Preface: VMware published multiple vulnerabilities on 22nd June 2023. It make the reader dazzled. Since the actual attack exploit technique did not released by VMware.
However they told vulnerability caused by DCEPRC. So, let us take a closer look of DCEPRC protocol. See whether it will lure your interest?
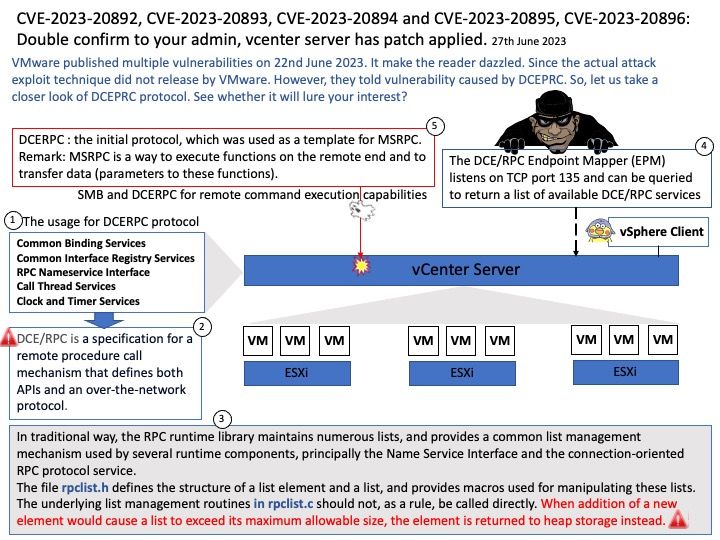
Background: (DCERPC) Distributed Computing Environment / Remote Procedure Calls, is the remote procedure call system developed for the Distributed Computing Environment (DCE) Networking. The usage of this protocol including Common Binding Services, Common Interface Registry Services, RPC Nameservice Interface, Call Thread Services, Clock and Timer Services,…
Remote Procedure Call (RPC) protocol is generally used to communicate between processes on different workstations. However, RPC works just as well for communication between different processes on the same workstation.
Microsoft server technique also based on RPC technique. RPC uses the client and server model. Bruce Jay Nelson is generally credited with coining the term “remote procedure call” in 1981. Remote procedure calls used in modern operating systems trace their roots back to the RC 4000 multiprogramming system, which used a request-response communication protocol for process synchronization.
Some experts has concern of RPC. The reason is that there is no uniform standard for RPC; it can be implemented in a variety of ways.
In traditional way, the RPC runtime library maintains numerous lists, and provides a common list management mechanism used by several runtime components, principally the Name Service Interface and the connection-oriented RPC protocol service.
The file rpclist[.]h defines the structure of a list element and a list, and provides macros used for manipulating these lists. The underlying list management routines in rpclist[.]c should not, as a rule, be called directly. When addition of a new element would cause a list to exceed its maximum allowable size, the element is returned to heap storage instead.
Vulnerability details: Please refer below links for reference.
Advisory ID: VMSA-2023-0014
https://www.vmware.com/security/advisories/VMSA-2023-0014.html
Applying individual product updates to VMware Cloud Foundation environments using Async Patch Tool (AP Tool) (88287)
https://kb.vmware.com/s/article/88287