Preface: The state in Redux is stored in memory. This means that, if you refresh the page the state gets wiped out. The state in redux is just a variable that persists in memory because it is referenced by all redux functions.
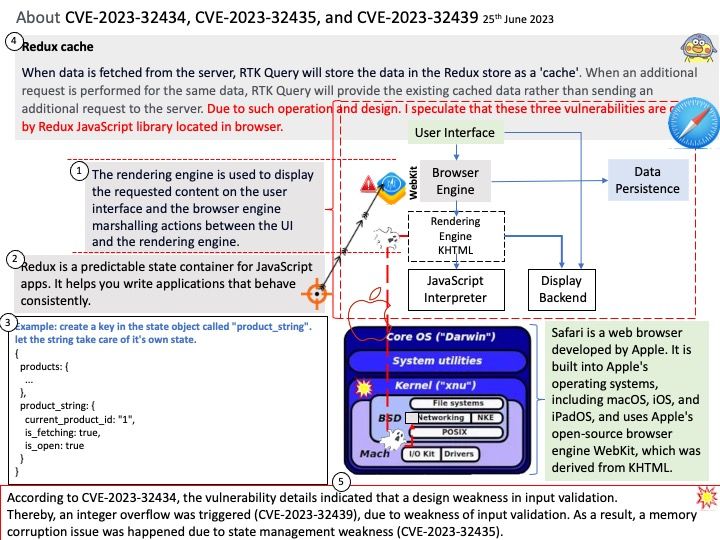
Background: Safari is a web browser developed by Apple. It is built into Apple’s operating systems, including macOS, iOS, and iPadOS, and uses Apple’s open-source browser engine WebKit, which was derived from KHTML.
The rendering engine is used to display the requested content on the user interface and the browser engine marshalling actions between the UI and the rendering engine.
Redux is a predictable state container for JavaScript apps. It helps you write applications that behave consistently.
Refer to my speculation (see attached picture). Due to such operation and design. I speculate that these three vulnerabilities are caused by Redux JavaScript library located in browser.
Vulnerability details:
According to CVE-2023-32434, the vulnerability details indicated that a design weakness in input validation.
Thereby, an integer overflow was triggered (CVE-2023-32439), due to weakness of input validation. As a result, a memory corruption issue was happened due to state management weakness (CVE-2023-32435).
https://nvd.nist.gov/vuln/detail/CVE-2023-32434
https://nvd.nist.gov/vuln/detail/CVE-2023-32435
https://nvd.nist.gov/vuln/detail/CVE-2023-32439