Preface
The objective of the smart city is design to incorporates information and communication technologies (ICT) to enhance the quality of life. The Smart City derivatives the cost effective solution. As a result, it benefits to urban services such as energy, transportation and utilities in order to reduce resource consumption, wastage and overall costs.
2 Common Focus (Shared Data and Open Data)
People concerning the personal privacy and therefore the key words data sharing make them scare.As a matter of fact the data breach incidents happened so far let people focus their defense idea on how to protect their personal data. And therefore whatever sharing concept will trigger their defense idea. Meanwhile this is the bottleneck to slow down smart city development.
About public data – Public data is information that can be freely used, reused and redistributed by anyone with no existing local, national or international legal restrictions on access or usage.
Understanding of data classification
Classifying data is the process of categorizing data assets based on nominal values according to its sensitivity.
The data classification scheme – definition table shown as below:
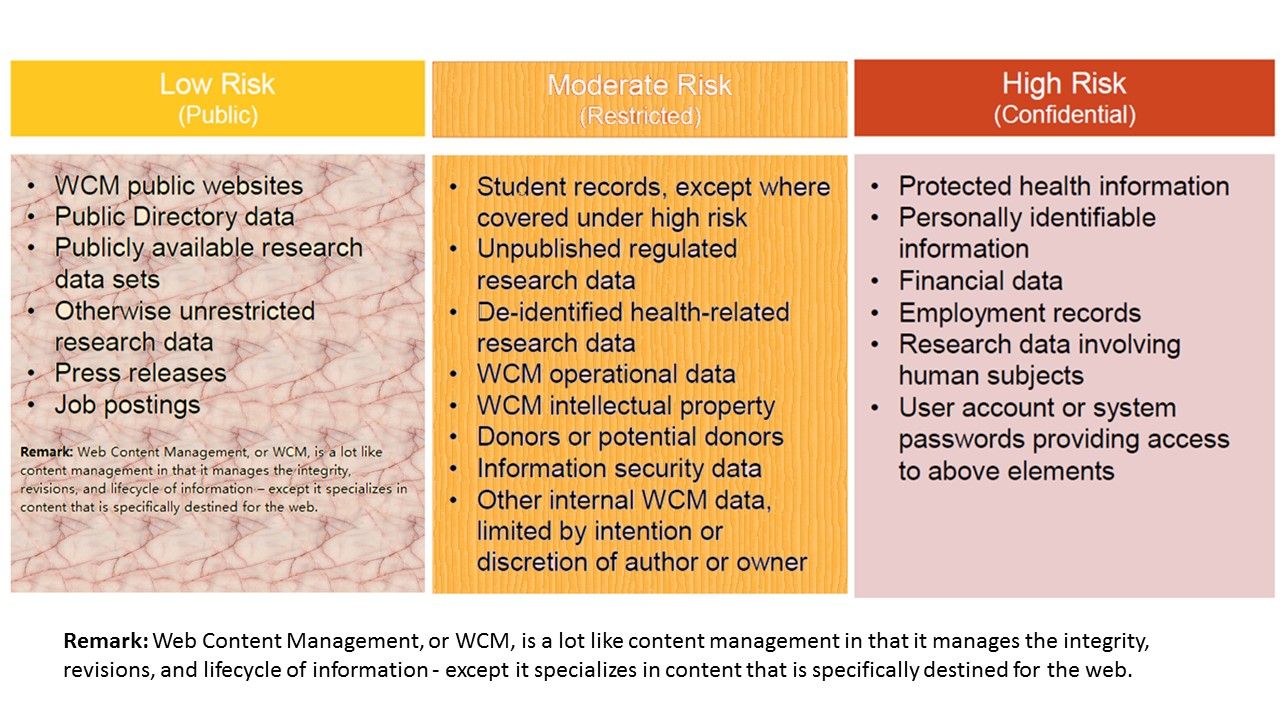
If we all agree on above data classification labels definitions. And do not have concerns (hiccups) for the terms of use set up. So do we have any other concern of smart City?
Hidden item – Technology Risk management – Whether follow the regular software patch cycle (zero day) to smart city?
From technical point of view, government facilities must follow the best practice to fulfill the patch management. However hardware manufacturer not guarantee they can remedy the vulnerability in quick manner. From some circumstances, smart city not only covered the fundemental infrastructure operation. It involves AI integration. That is business facilities join venture with government facilities. So how to maintain a secure environment? It is one of key element in smart City.
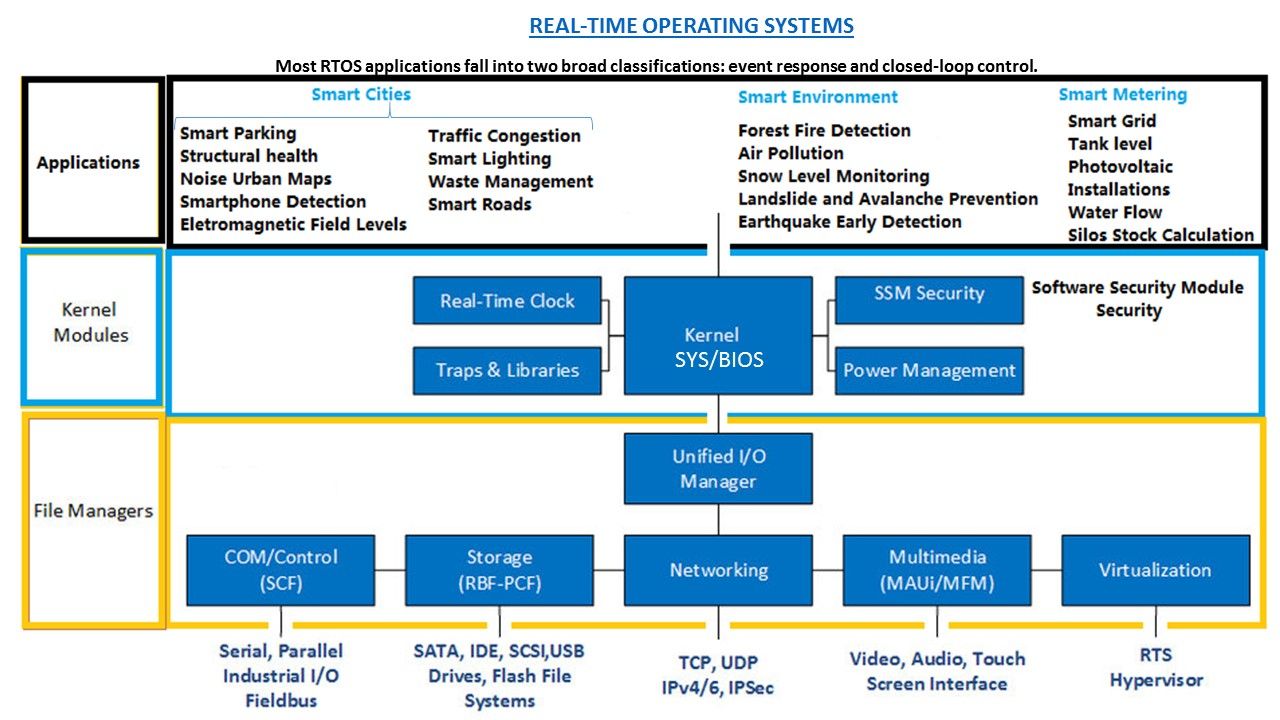
REAL-TIME OPERATING SYSTEMS (RTOS)
Internet of Things is growing rapidly, the common standard of smart devices will be designed with Embedded Systems (ESs). Real Time Operating Systems (RTOS) are used in ESs development due to RTOS added important features as RTOS simplifies development and makes systems more reliable. A real-time operating system (RTOS) is an operating system (OS) intended to serve real-time applications that process data as it comes in, typically without buffer delays. Most RTOS applications fall into two broad classifications. They are event response and closed-loop control.
Reference: A closed loop system is one where the output is feed back into the the system as an input in some way. For instance a thermostat.
Continuous closed-loop control
WHILE (Y <> specified_condition)
take_action(X)
measure(Y)
wait(Z)
REPEAT
Event response applications, such as automated visual inspection of assembly line parts, require a response to a stimulus in a certain amount of time. In this visual inspection system, for example, each part must be photographed and analyzed before the assembly line moves.
Reference: A closed loop system is one where the output is fed back into the the system as an input in some way. For instance a thermostat.
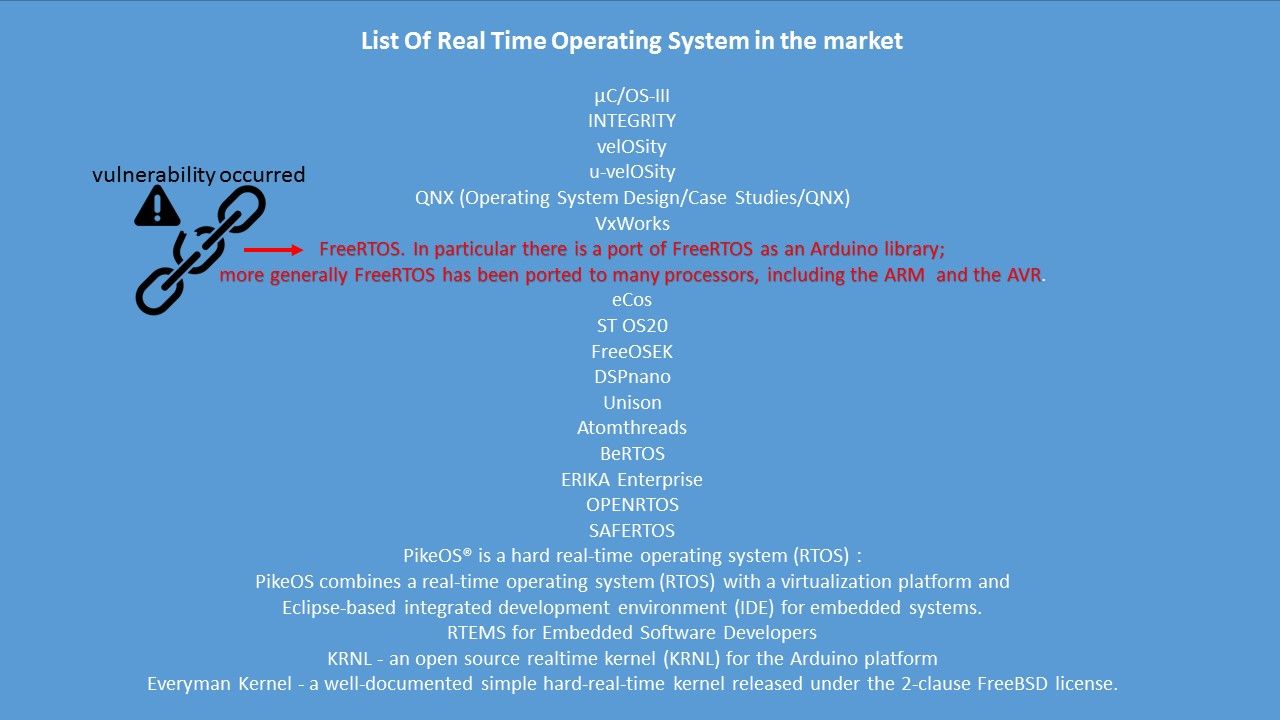
List Of Real Time Operating System in the market
IoT devices potential risk
Threat actors exploit IoT device weakness conduct cyber attack. As a result cyber security guru summarizes the following design weakness of IoT devices. Those devices are heavy deployed in smart city. For instance survillance web cam, sensor, motion detector, … etc. The design weakness are shown as below:
6 Big Security Concerns About IoT For Business
- Default ‘Raw Data’ Storage
- Insecure Devices.
- Lack Of Updates
- Hard to avoid Data Breaches
- Difficult to compliant Data Storage policy
- High hit rate to become a DDoS Attacks tool.
Vulnerabilities & Exposure (recently) – FreeRTOS vulnerabilities awake IoT technology weakness. Vulnerabilities discovered in the FreeRTOS operating system can expose a wide range of systems to attacks, including smart home devices and critical infrastructure.
Risk factor: FreeRTOS TCP/IP Stack Vulnerabilities put a wide range of devices at risk of compromise. Researchers from Zimperium’s zLabs have analyzed FreeRTOS’s TCP/IP stack and AWS secure connectivity modules, and discovered vulnerabilities that also impact OpenRTOS and SafeRTOS.
| CVE-2018-16522 |
Remote Code Execution |
| CVE-2018-16525 |
Remote Code Execution |
| CVE-2018-16526 |
Remote Code Eexecution |
| CVE-2018-16528 |
Remote Code Execution |
| CVE-2018-16523 |
Denial of Service |
| CVE-2018-16524 |
Information Leak |
| CVE-2018-16527 |
Information Leak |
| CVE-2018-16599 |
Information Leak |
| CVE-2018-16600 |
Information Leak |
| CVE-2018-16601 |
Information Leak |
| CVE-2018-16602 |
Information Leak |
| CVE-2018-16603 |
Information Leak |
| CVE-2018-16598 |
Other |
Summary:
In technology world, it is hard to avoid the vulnerability occurs. Perhaps patch management now includes in modern software and system development life cycle. There are two popular ways of disclosing vulnerabilities to software vendors.
- The first is called full disclosure – researchers immediately publish their vulnerability to public, giving the vendors absolutely no opportunity to release a fix.
- The second is called responsible disclosure, or staggered disclosure. This is where the researcher contacts the vendor before the vulnerability is released. Vendor is given a conventional 30 calendar days to fix vulnerability. Some security holes cannot be fixed easily, and require entire software systems to be rebuilt from scratch.Once both parties are satisfied with the fix that’s been produced, the vulnerability is then disclosed and given a CVE number. Regarding to above FreeRTOS vulnerabilities, Amazon addressed the issues with the release of FreeRTOS 1.3.2.But what is the remedy status of the opensource application? As far as I know, security researcher agree to give another 30 days to allow vendors to deploy the patches. However the potential risks are valid until vendor fix the security hole.
Smart City infrastructure not proprietary for famous vendor. We can use not famous brand name surveillance web cam, senor and motion detector. Could you imagine what is the actual status once the vulnerabilities occurs?
Reference:
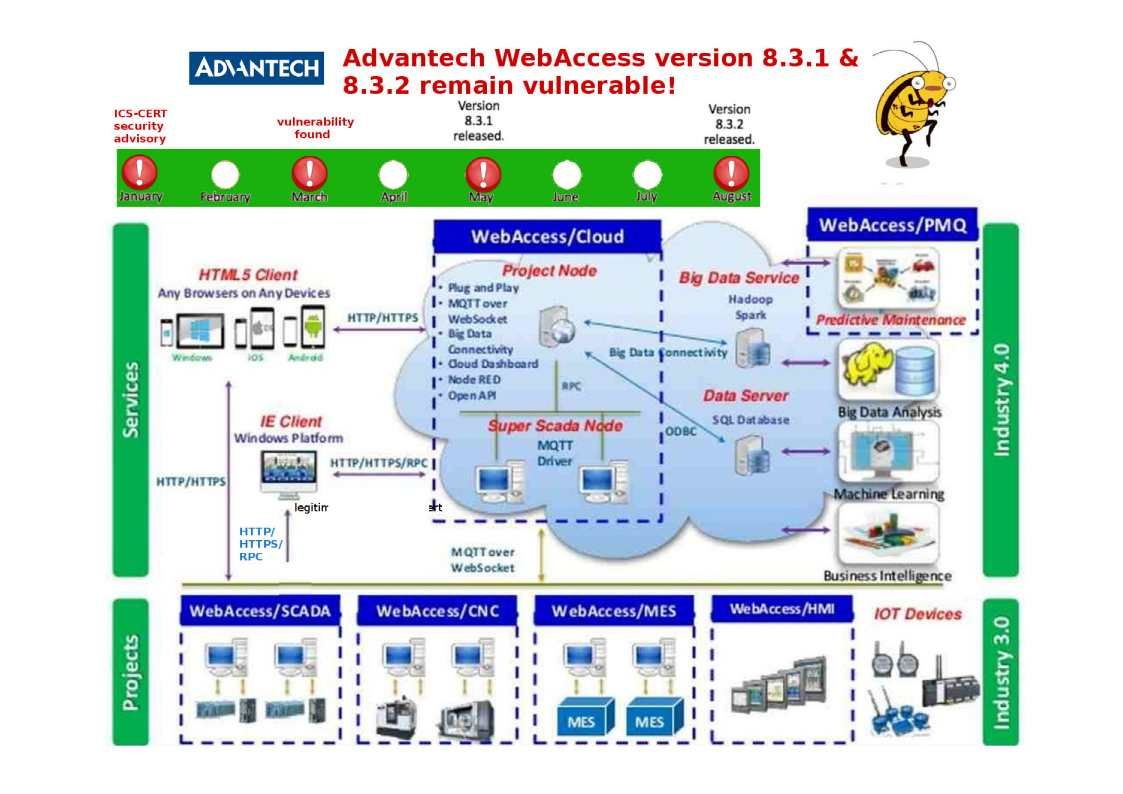
Smart City infrastructure work closely with MQTT technology.
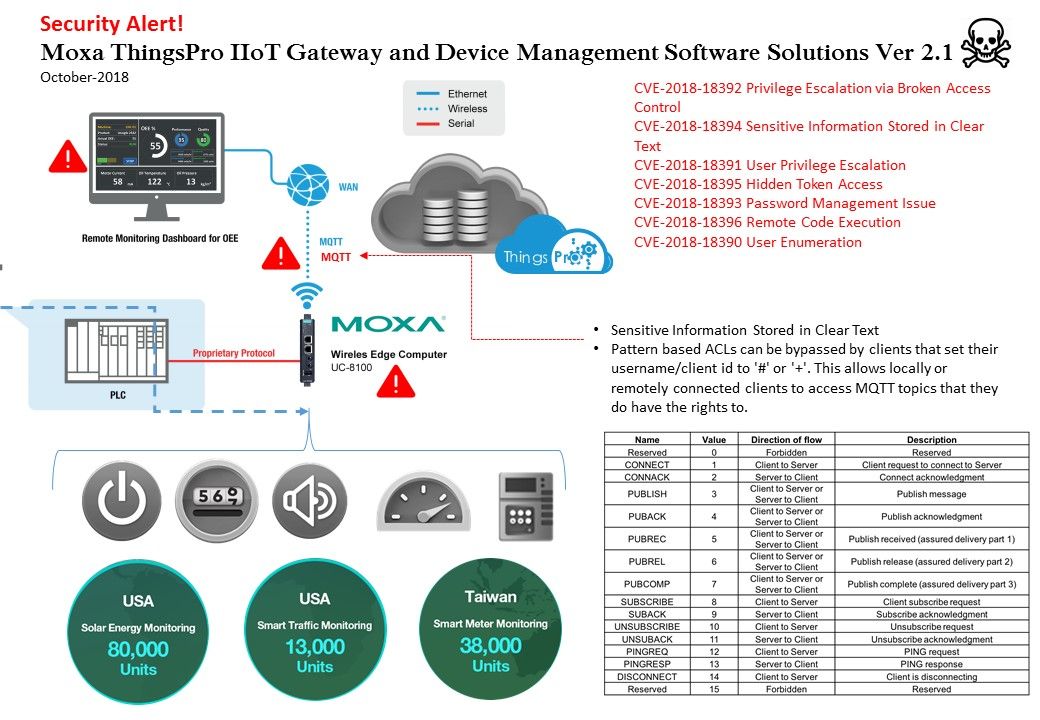
Security Alert – Moxa ThingsPro IIoT Gateway and Device Management Software Solutions version 2.1.
Security Alert! Moxa ThingsPro IIoT Gateway and Device Management Software (Oct 2018)