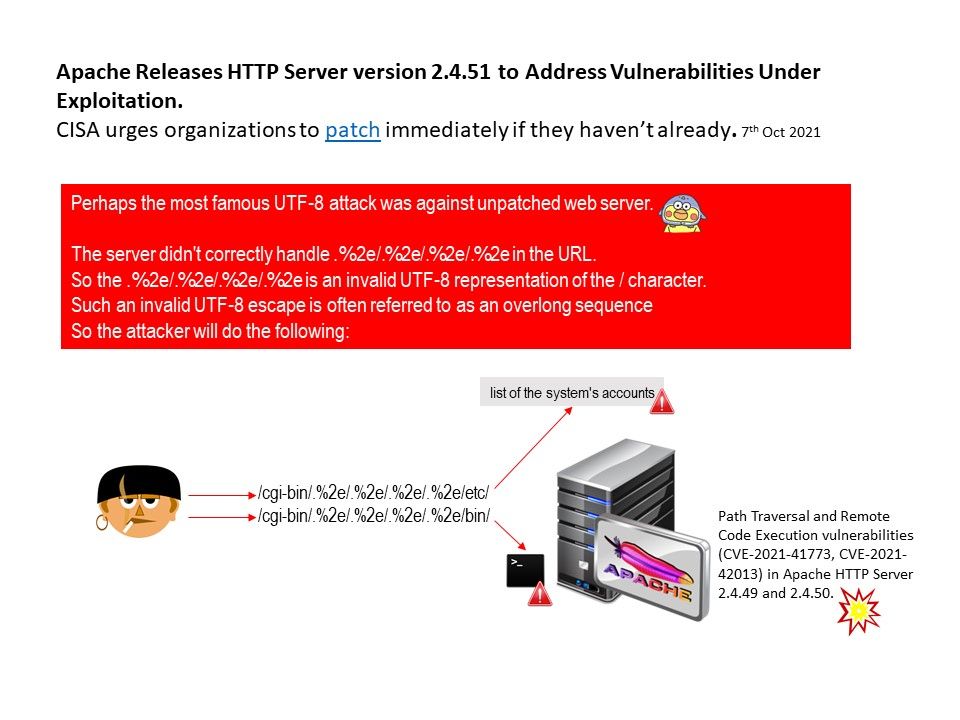
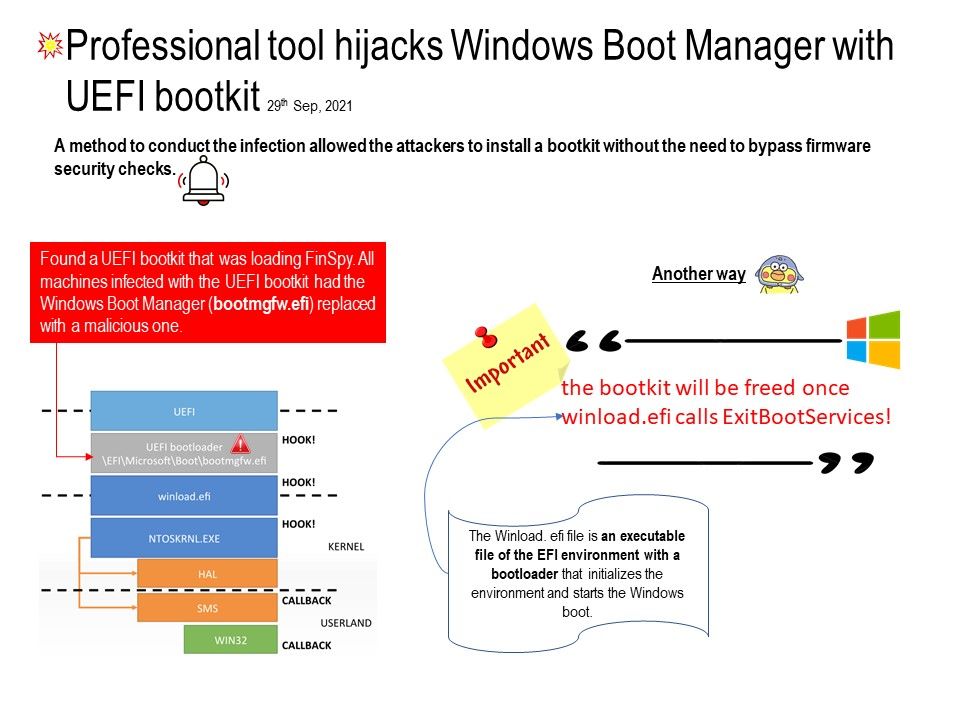
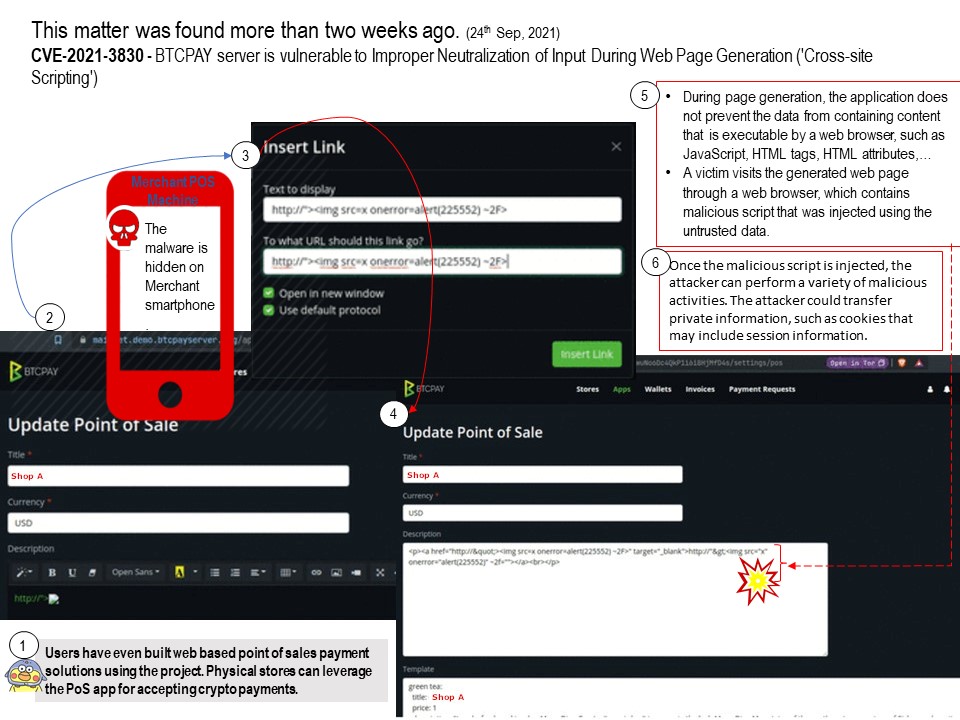
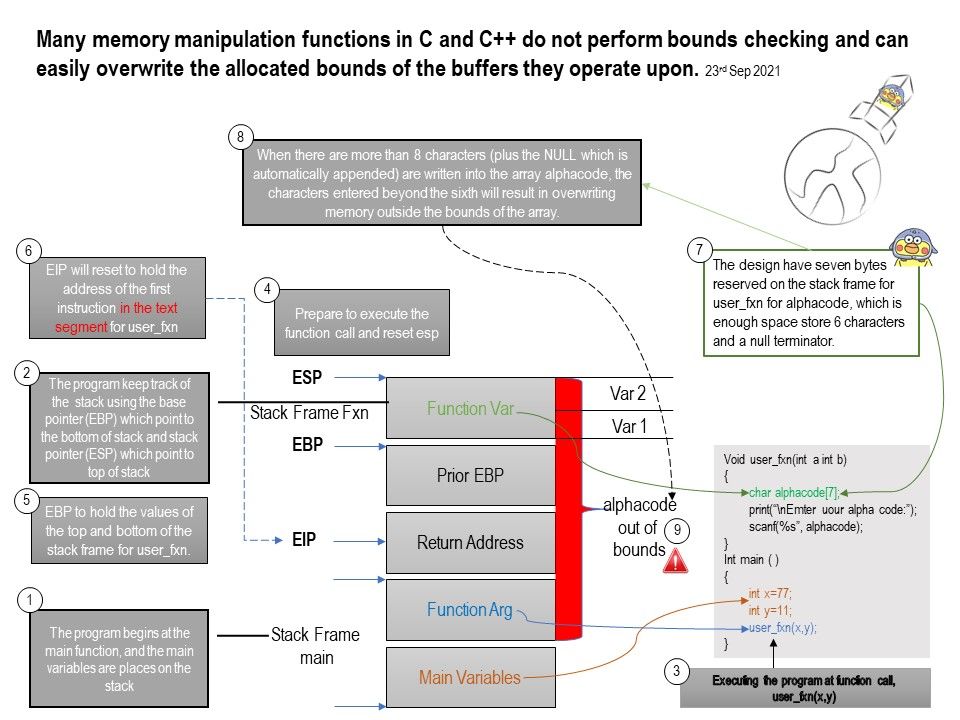
Preface: the most famous UTF-8 attack was against unpatched web server.
Background: The most common users of Apache HTTP Server are from Small Businesses and the Information Technology & Services industry. Perhaps
How to Check the Apache Version?
- Open terminal application on your Linux, Windows/WSL or macOS desktop.
- Login to remote server using the ssh command.
- To see Apache version on a Debian/Ubuntu Linux, run: apache2 -v.
- For CentOS/RHEL/Fedora Linux server, type command: httpd -v.
Vulnerability details: The server didn’t correctly handle contents in the URL. So the contain contained invalid UTF-8 representation of the [/] character. Such an invalid UTF-8 escape is often referred to as an overlong sequence. Therefore it provide an opportunity to the attacker. On 6th Oct,2021, Apache released Apache HTTP 2.4.50 to fix an actively exploited path traversal vulnerability in version 2.4.49 (tracked as CVE-2021-41773). This flaw allows threat actors to view the contents of files stored on a vulnerable server. Please refer to the official website for announcements – https://httpd.apache.org/security/vulnerabilities_24.html#CVE-2021-42013
.jpg)

.jpg)