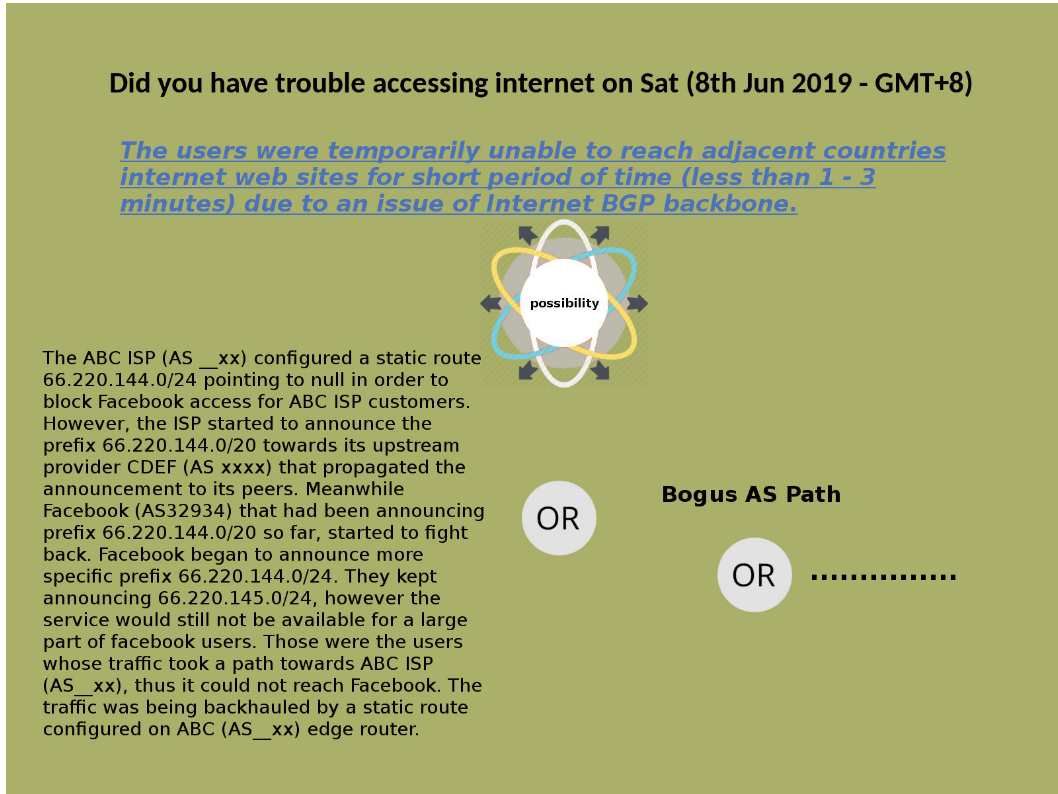
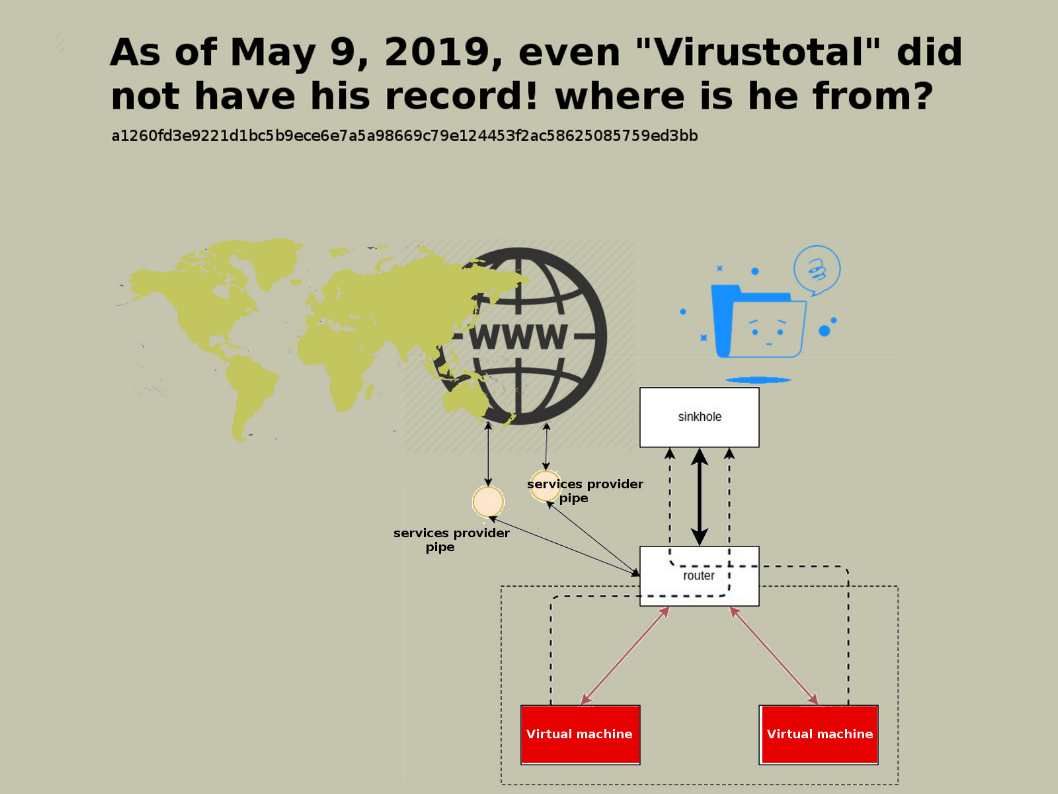
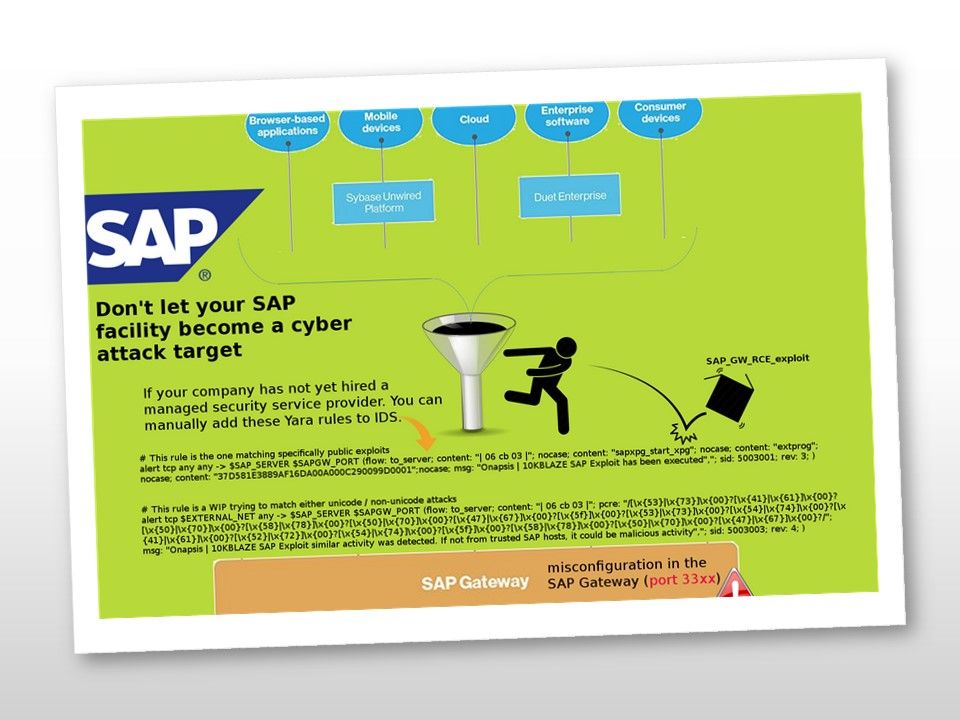
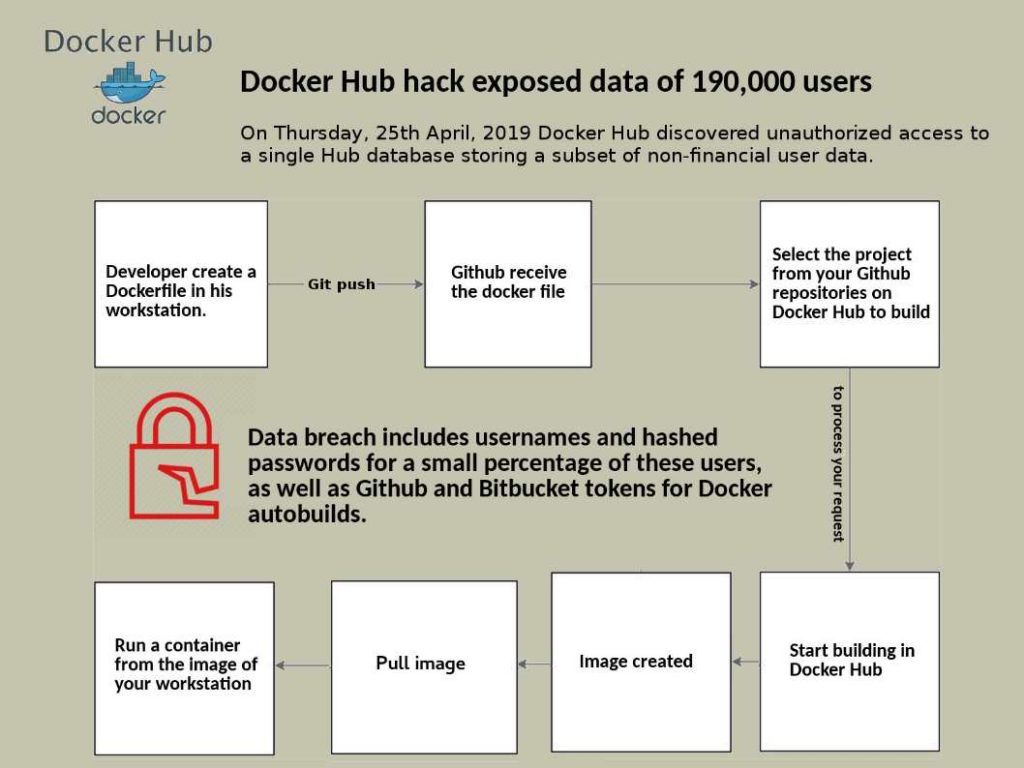
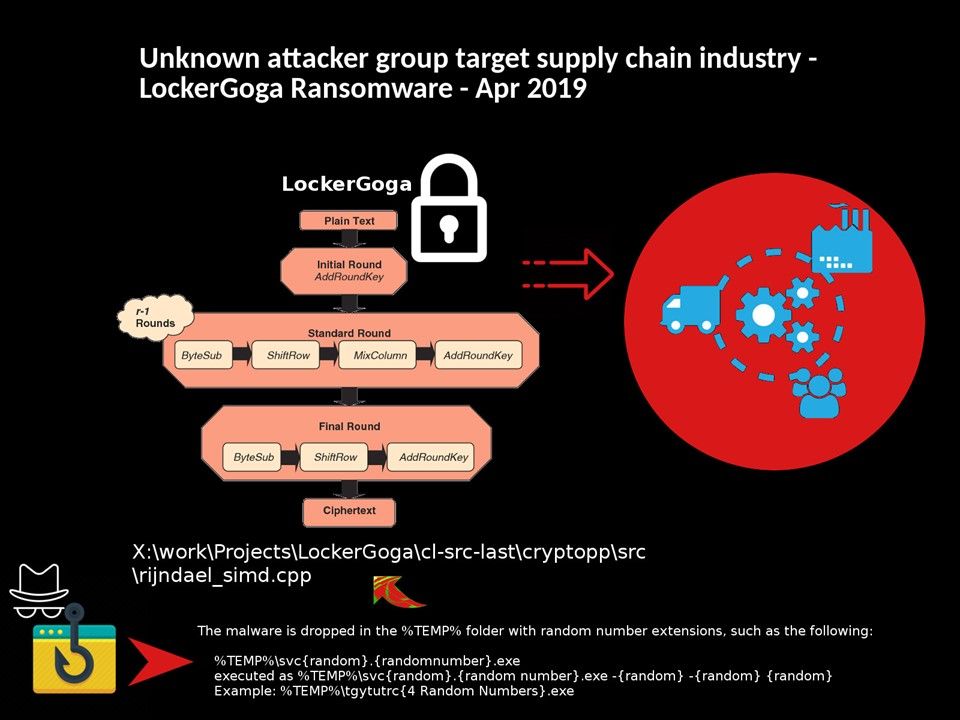
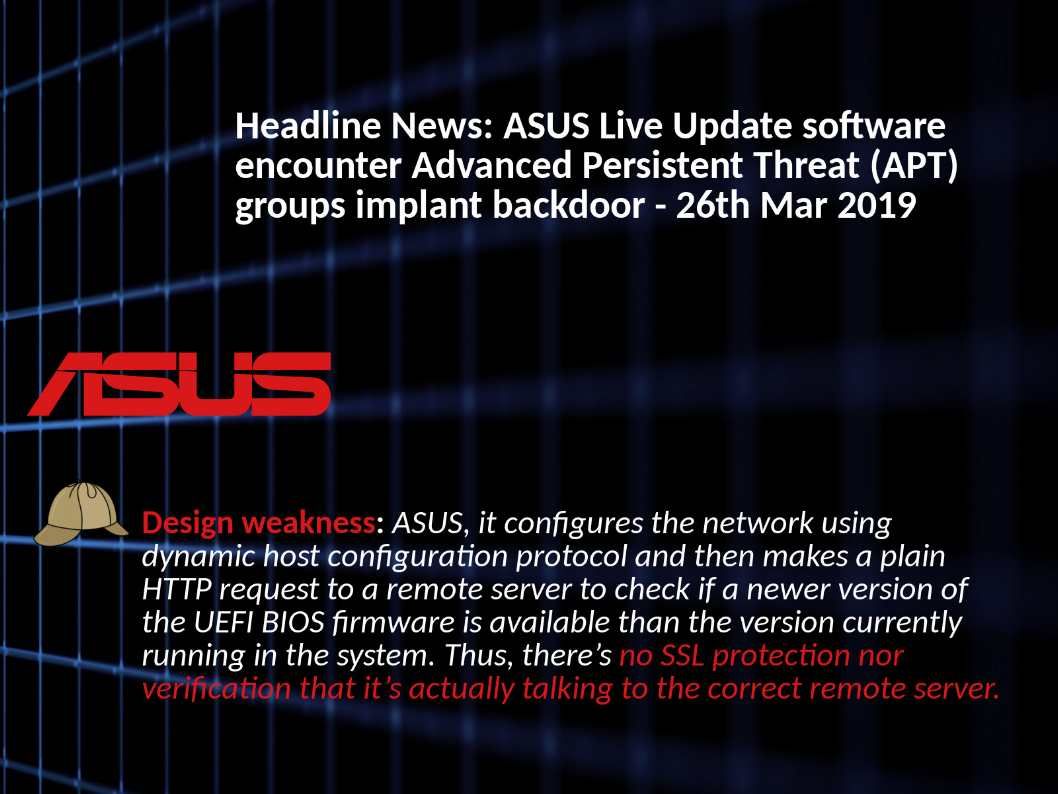
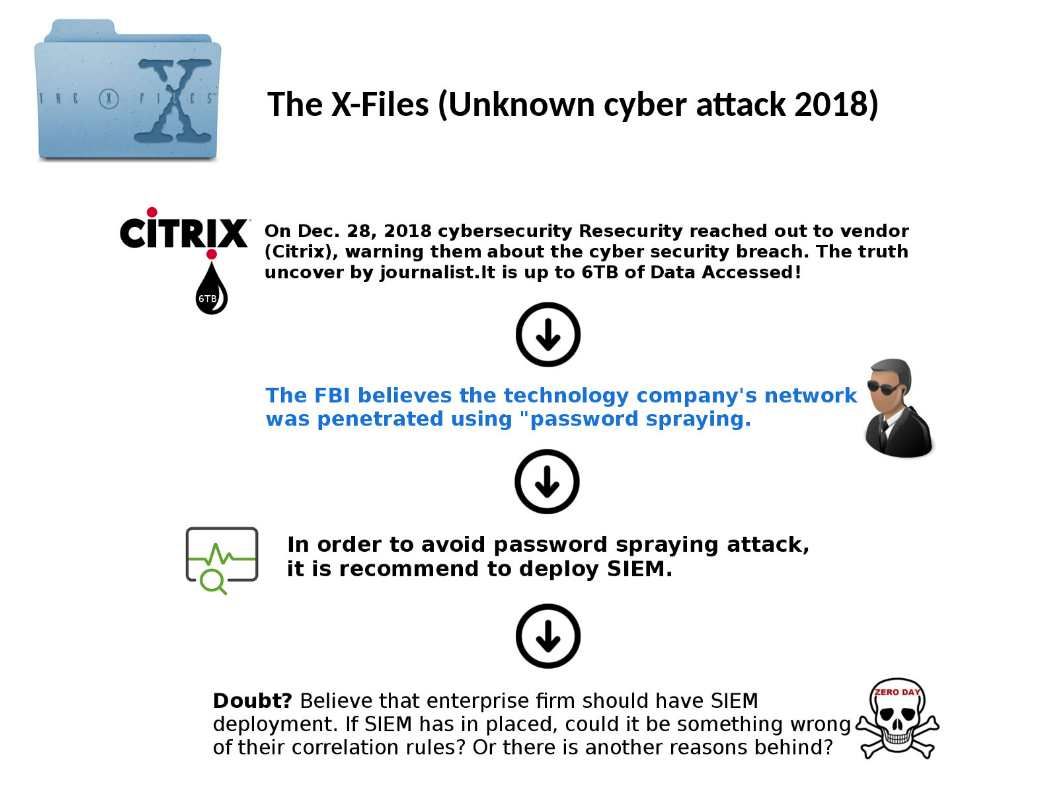
Preface: Exim is growing in popularity because it is open source.
Background:It’s the default mail transport agent installed on some Linux systems.It contain feature likes:
Lookups in LDAP servers, MySQL and PostgreSQL databases, and NIS or NIS+ services.
Vulnerability details: The vulnerability was patched in Exim 4.92, released on February 10, 2019. The vulnerable code is in “deliver_message()”. A vulnerability exists because the email address in the deliver_message() function in /src/deliver.c is not fully validated. So local attackers simply send emails to “${run{…}}@localhost”. Since “localhost” is a local domain of Exim) and execute as root (system privileges).
Remark: Deliver_drop_privilege is set to false by default.
Attack synopsis: If the “verify = recipient” ACL is manually deleted then remote attack will be occurred. Attacker can reuse our local-exploitation method with an RCPT TO “xxx+${run{…}} @ localhost”. Where “xxx” is the name of the local user .
For official details, please click on the link – https://www.exim.org/static/doc/security/CVE-2019-10149.txt