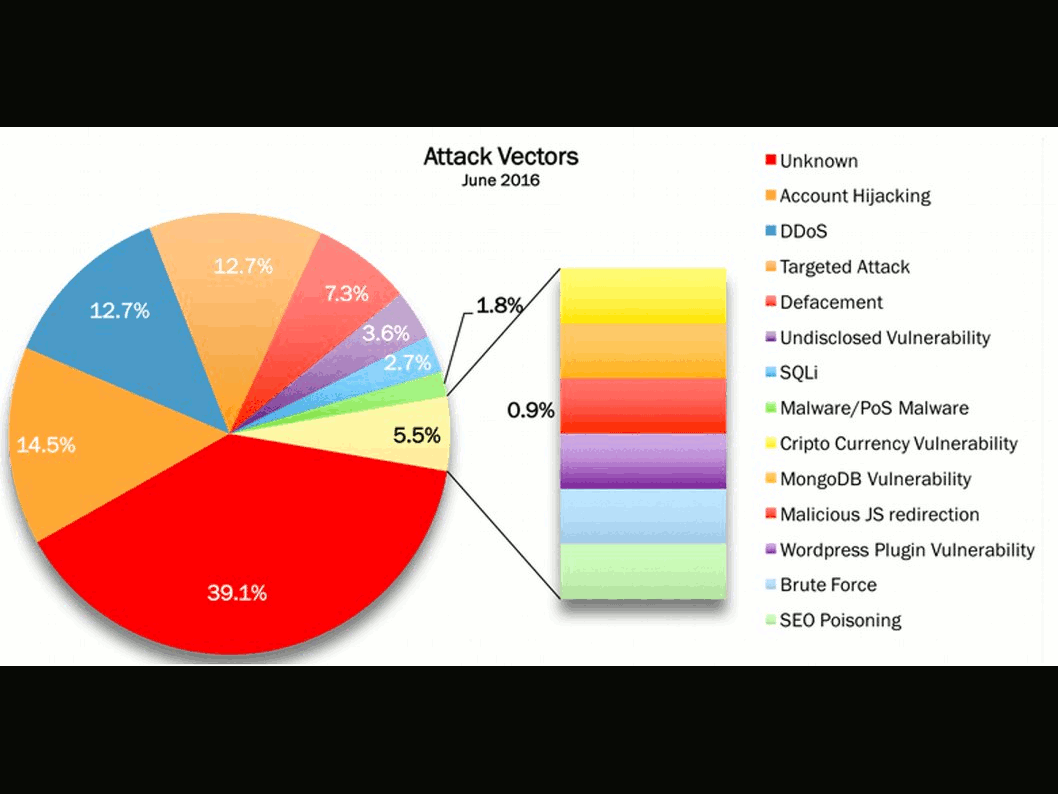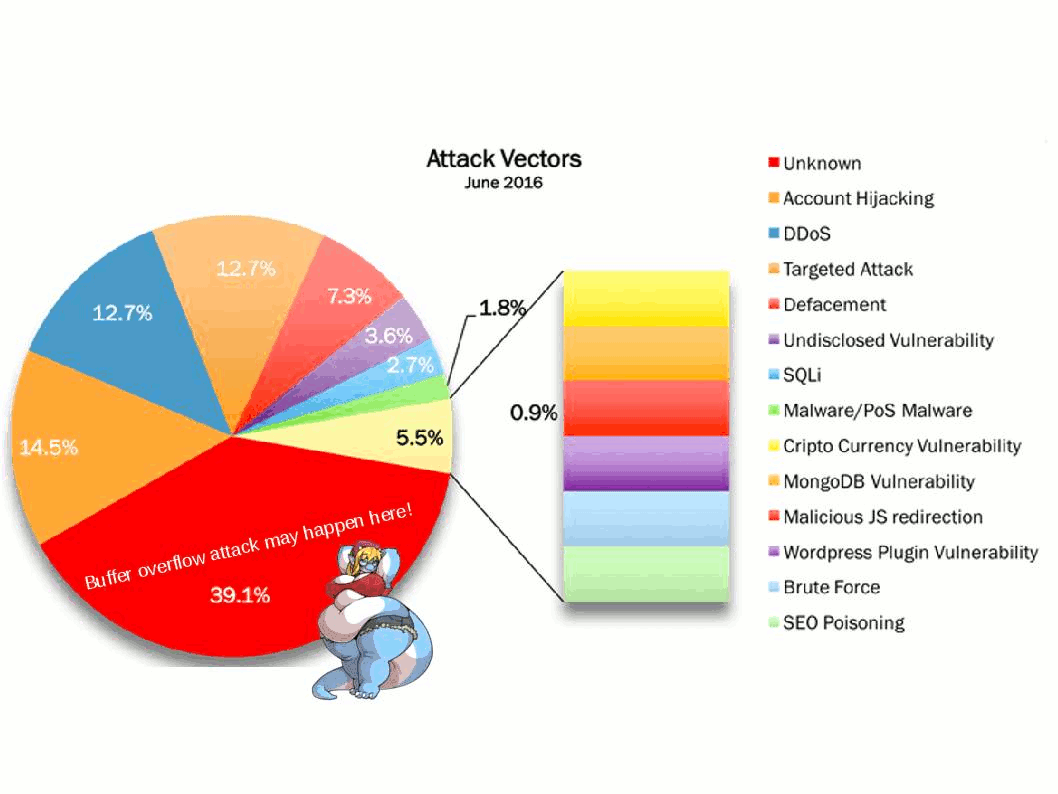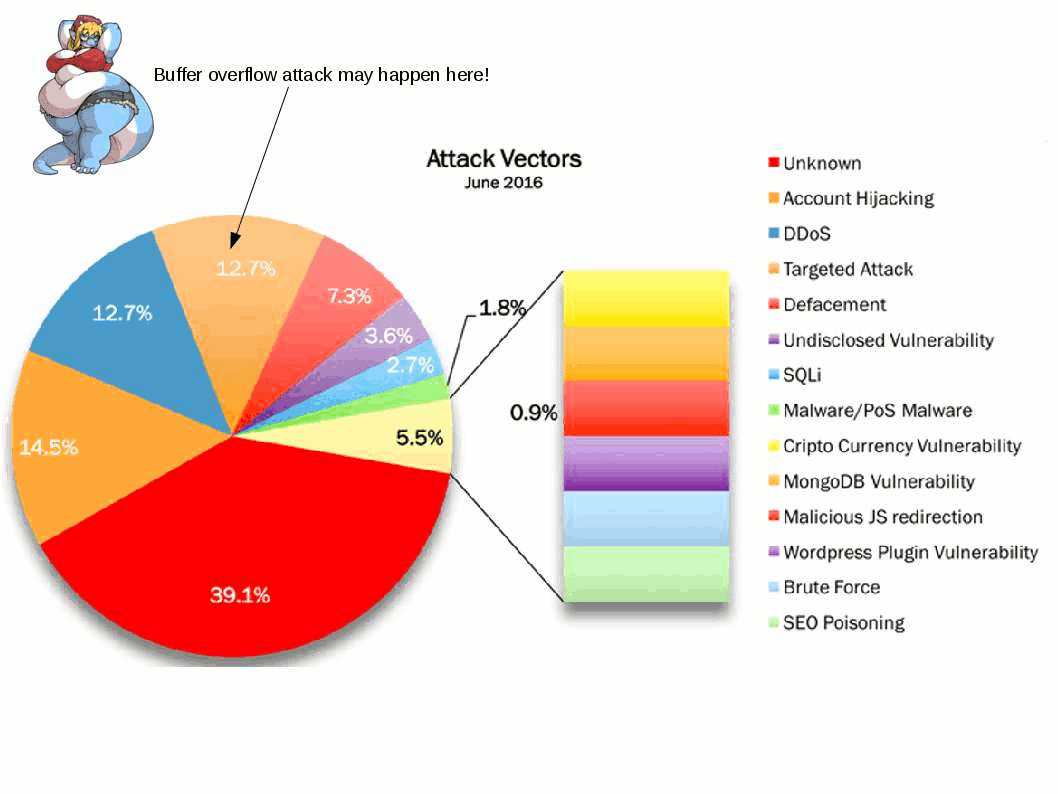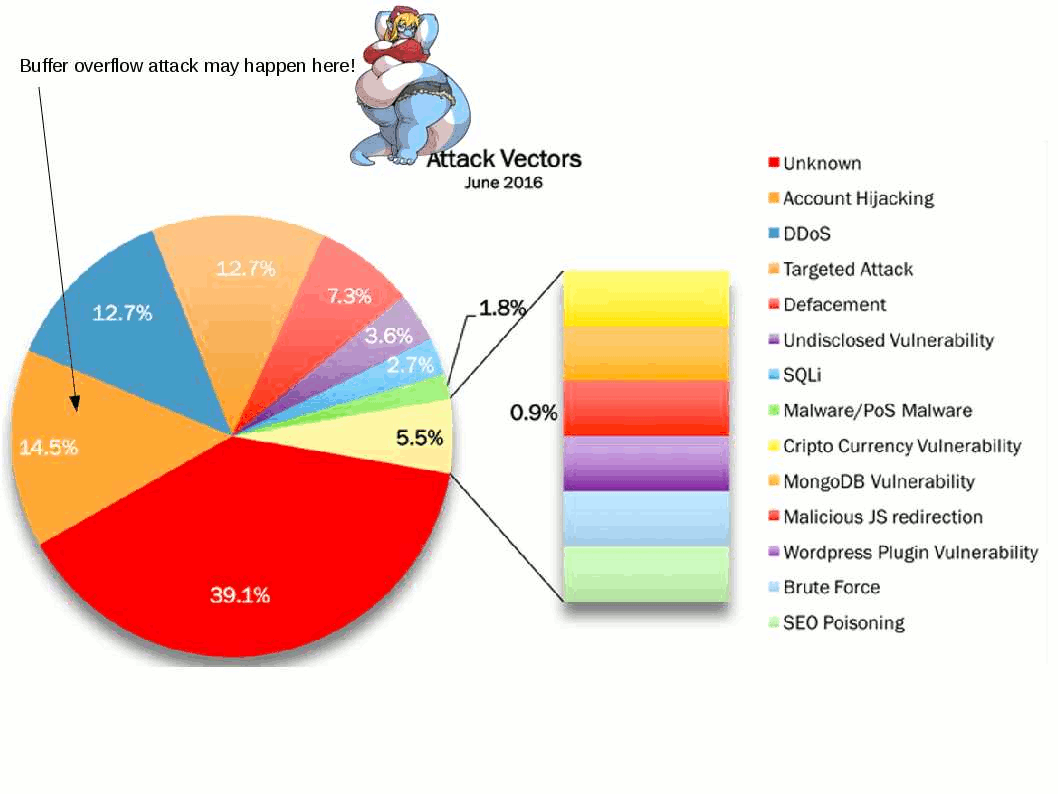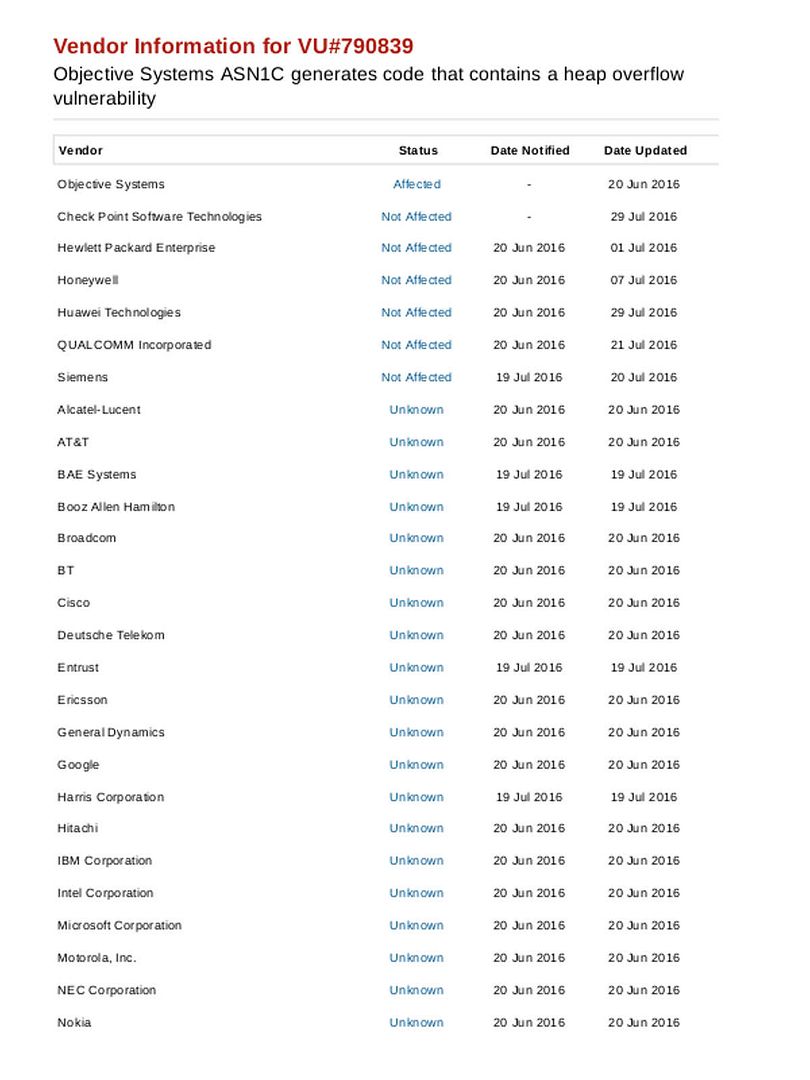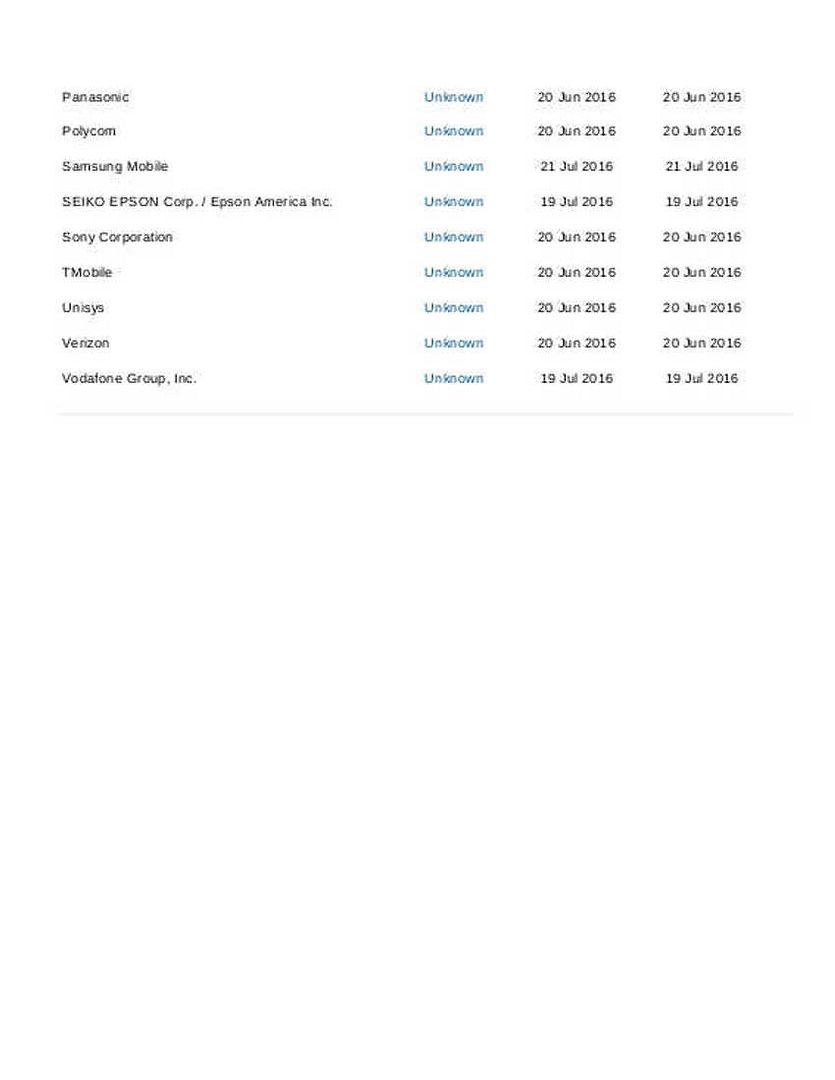
Headline news alert that malware embedded to picture file boil up hijack storm to android world. Sound horrible! No need involve phishing technique lure victim engage click url action and such a way compromise your android phone. No safe world! The vulnerability (CVE-2016-3862) fix immediately. Resolution is that enforce IPC Router to check if the port is a client port before binding it as a control port. Security Guru might alerts that critical vulnerabilities found this year are similar. The design ignore the verification check. Quote an example, a vulnerability (CVE-2016-0817) in the Simple Network Management Protocol (SNMP) code of Cisco Adaptive Security Appliance (ASA) Software could allow an unauthenticated, remote attacker to cause a reload of the affected system or to remotely execute code. The vulnerability is due to a buffer overflow in the affected code area. Yes, the device allow anyone send SNMP packet (OSI 5 – 7 layers) is the fundamental design. But the design concept not including someone is going to fool him. Is it a flaw? But SNMP protocol contains technical weakness originally! SNMP design flaw not on our discussion this time. We jump to a more critical topic. Yes, it is the buffer overflow attack. I claimed that this is the 2nd stricken region of cyber attack vector.
Heads-up (Quick and Dirty):
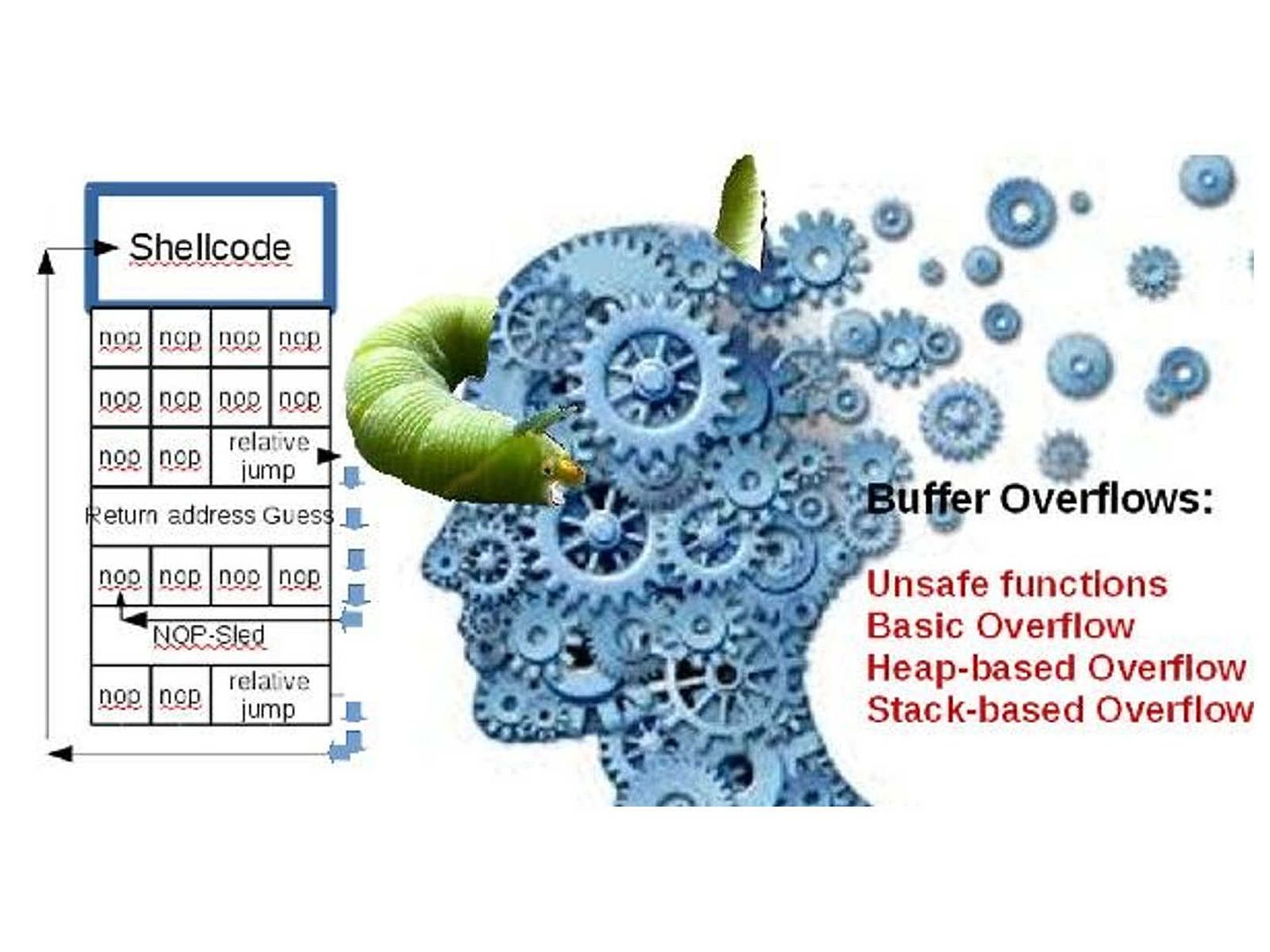
Unsafe functions buffer overflow
Buffer overflows, both on the stack and on the heap, are a major source of security vulnerabilities in C, Objective-C, and C++ code.When the input data is longer than will fit in the reserved space, if you do not truncate it, that data will overwrite other data in memory. If the overwritten data includes the address of other code to be executed and the user has done this deliberately, the user can point to malicious code that your program will then execute.
Basic buffer overflow attack
NOP-sled is a quite common shellcode preamble used in memory corruption attacks to increase the probability of successful target exploitation. The attackers usually prepend their machine language code with a large amount of No Operation (NOP) instructions. Most CPUs have one or more NOP instruction types, which tell the processor to do nothing for a single clock cycle. The attacks consist on making the program jump into an specific address and continue running from there. By looking at the program and its output, attacker can write the address of bar into the return address. The step is that overwrite return address so that code execution jumps into the input given by attacker.
Heap-based overflow
The heap is the memory area where you can allocate memory during the execution of a binary. Heap attacks are typically harder to perform than a Stack based attack.
i. Overwrite pointer – A pointer points to valid executed code. But the attacker corrupting the pointer and put the malware function replace the valid executed code. A remote attacker may exploit this issue to execute arbitrary code within the context of the affected application.
Stack-based overflow
It affects any function that copies input to memory without doing bounds checking. If the source data size is larger than the destination buffer size. The data will go to high address and overflow previous data on stack. The attacker could use to execute arbitrary code with elevated privileges or cause a DoS condition.
Buffer overflow attack may appear everywhere in cyber world today. Any weakness of system and application design will lure the interest by hacker. IT Guru don’t ignore this channel.