Preface: You can use POSIX permissions to lock down access to the file descriptor (FD) associated with the socket, and the server side can request information such as credentials and PID of clients before they can fully connect.
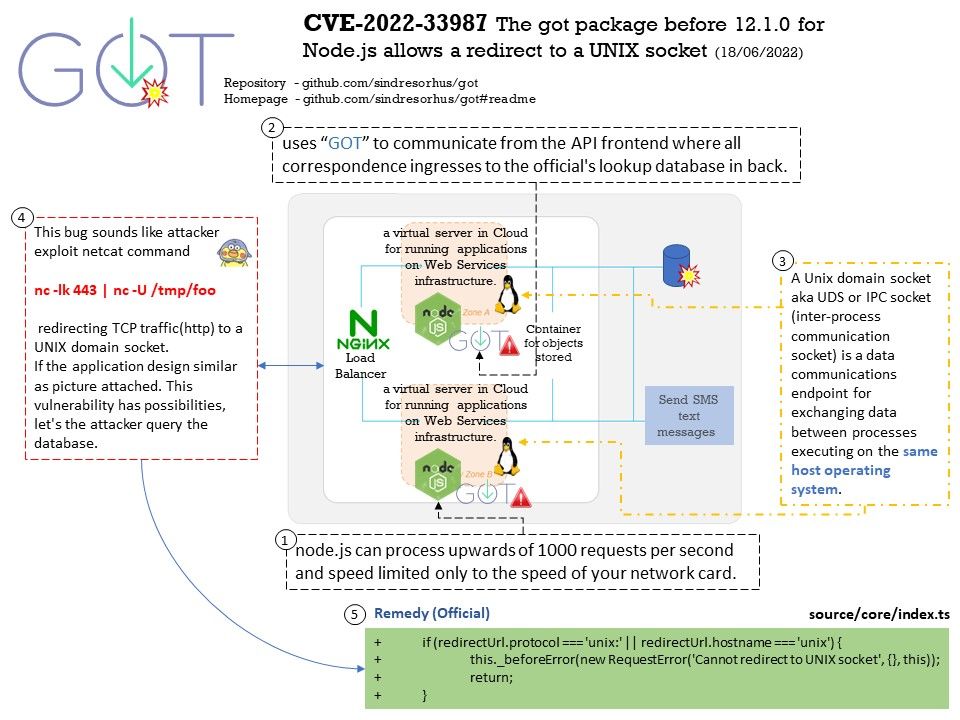
Background: node.js can process upwards of 1000 requests per second and speed limited only to the speed of your network card.
From techincal point of view, in order to improve the loading on new generation of web services. There are web application design not using traditional way. They uses “GOT” to communicate from the API frontend where all correspondence ingresses to the official’s lookup database in back.
It’s a GET request by default, but can be changed by using different methods or via options.method. By default, Got will retry on failure. To disable this option, set options.retry to 0.
Vulnerability details: A vulnerability was found in got Package up to 12.0.3. The design weakness allow Node.js redirect to a UNIX socket. A Unix domain socket aka UDS or IPC socket (inter-process communication socket) is a data communications endpoint for exchanging data between processes executing on the same host operating system.
This bug sounds like attacker exploit netcat command redirecting TCP traffic(http) to a UNIX domain socket. If the application design similar as picture attached. This vulnerability has possibilities, let’s the attacker query the database.
Remedy: Disable redirects to UNIX sockets – https://github.com/sindresorhus/got/pull/2047/commits/ef5cc13996b9765f306625ac5a0040bd445580eb