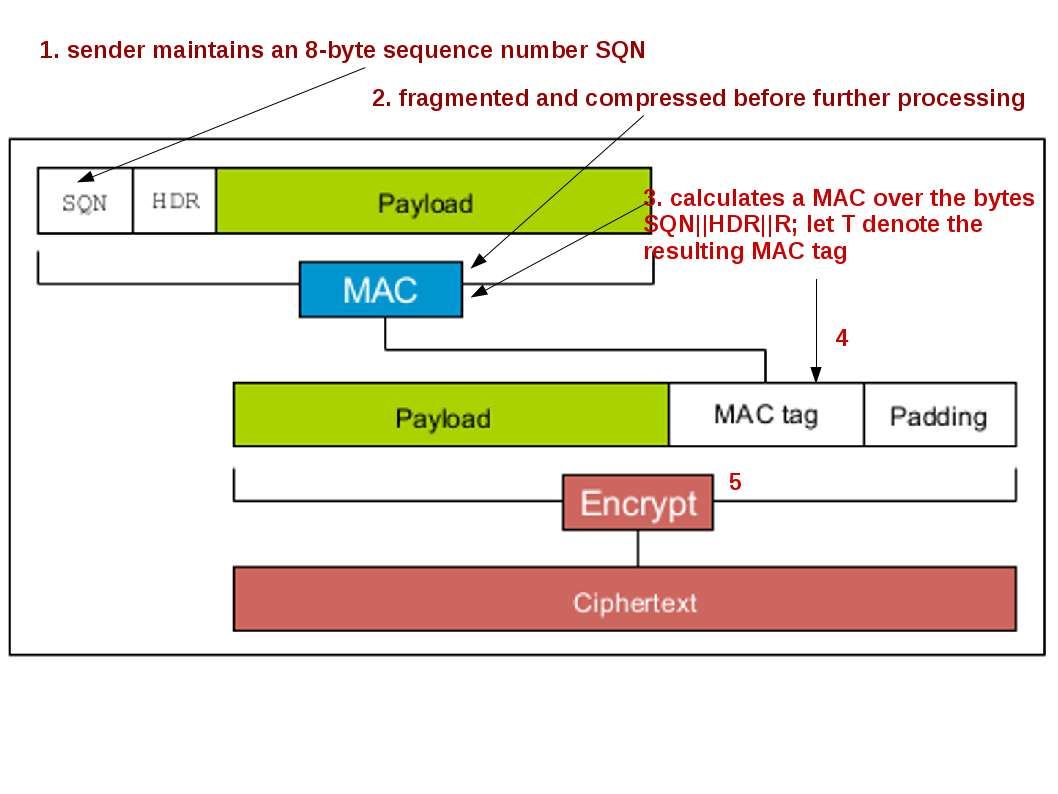
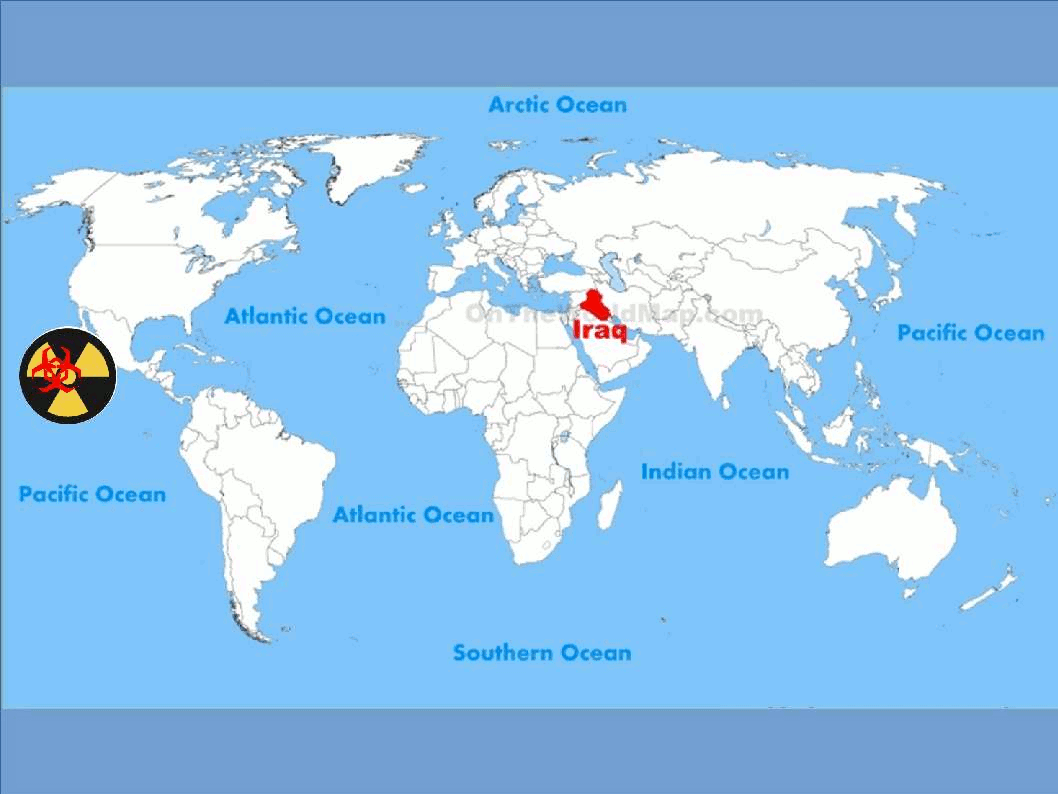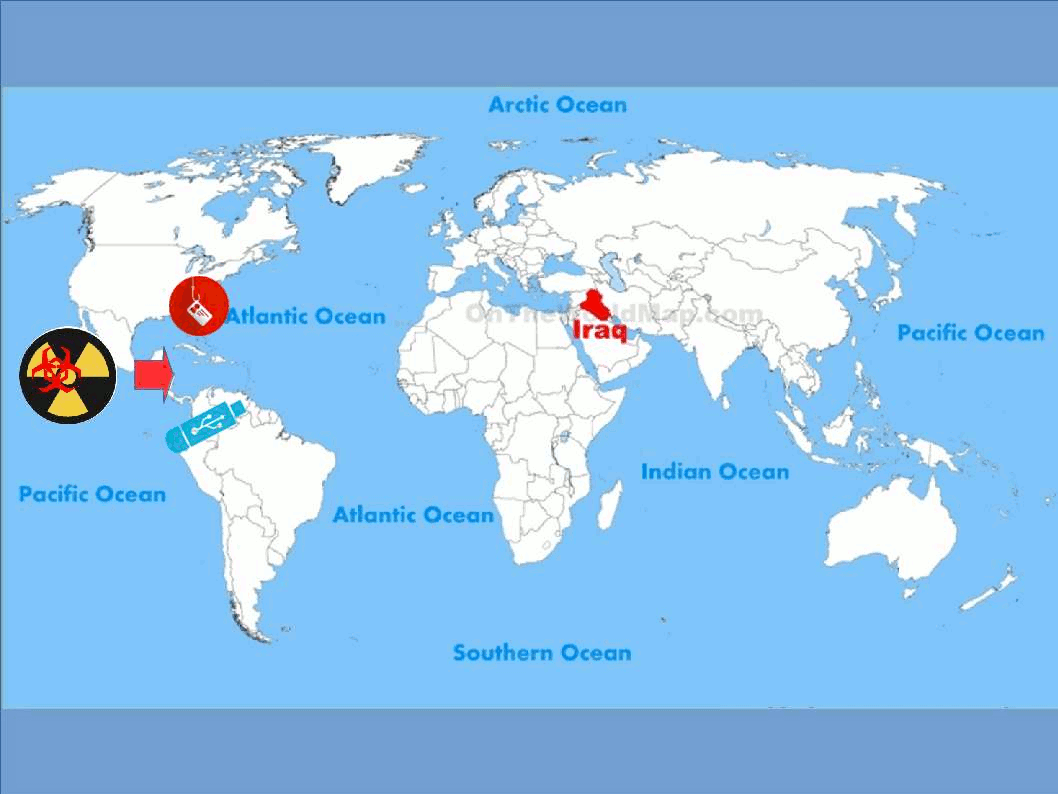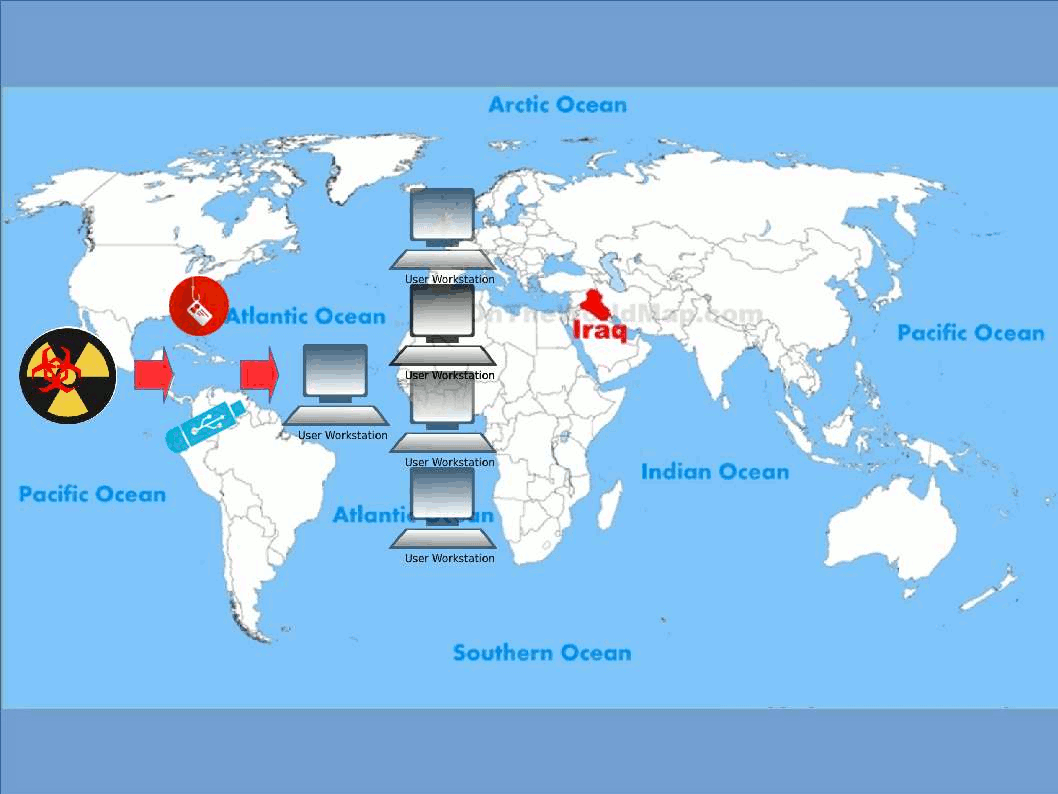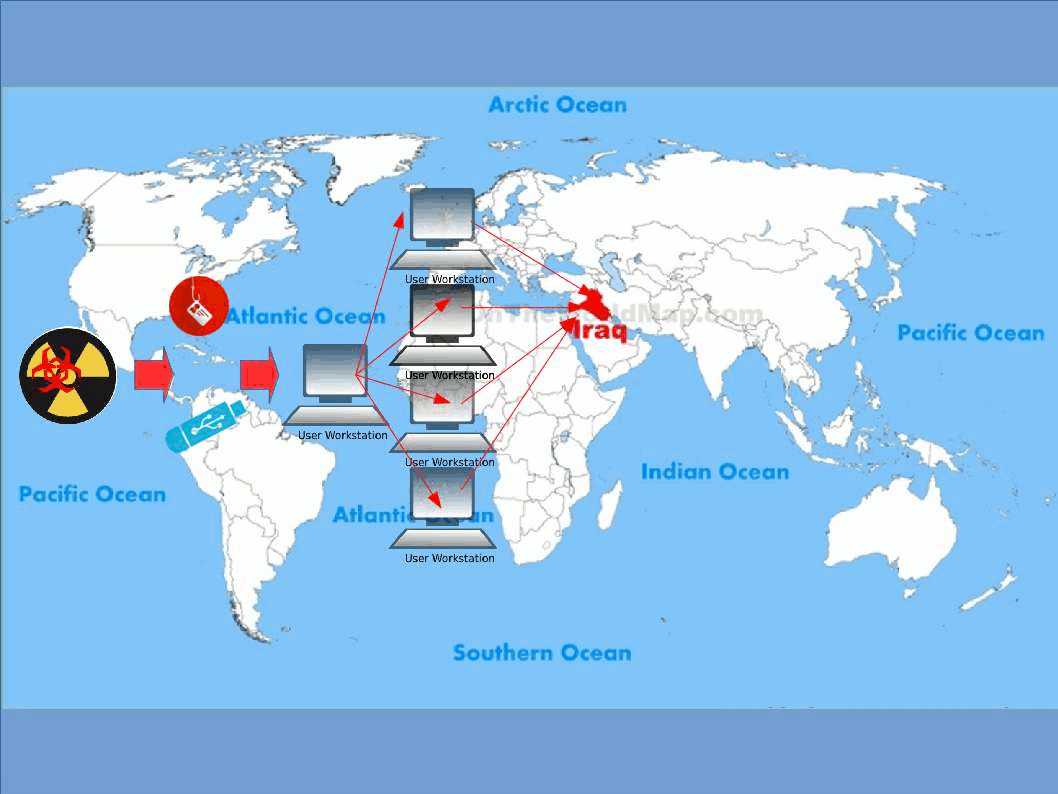
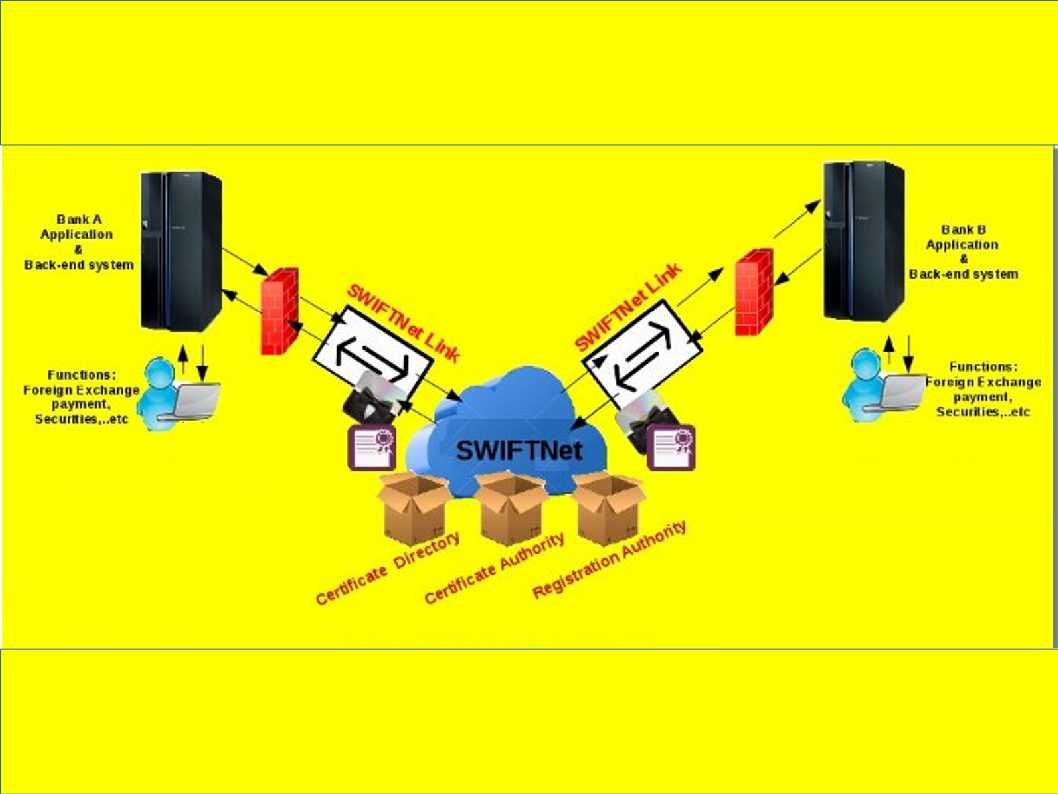
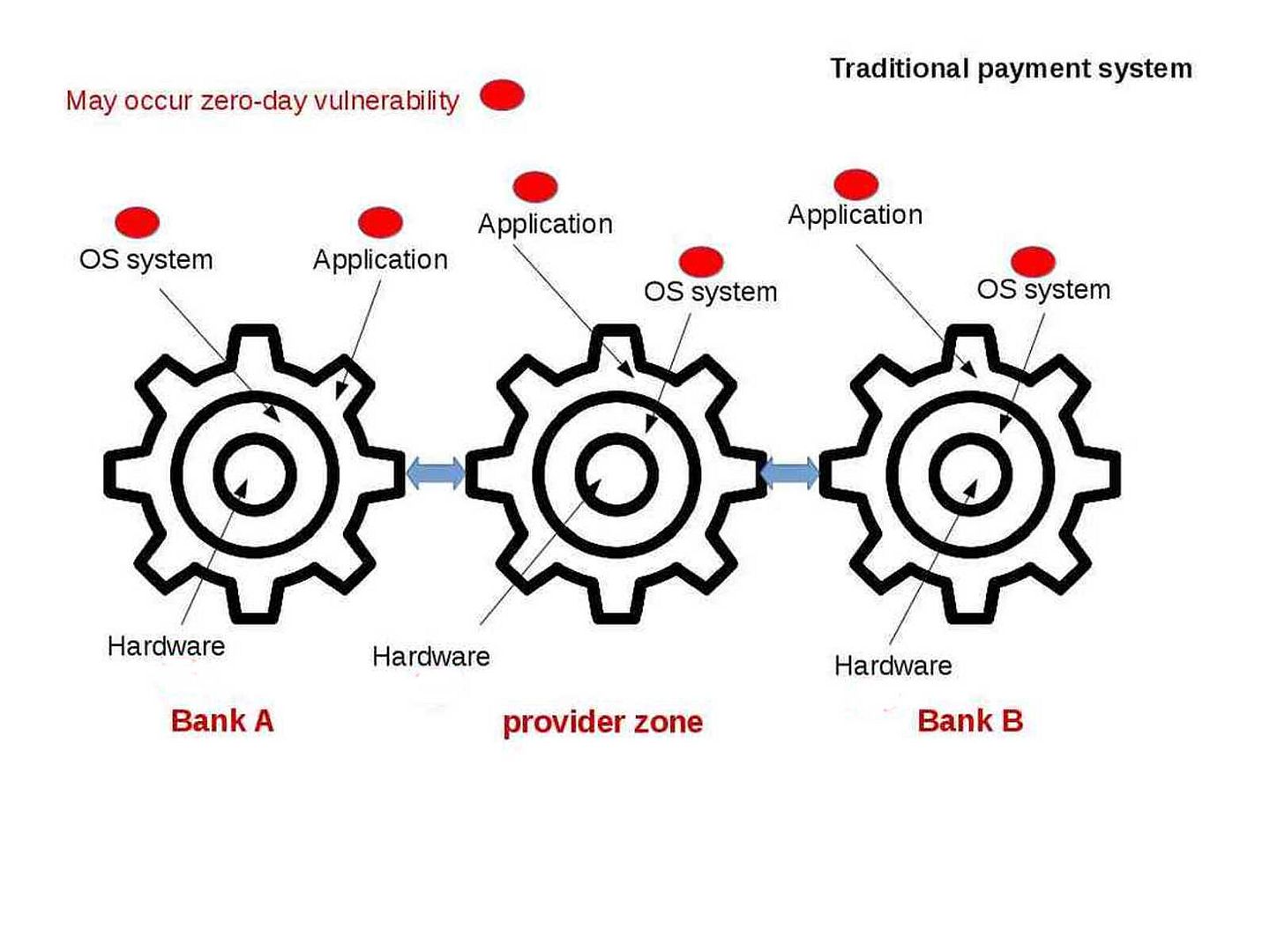
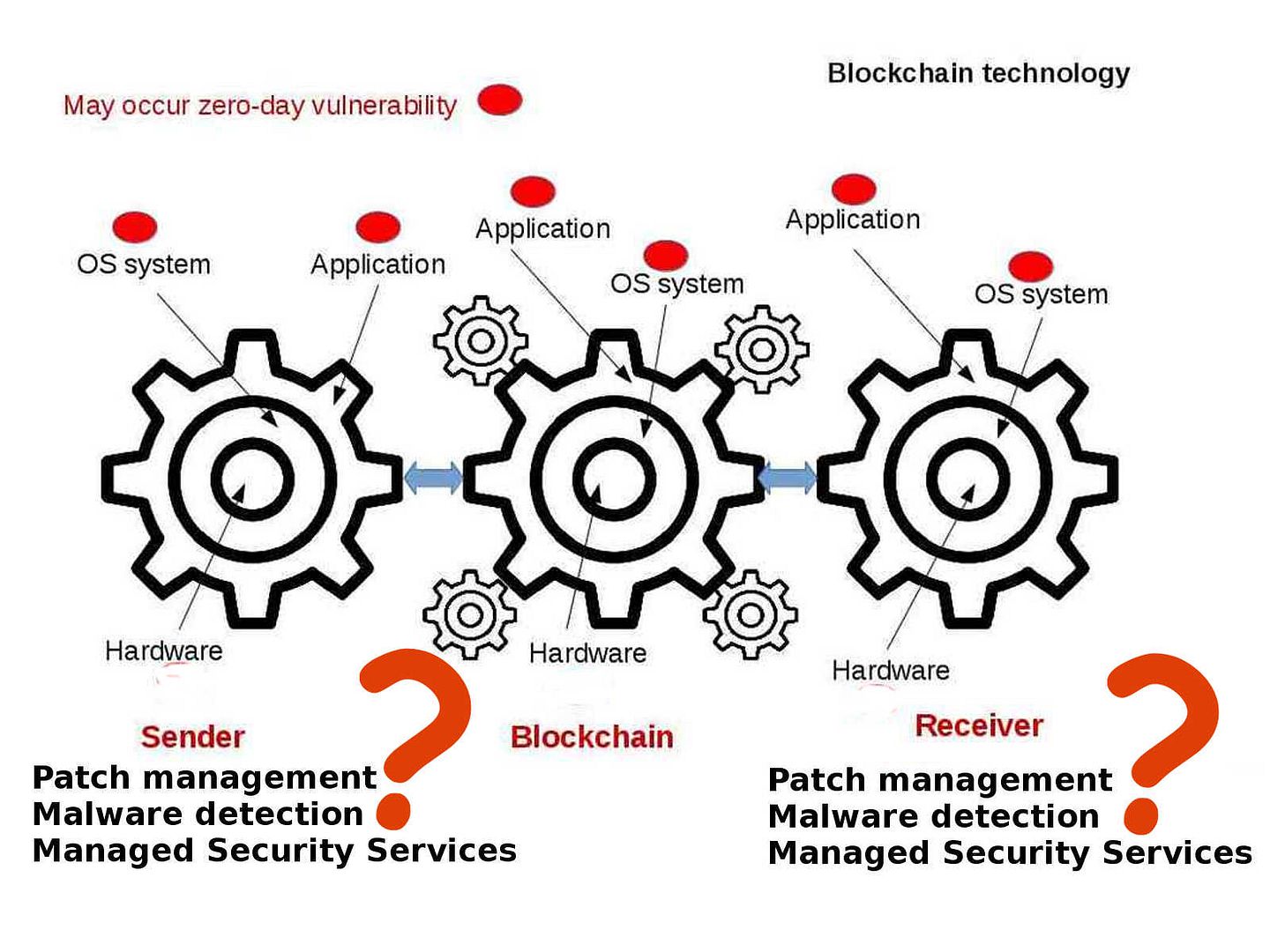
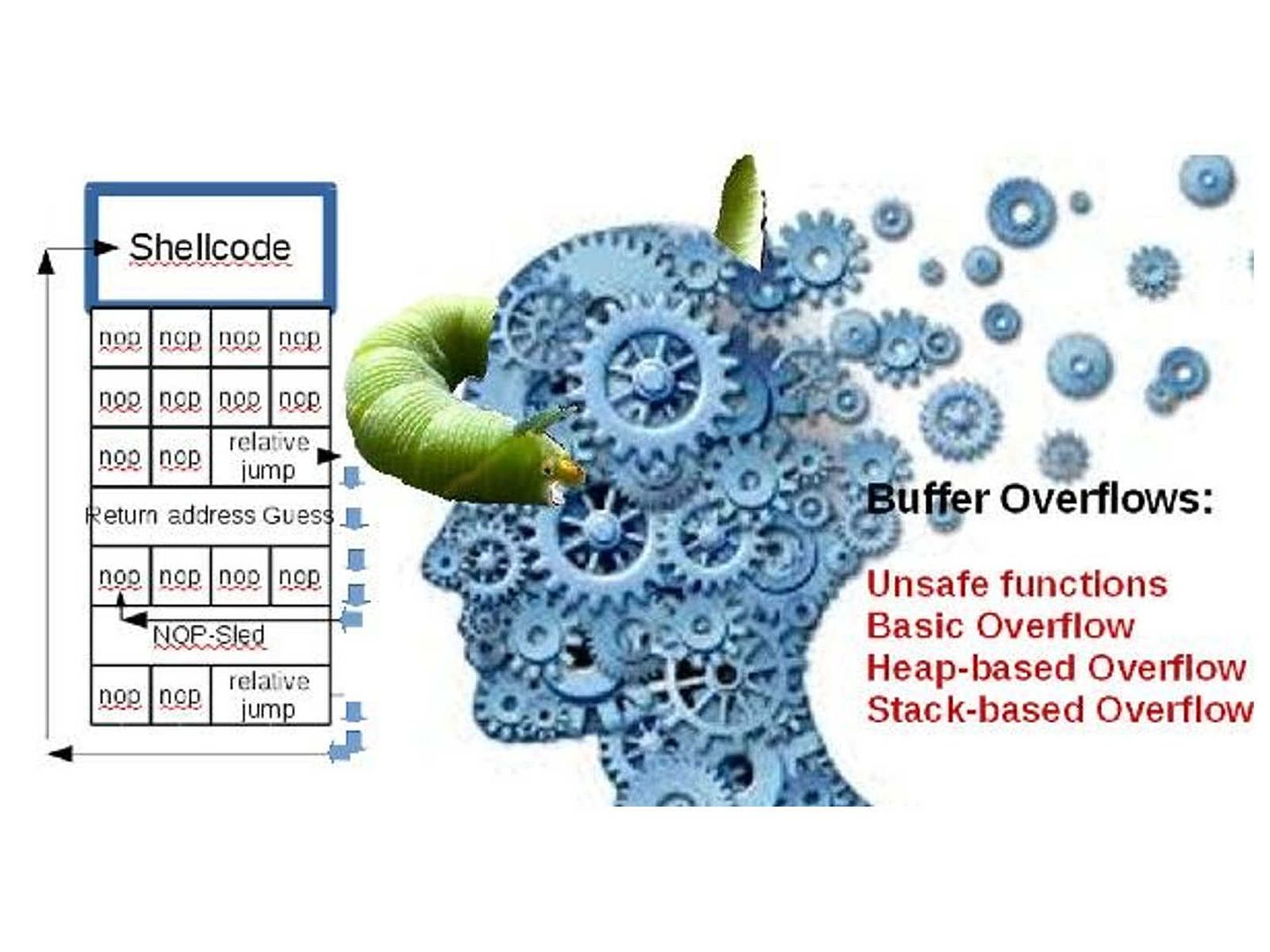
Enterprise firm execute data classification to protect corporate important data. Follow the code of practise, confidential data contained high level of sensitivity label requires encryption. The whistleblower Edward Snowden alerts the people in the world on 2013. But you might have question to ask till now, what sort of personal data we need to protect. Seems end user computing mostly ignore by users. The traditional idea is that we enforce the preventive control from server end. As times go by, mobile phone twisted the IT world. IT Renaissance, literally reborn. The usage of computer not limit to location and time zone. We can execute the remittance or payment on mobile phone. You do a backup or synchronize mobile data when go home. Sure you can upload everything on cloud.
In regards of global surveillance program by US government
It looks that surveillance program is a never ending story! Why? From official perspective domestic surveillance program can effectively monitoring terrorist attacks and criminal activities. NSA web page slogan have the following statement.
“Defending our nation. Securing the citizens.”
We have no objection that collection of internet data, mobile phone voice and data exchange as a weapon fright againts crime. To be honest we don’t have rights! But question raised how to identify the usage of this data?We are not the perpetrator, logically we might not afraid of this control?
Highlight the NSA data collection methoglogy:
- Real-Time Yahoo Email Scanning
- Domestic Intercept Stations
- Bulk Collection of U.S. Citizens’ Phone Records
- The PRISM Program: Source of Raw Intelligence
- Google Cloud Exploitation
- Cellphone Tracking
- Spying Toolbox: Servers, routers, firewall devices, computers, USB, keyboard, wireless LAN, cell phone network & mobile phone
- FBI Aviation Surveillance Operations (FBI Hawk Owl Project)
- XKeyscore: Our Real-Time Internet Monitoring Capability
Above details not a confidential data, you can easy find this information. Please take a visit to NSA front page, for more details please see below:
https://nsa.gov1.info/surveillance/
US Government with high visibility statement let’s the citizens know they are under surveillance. A open method of NSA is use a tool so called “XKEYSCORE”. When an US speaker logs into a Yahoo email address, XKEYSCORE will store “mail/yahoo/login” as the associated appID. This stream of traffic will match the “mail/english” fingerprint (denoting language settings). When a browser visits a site that uses Yield Manager, a cookie will be set. This cookie is used to identify whether the browser has loaded an advert and when and where it loaded it (which detects Yahoo browser cookies). Yield Manager also collects information such as:
– the date and time of your visit to the website.
– IP address.
– the type of browser you are using.
– the web page address you are visiting.
XKEYSCORE appIDs and fingerprints lists several revealing examples. Windows Update requests appear to fall under the “update_service/windows” appID, and normal web requests fall under the “http/get” appID. XKEYSCORE can automatically detect Airblue travel itineraries with the “travel/airblue” fingerprint, and iPhone web browser traffic with the “browser/cellphone/iphone” fingerprint.
XKEYSCORE features highlight:
- Tracking Bridge Users
- Tracking Tor Directory Authorities
- Tracking Torproject.org Visits
See below part of the XKEYSCORE sourcecode can bring you an idea XKEYSCORE focus on TOR routers.
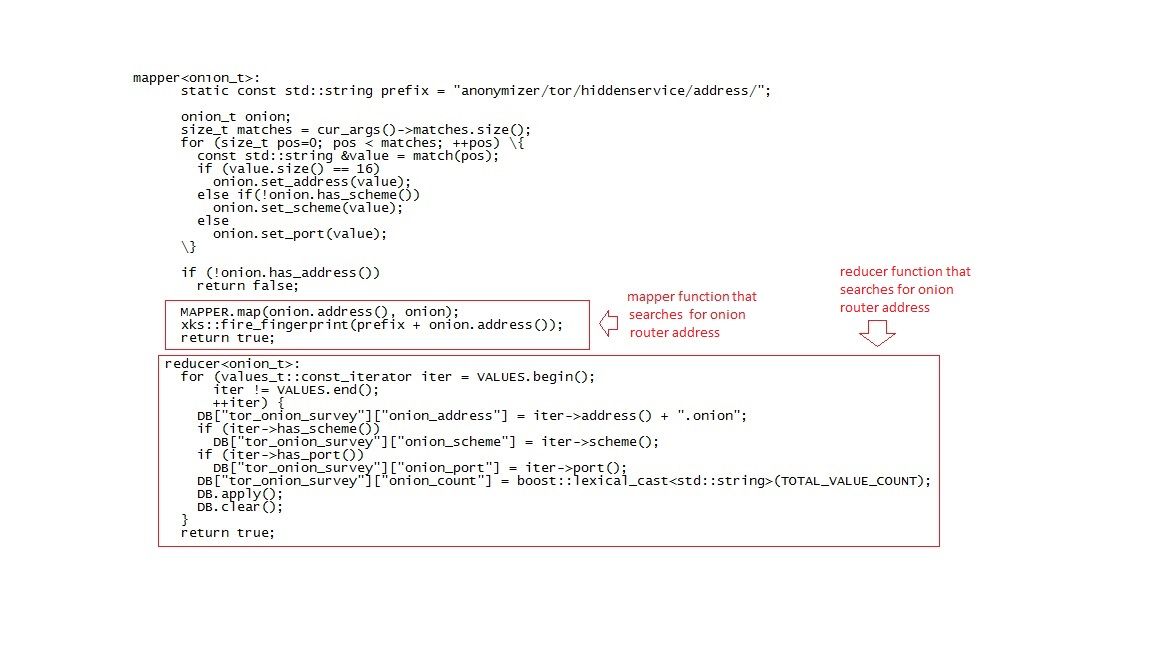
Traffic flows into an XKEYSCORE cluster, the system tests the intercepted data against each of these rules and stores whether the traffic matches the pattern.
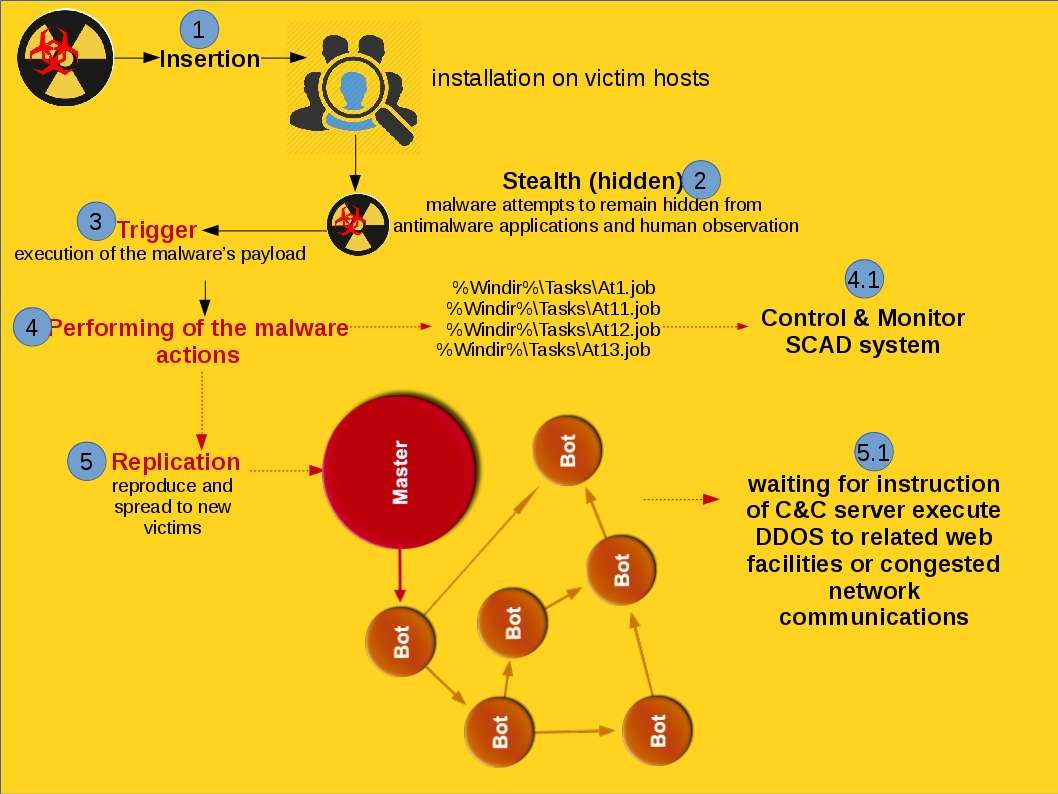
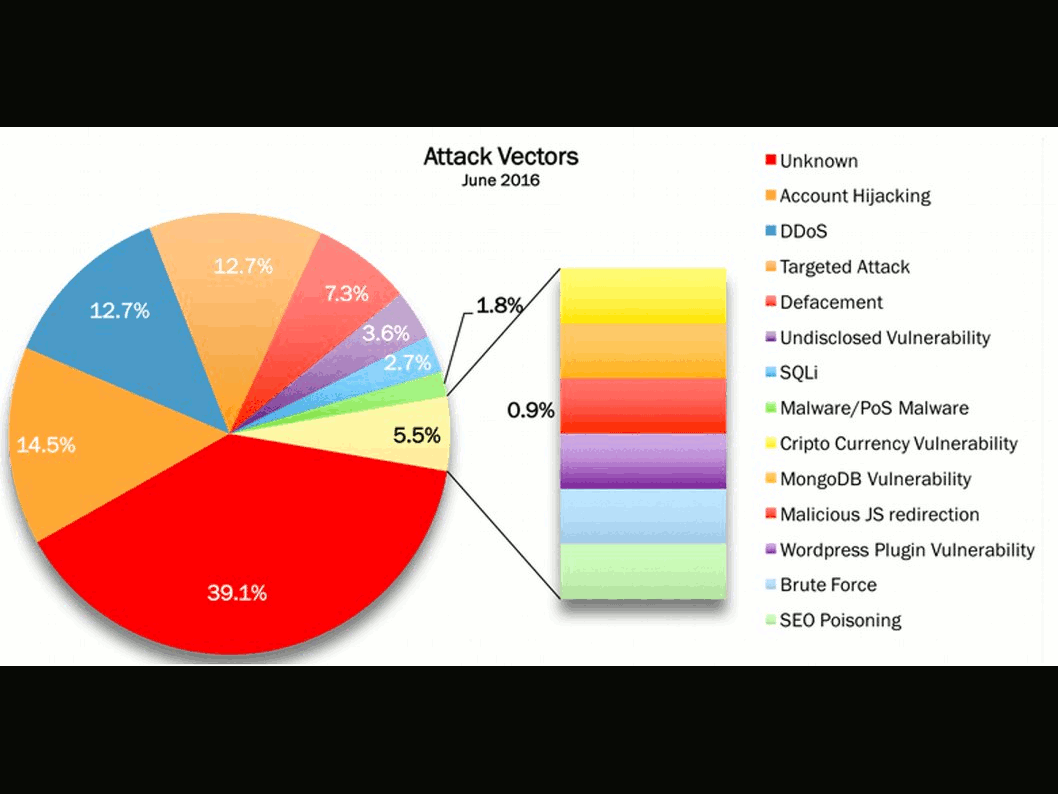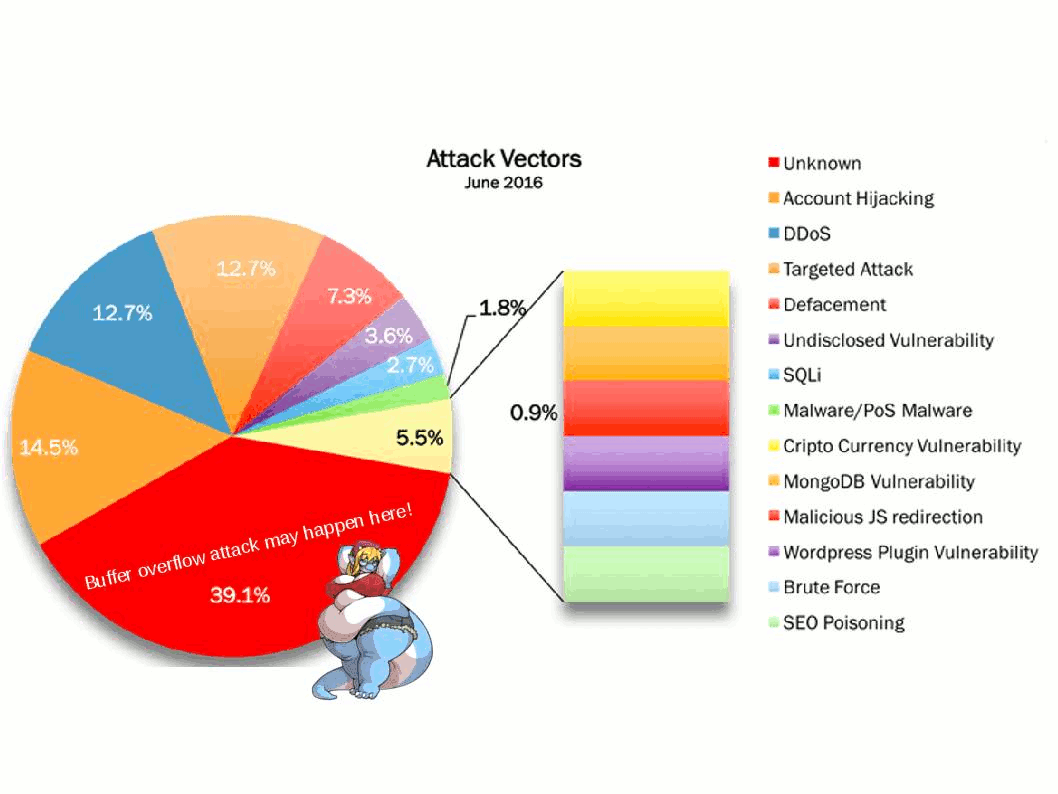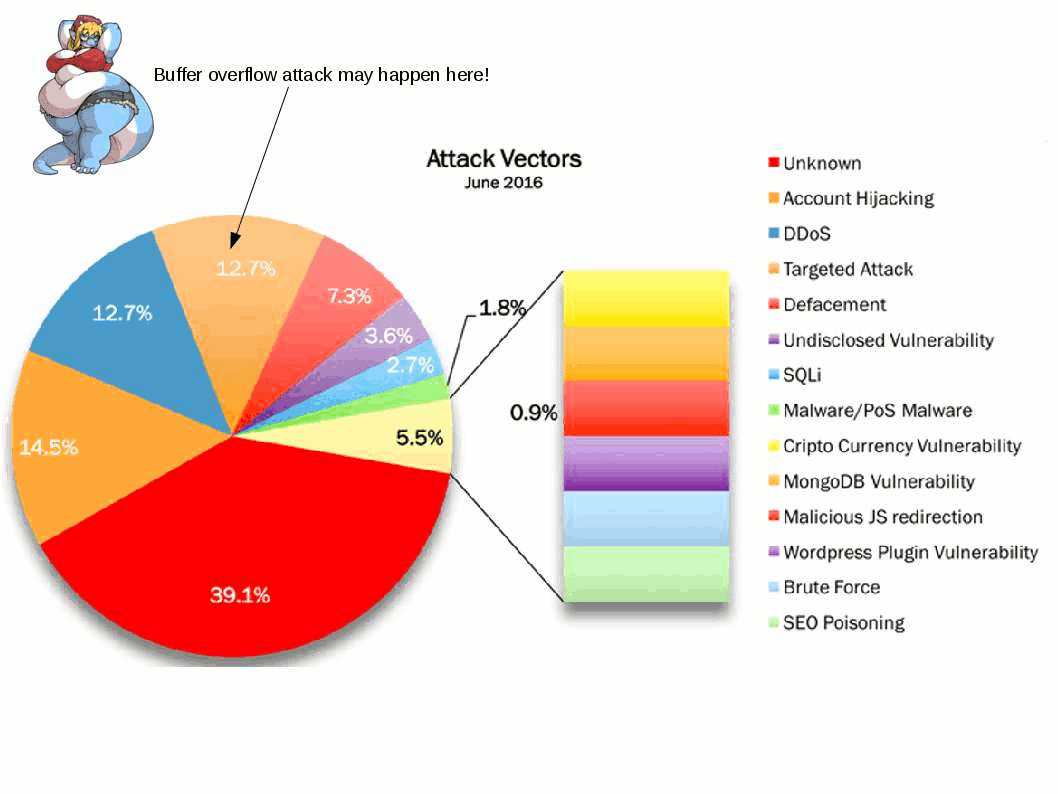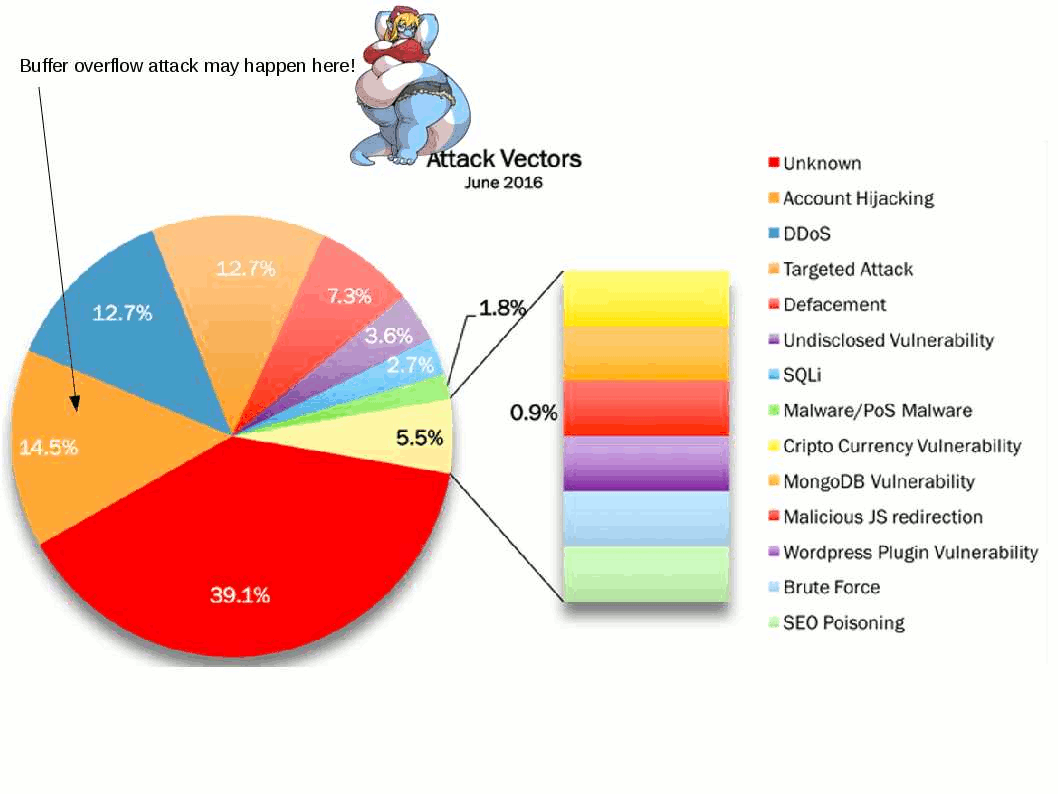
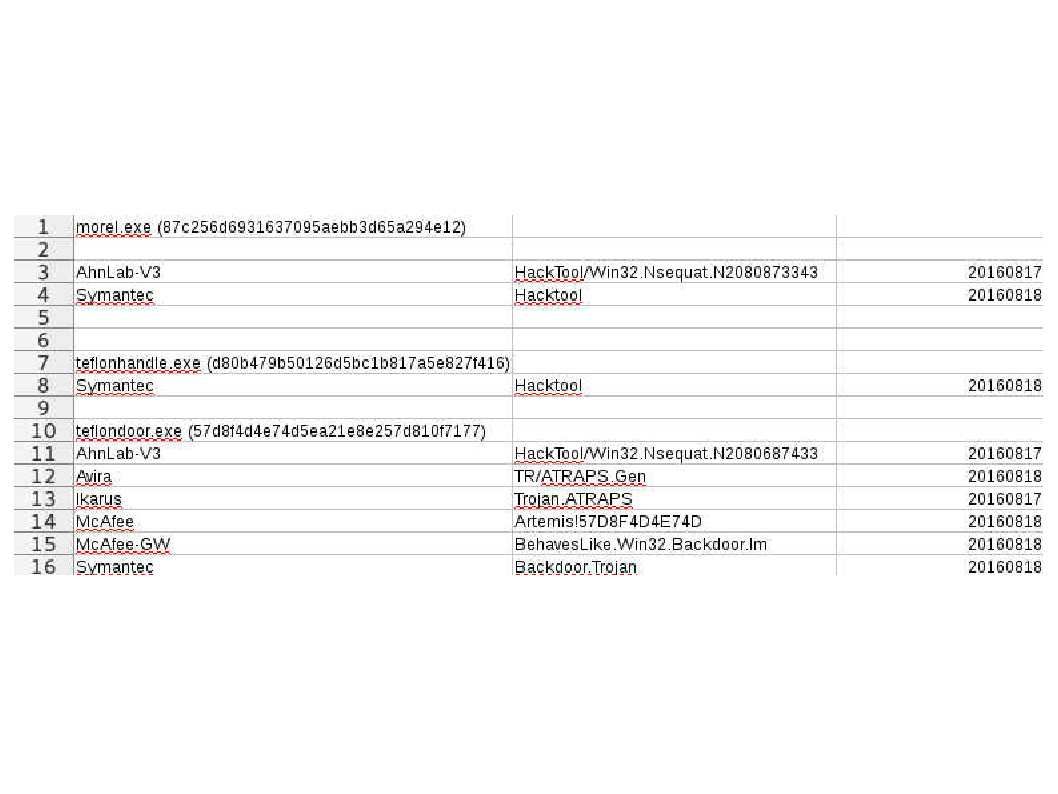
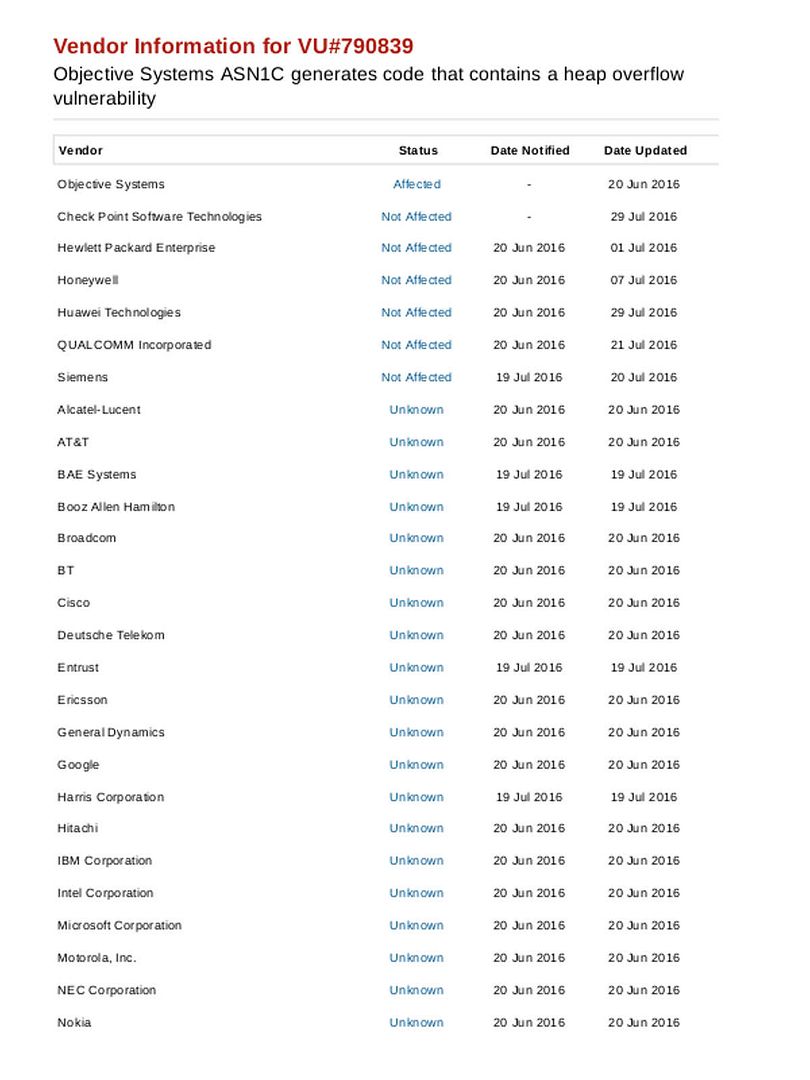
But how about the hackers? Hacker also have interest of these data which NSA does. I believed that below checklist details lure hacker interest.
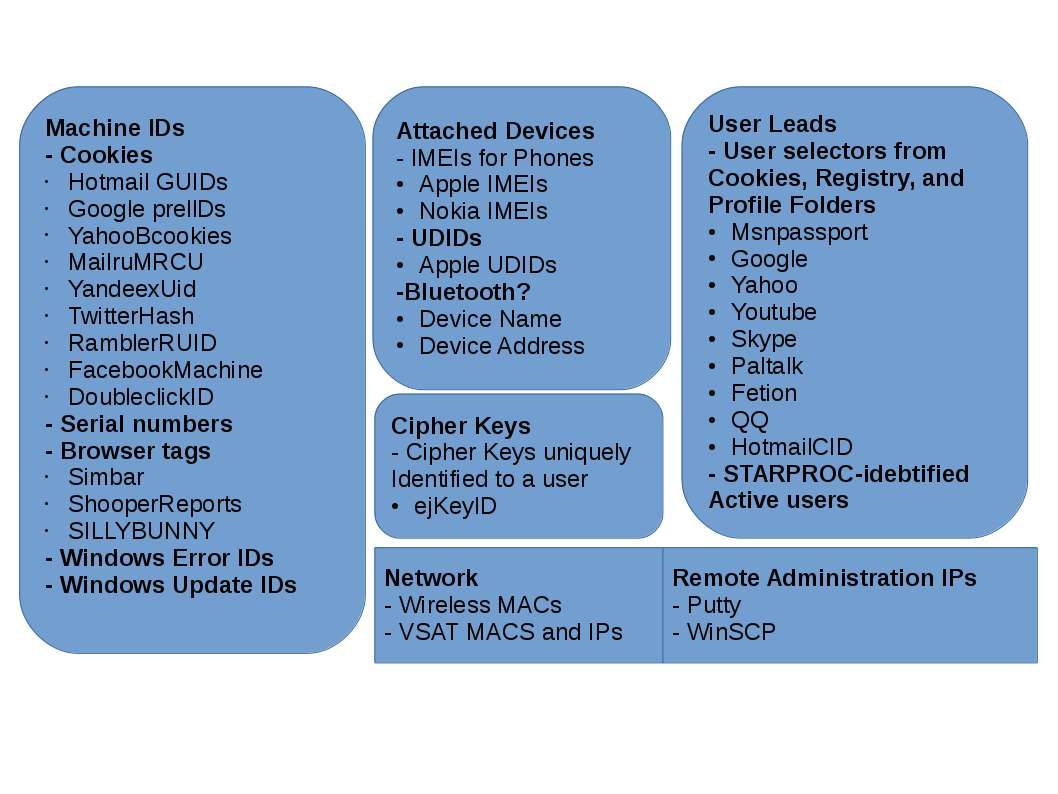
Internet application coding create a loophole make this cyber games become a never ending story.
Example:
- Email accounts or passwords using session cookies
- A common use for XSS is stealing cookies to hijack sessions and gain access to restrictedweb content
- When cookie doesn’t have Secure flag set, then it can be sent over insecure HTTP (provided that HSTS is not used; HSTS is described in the next section). When this is a case, the attacker controlling the communication channel between a browser and a server can read this cookie. If the cookie stores session ID, then disclosure of this cookie over insecure HTTP leads to user impersonation.
- When a cookie doesn’t have HttpOnly flag set, then JavaScript can read a value of this cookie. That’s why XSS attack leads to user impersonation if there is no HttpOnly flag set for a cookie with session ID. When a cookie has HttpOnly flag set, then attacker can’t read a value of the cookie in case of XSS attack. The problem is that access permissions are not clearly specified in RFC 6265. It turns out, that cookie with HttpOnly flag can be overwritten in Safari 8.
Short term conclusion:
No way because we are living on earth!