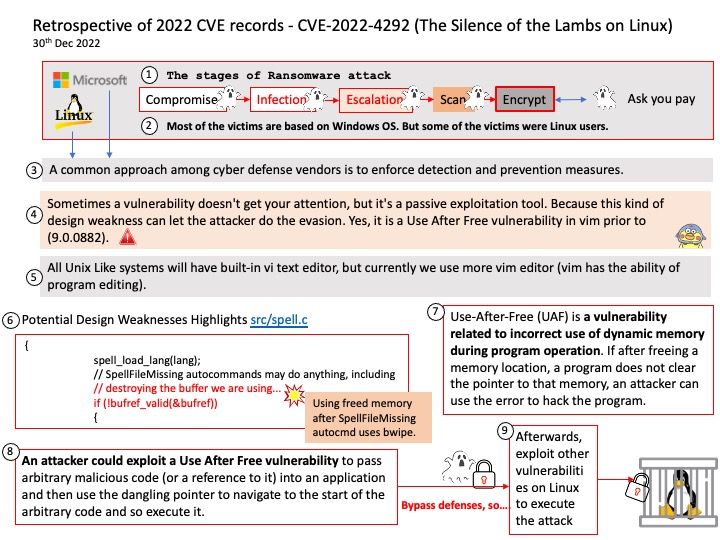
Preface: Use-After-Free (UAF) is a vulnerability related to incorrect use of dynamic memory during program operation. If after freeing a memory location, a program does not clear the pointer to that memory, an attacker can use the error to hack the program.
Background: Most of the victims are based on Windows OS. But some of the victims were Linux users. A common approach among cyber defense vendors is to enforce detection and prevention measures.
Sometimes a vulnerability doesn’t get your attention, but it’s a passive exploitation tool. Because this kind of design weakness can let the attacker do the evasion. Yes, it is a Use After Free vulnerability in vim (prior to 9.0.0882).
All Unix Like systems will have built-in vi text editor, but currently we use more vim editor (vim has the ability of program editing).
Vulnerability details: Use After Free in GitHub repository vim/vim prior to 9.0.0882. For details, see the link – https://nvd.nist.gov/vuln/detail/CVE-2022-4292
Observation: An attacker could exploit a Use After Free vulnerability to pass arbitrary malicious code (or a reference to it) into an application and then use the dangling pointer to navigate to the start of the arbitrary code and so execute it.
Afterwards, exploit other vulnerabilities on Linux to execute the attack.
As there is currently no such exploit. But my point is that Linux users and environments should be aware of this small vulnerability. Do not despise this power.
Mitigation – Untrusted vim scripts with -s [scriptin] are not recommended to run.