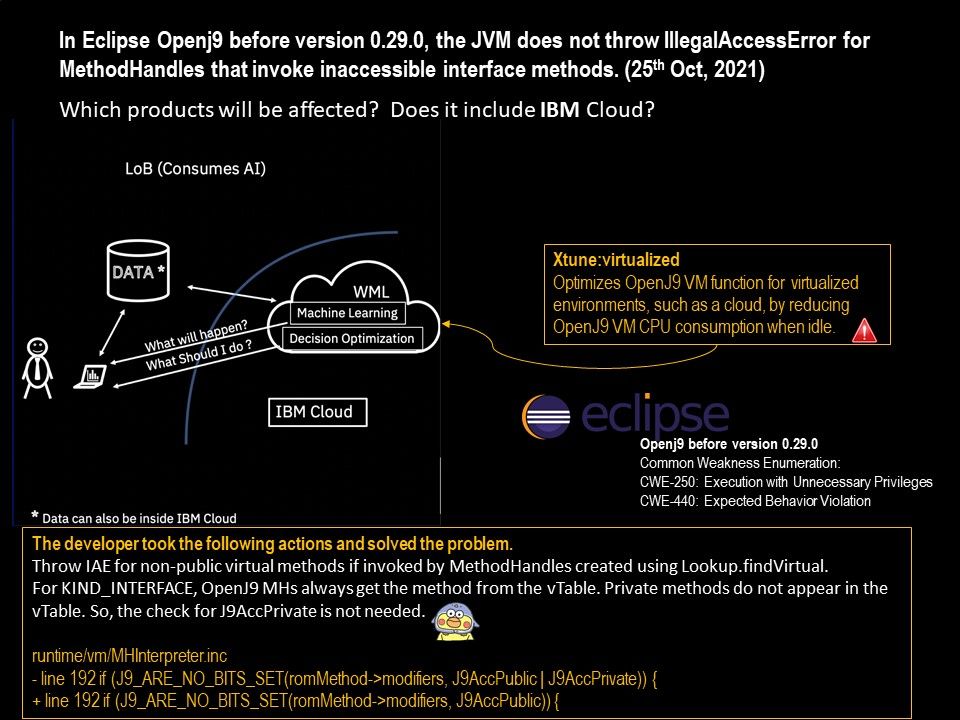
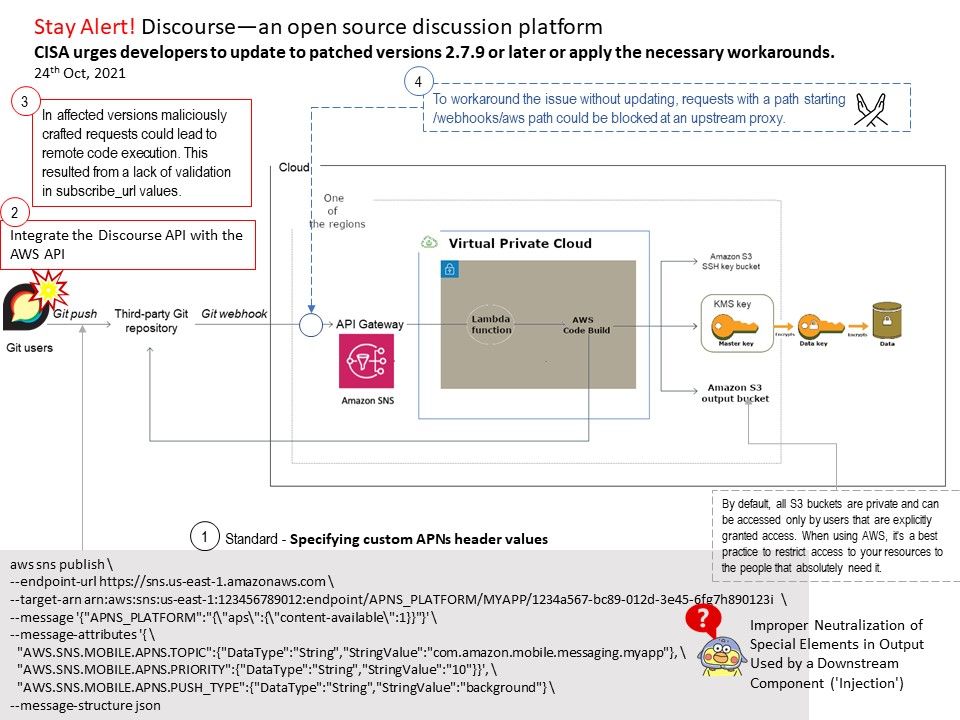
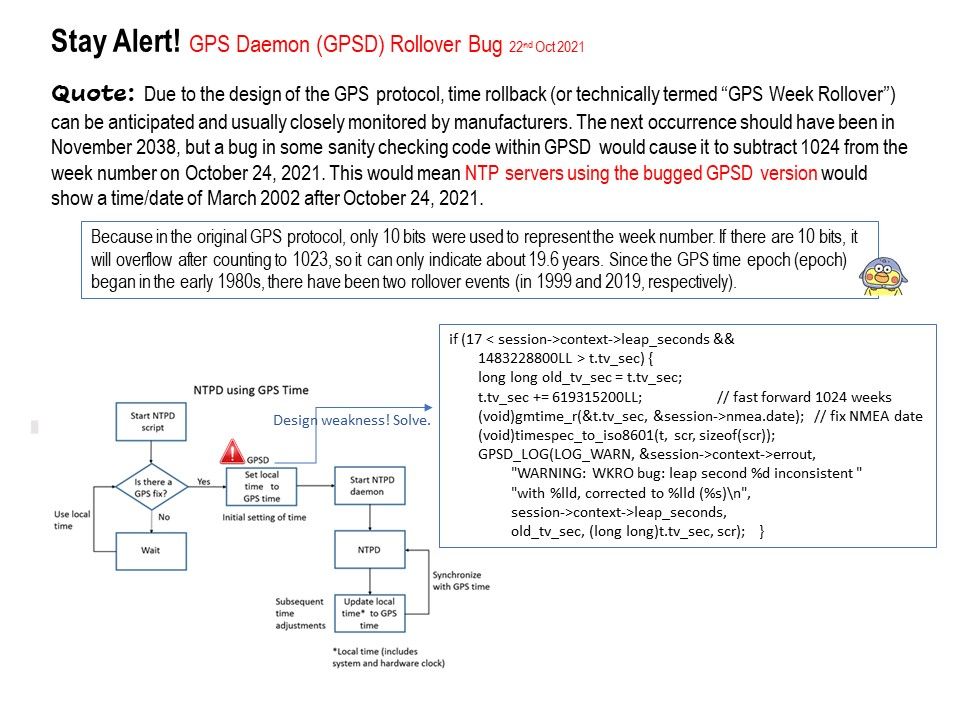
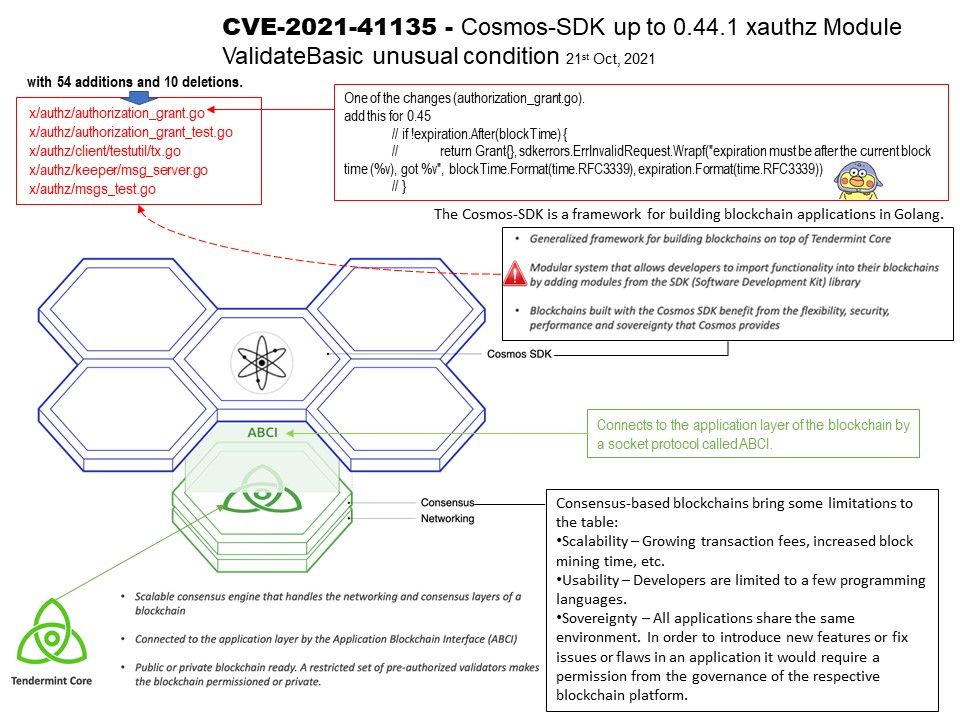
.jpg)
Preface: Android garbage collection is an automatic process which removes unused objects from memory. However, frequent garbage collection consumes a lot of CPU, and it will also pause the app.
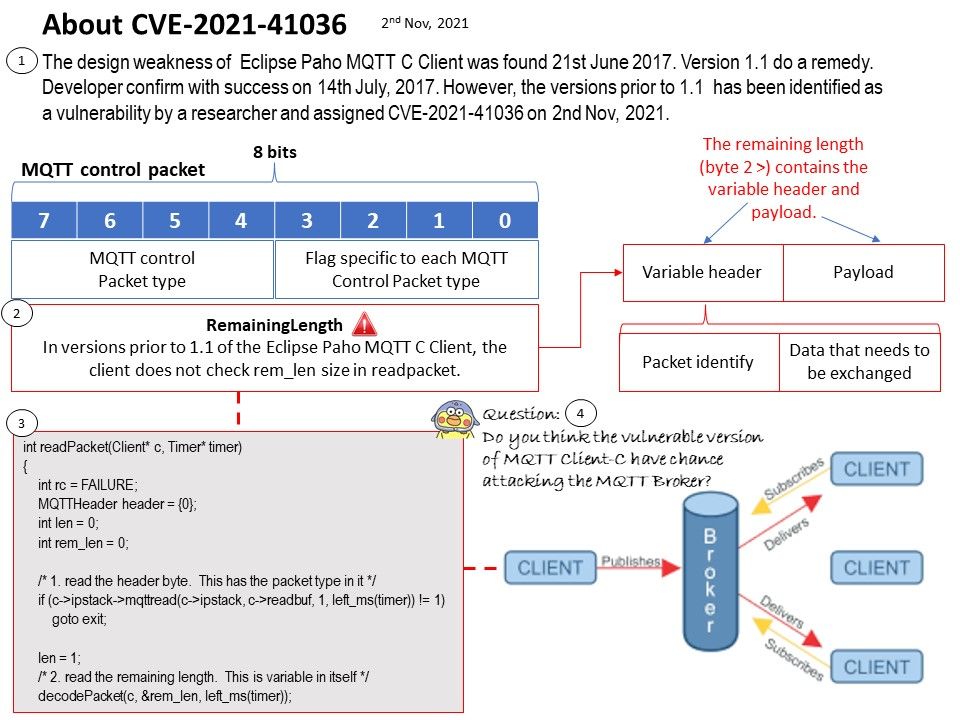
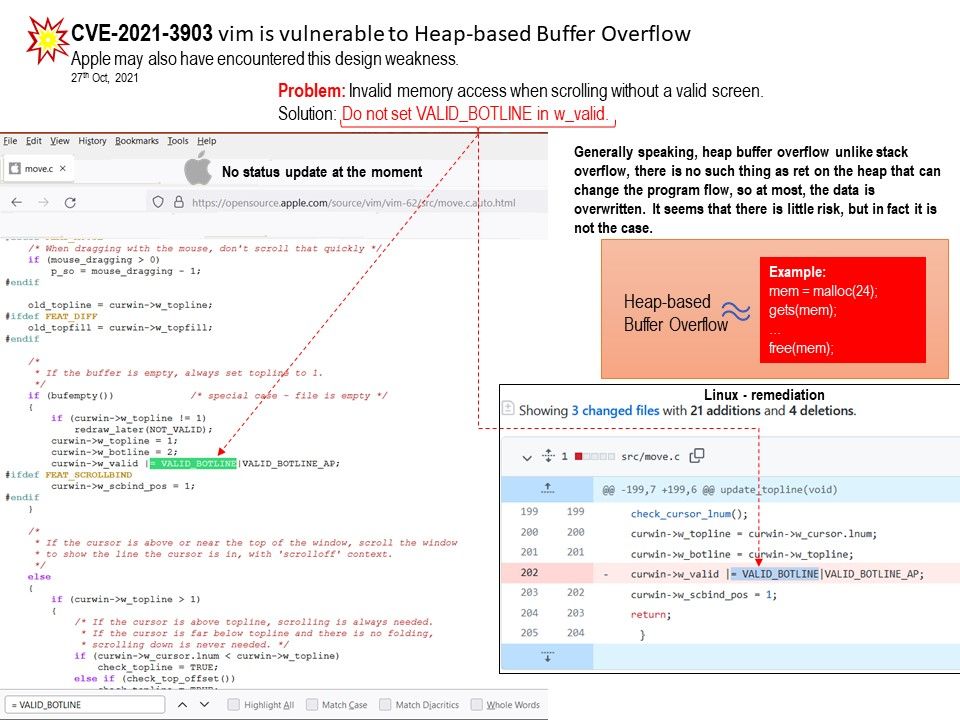
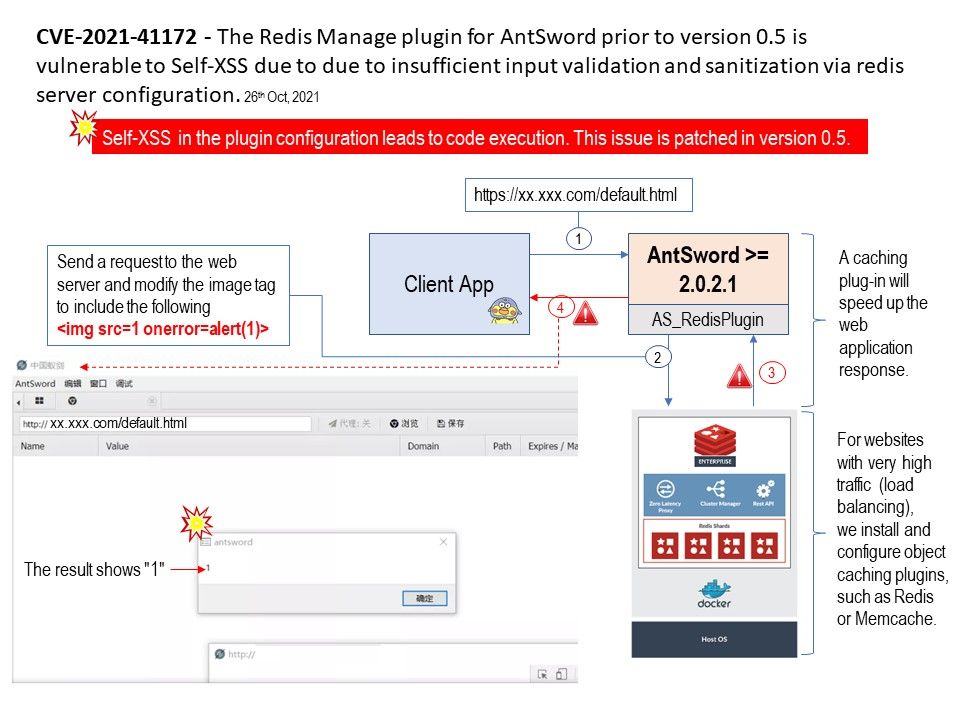
Background: The garbage collection of Unix sockets first selects a set of candidate sockets that are only referenced from the flight (total_refs == inflight_refs). This condition is checked and marked once during the candidate collection phase. Although inflight_refs is protected by unix_gc_lock, total_refs (file count) is not protected.
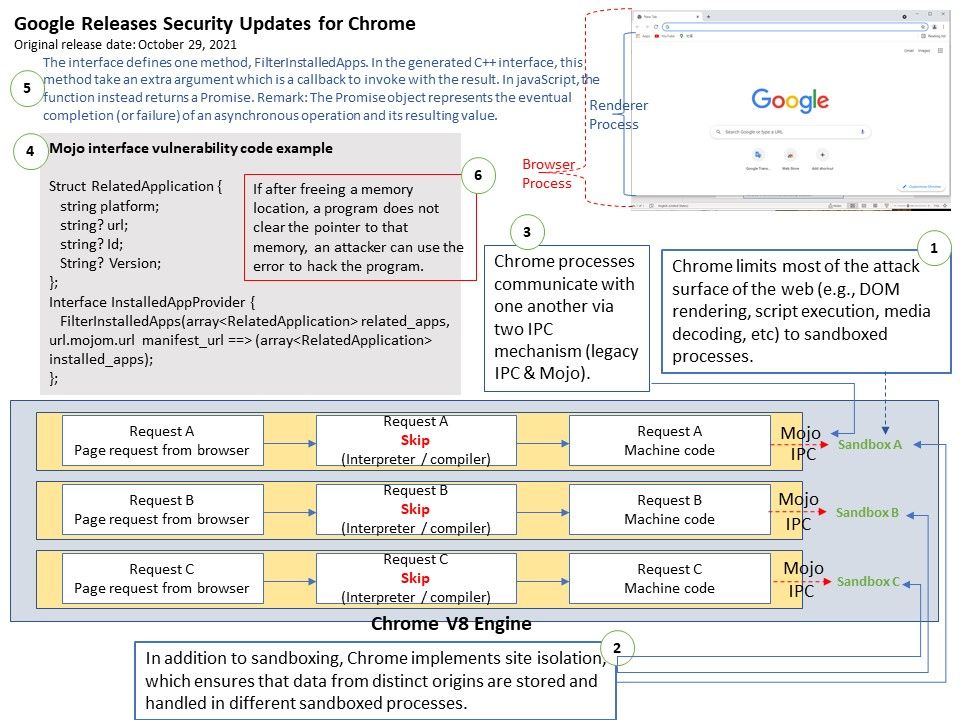
Vulnerability details: Google described the one that attackers may be picking apart – CVE-2021-1048 – as caused by a use-after-free (UAF) vulnerability in the kernel.
Additional: CVE-2021-1048 is a use-after-free issue in the Kernel that allows for local privilege escalation but require attacker had local access right. Afterwards, the attacker can install rogue applications or use Internet Web applications to obtain malicious code (Javascript).
As a result, the attacker will escape the sandbox and abuse this kernel vulnerability.
Official announcement: Published November 1, 2021 | Updated November 2, 2021. There are indications that CVE-2021-1048 may be under limited, targeted exploitation.Please refer to the link for details – https://source.android.com/security/bulletin/2021-11-01