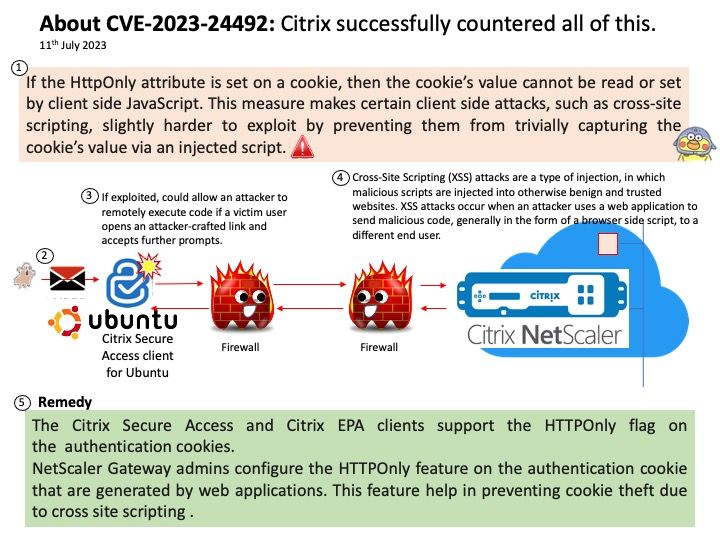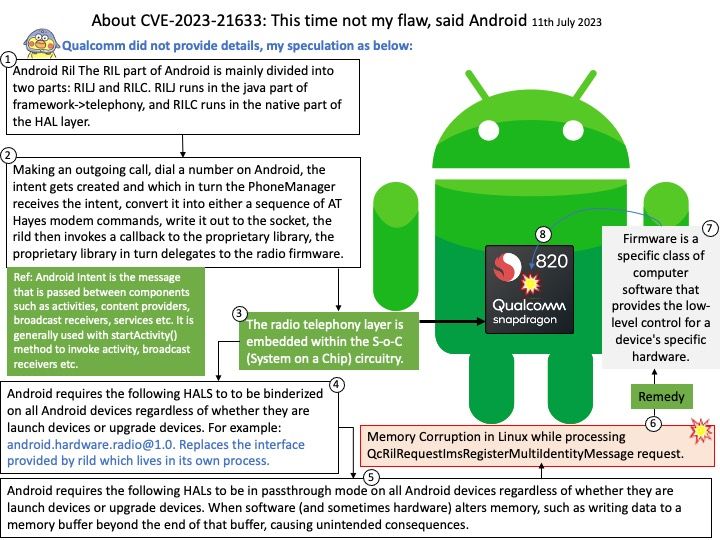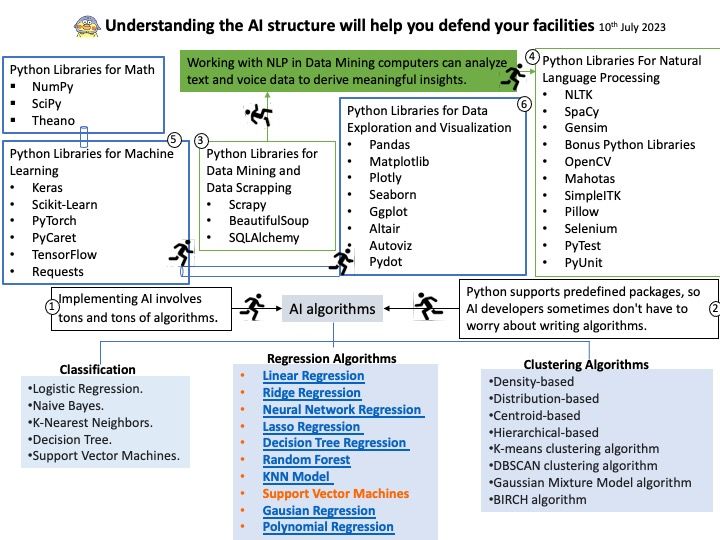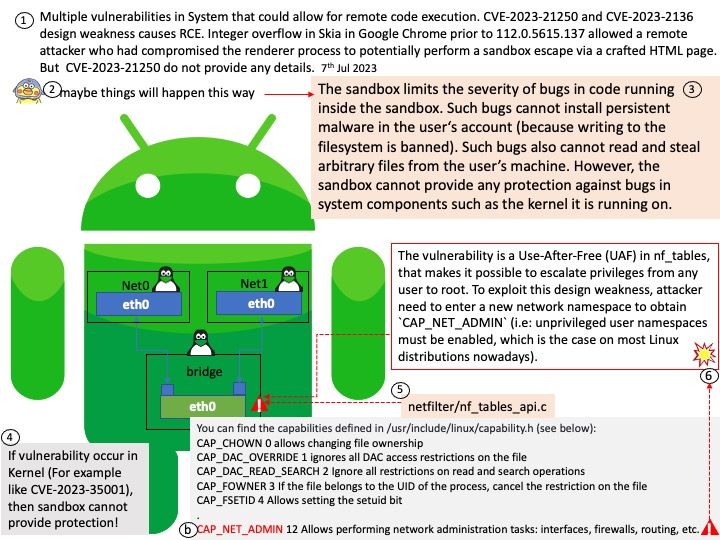
Background: Use Citrix Gateway with StoreFront to provide secure remote access for users outside the corporate network and Citrix ADC to provide load balancing.
*Citrix StoreFront is an enterprise application store that provides an interface for users to access XenDesktop and XenApp virtual desktops and applications remotely.
How do I access Citrix StoreFront? On the Windows Start screen or Apps screen, locate and click the Citrix StoreFront tile. Select the Stores node in the right pane of the Citrix StoreFront management console and, in the results pane, select a store. In the Actions pane, click Configure Remote Access Settings.
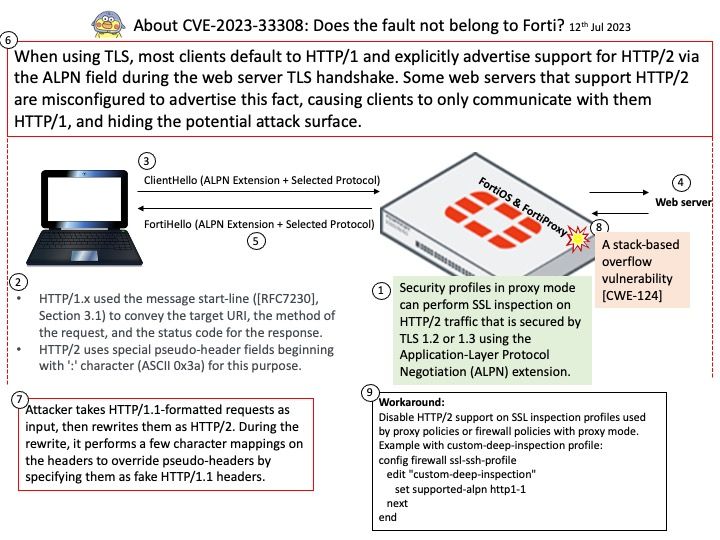
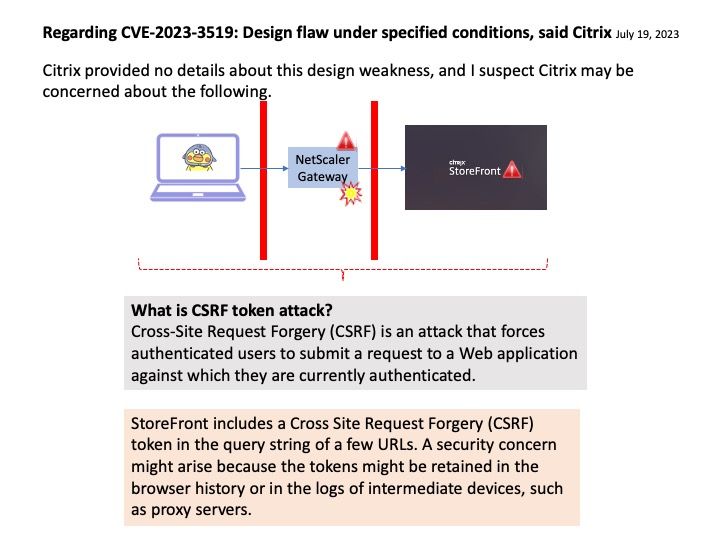
Vulnerability details: An attacker can exploit design weakness to execute code remotely without authentication.
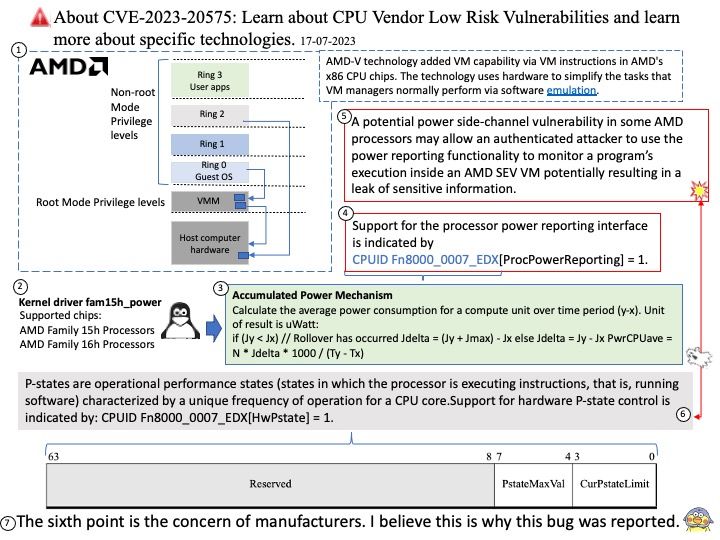
Design flaws arise under specified conditions: Appliance must be configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) OR AAA virtual server.
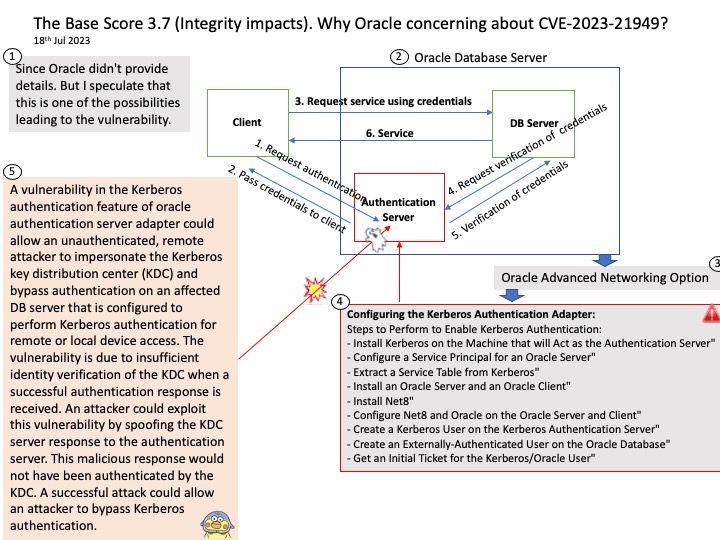
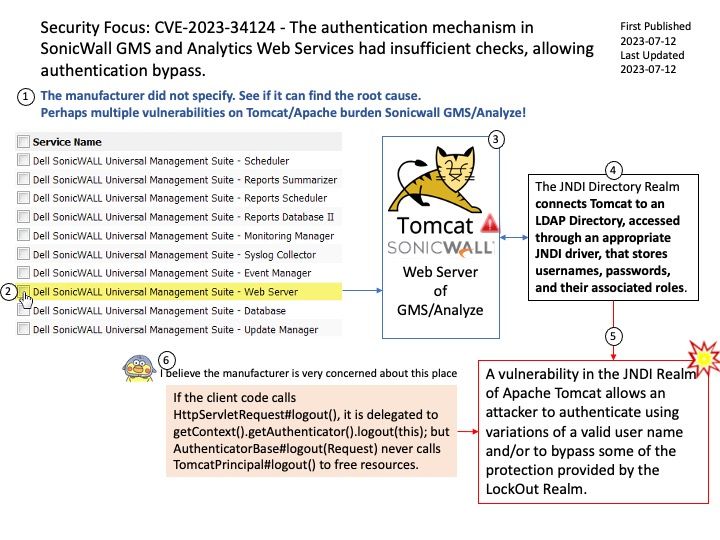
Ref: StoreFront includes a Cross Site Request Forgery (CSRF) token in the query string of a few URLs. A security concern might arise because the tokens might be retained in the browser history or in the logs of intermediate devices, such as proxy servers.
Official announcement: For details, please refer to the link – https://support.citrix.com/article/CTX561482/citrix-adc-and-citrix-gateway-security-bulletin-for-cve20233519-cve20233466-cve20233467