Preface: Why do I say on behalf of the Linux kernel that it takes time to adjust. If you recall, last year (December 2022), a flaw was found in fib6_rule_suppress() that would crash the kernel. According to the RedHat knowledge base, a resolution is in the works. That’s why I mentioned. Perhaps the website not update the status yet. However there is another new flaw relate to fib6_rule_suppress( ) was found.
Background: Linux kernel has had IPv6 support since 1996. So, you must compile the Linux kernel with IPv6 networking support.
When the IPv6 is in enabled state is set to 0 else it is 1:
cat /sys/module/ipv6/parameters/disable
IPv6 uses the same data struct for both control plane (FIB entries) and
data path (dst entries). This struct has elements needed for both paths
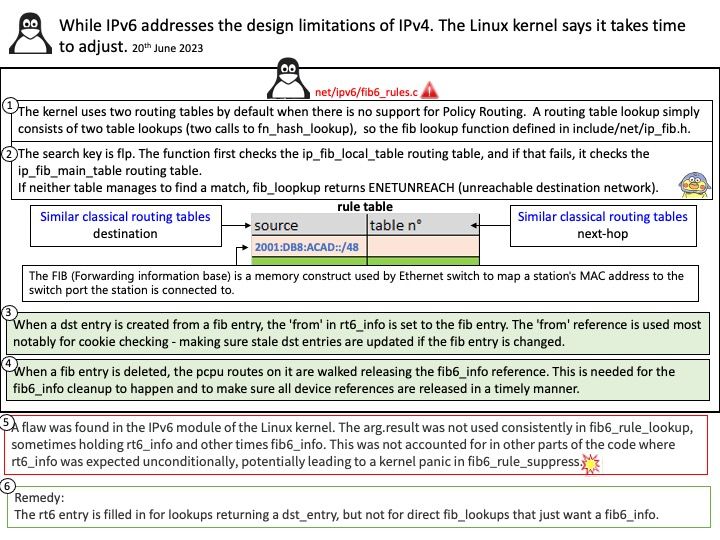
adding memory overhead and complexity (taking a dst hold in most places but an additional reference on rt6i_ref in a few). Furthermore, because of the dst_alloc tie, all FIB entries are allocated with GFP_ATOMIC (Used to allocate memory from interrupt handlers and other code outside of a process context).to improve the scalability of the IPv6 code. It include:
Allow FIB lookups without generating a dst (e.g., most rt6_lookup users just want to verify the egress device). Means moving dst allocation to the other side of fib6_rule_lookup which again aligns with IPv4 behavior.
Vulnerability details: A flaw in the Linux Kernel found. If IPV6 being used in the way that some specific networking local rule enabled and both IPV6 being used, then it can lead to Kernel crash with the message “fib6_rule_suppress+0x22”. It happens when receiving some networking packet to the local IPV6 address that matches this specific rule.
Official announcement: For details, please refer to the link – https://nvd.nist.gov/vuln/detail/CVE-2023-3022