Preface: When defining mappings, it will configure the fields that contain an array of objects within them as “object” type. This is fine in many cases, but sometimes the mappings will need to be adjusted.
Nested is a special type of object that is indexed as a separate document, and a reference to each of these inner documents is stored with the containing document, so we can query the data accordingly.
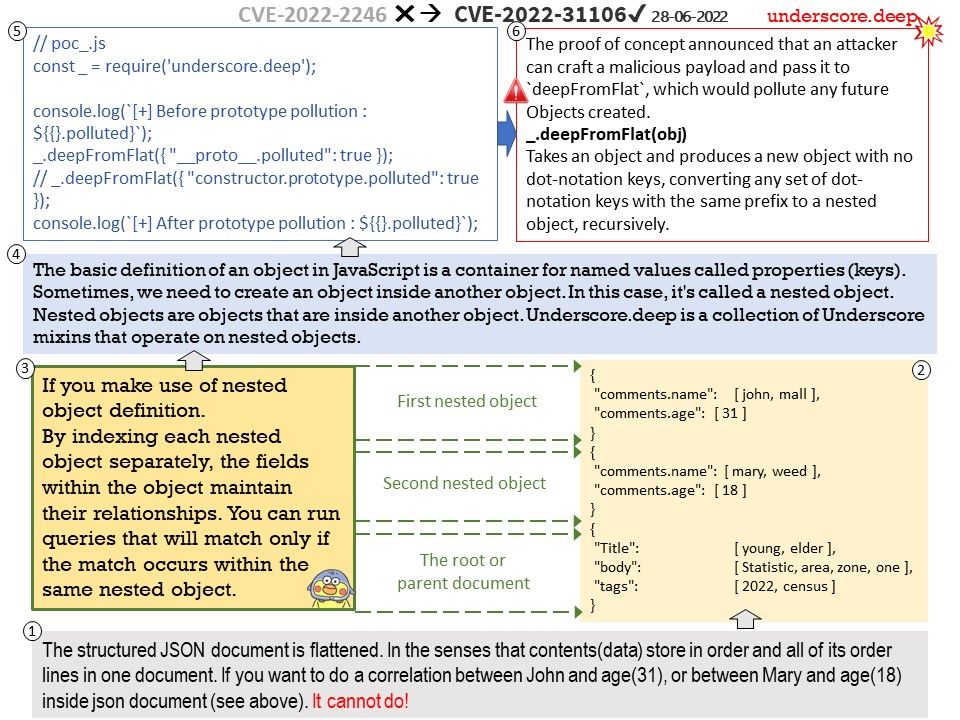
Background: The basic definition of an object in JavaScript is a container for named values called properties (keys). Sometimes, we need to create an object inside another object. In this case, it’s called a nested object.Nested objects are objects that are inside another object.Underscore.deep is a collection of Underscore mixins that operate on nested objects. Dealing with nested objects often we’ll be needing to access the innermost nested values safely.
Vulnerability details: Underscore.deep is a collection of Underscore mixins that operate on nested objects. Versions of underscore.deep prior to version 0.5.3 are vulnerable to a prototype pollution vulnerability. An attacker can craft a malicious payload and pass it to deepFromFlat, which would pollute any future Objects created. Any users that have deepFromFlat or deepPick (due to its dependency on deepFromFlat) in their code should upgrade to version 0.5.3 as soon as possible.
Workarounds: Is there a way for users to fix or remediate the vulnerability without upgrading? Modifying deepFromFlat to prevent specific keywords will prevent this from happening. For details, please refer to link – https://github.com/clever/underscore.deep/commit/b5e109ad05b48371be225fa4d490dd08a94e8ef7
Remedy: Users should upgrade to 0.5.3.