Preface: Information security driven role base access control. But when cloud service provider design or implement access control. It will be sophisticated. If access control include virtual machine technology under hierarchical structure. In order to harden the effectiveness of the control.
Cloud resources are organised hierarchically, where the organisation node is the root node in the hierarchy, the projects are the children of the organisation, and the other resources are descendants of projects. You can set allow policies at different levels of the resource hierarchy.
Background: Secure computing mode (seccomp) is a Linux kernel feature. You can use it to restrict the actions available within the container.
The seccomp() system call operates on the seccomp state of the calling process.
You can use this feature to restrict your application’s access.
This feature is available only if Docker has been built with seccomp and the kernel is configured with CONFIG_SECCOMP enabled.
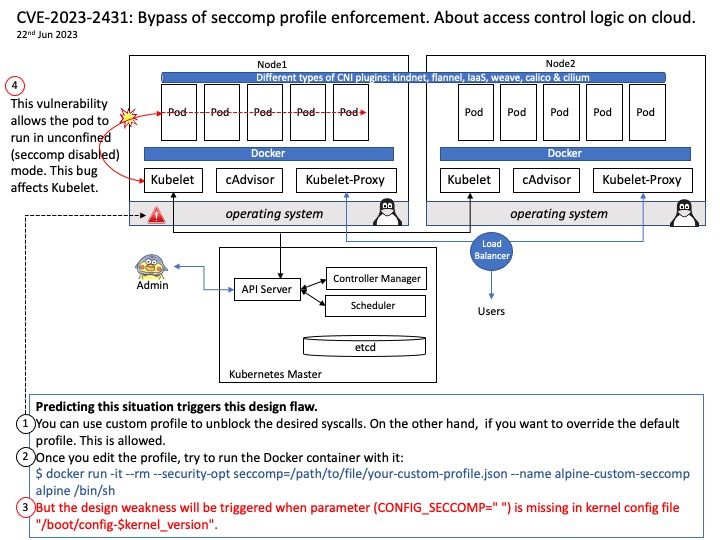
Vulnerability details: A security issue was discovered in Kubelet that allows pods to bypass the seccomp profile enforcement. Pods that use localhost type for seccomp profile but specify an empty profile field, are affected by this issue. In this scenario, this vulnerability allows the pod to run in unconfined (seccomp disabled) mode. This bug affects Kubelet.
Official details: For details, please refer to the link – https://nvd.nist.gov/vuln/detail/CVE-2023-2431