Preface: The registration of CVE records is largely out of sync with the time of the event. Perhaps the new release of CVE record by today, however it was happened few weeks or months ago. But with reference of these vulnerabilities records. Vulnerability scanner can precisely provide a result to you after scan.
Background: A USB Linux Gadget is a device which has a UDC (USB Device Controller) and can be connected to a USB Host to extend it with additional functions like a serial port or a mass storage capability.
Another way to integrate Modern USB gadgets on Linux with systemd: Users create a separate directory for each gadget they want to have, give their gadget a personality by specifying a vendor ID, product ID, and a USB string (eg visible after running lsusb -v as root), then In that directory create the configuration they want and instantiate the USB functions they want (both by creating the corresponding directory), and finally associate the function with the configuration via a symlink. At this point, the composition of the gadget is already in memory, but not bound to any UDC. To activate a gadget, the UDC name must be written to the UDC property in the gadget’s configfs directory – the gadget is then bound to this specific UDC (and a UDC cannot be used by multiple gadgets). Available UDC names are at /sys/class/udc. The gadget can only be successfully enumerated by the USB host after it is bound to the UDC.
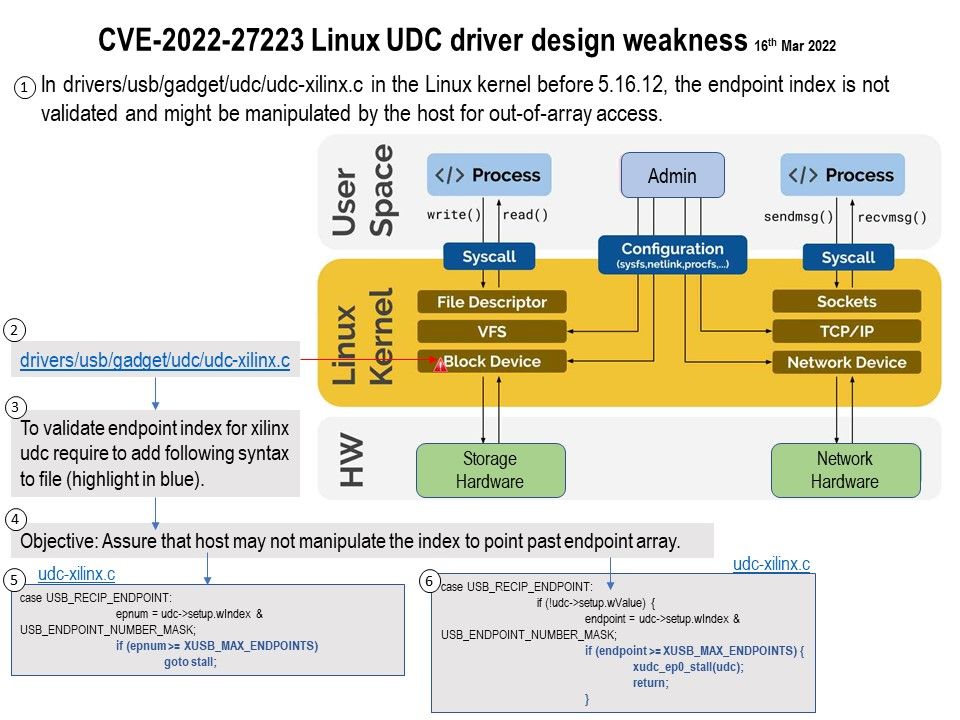
Vulnerability details: In drivers/usb/gadget/udc/udc-xilinx[.]c in the Linux kernel before 5.16.12, the endpoint index is not validated and might be manipulated by the host for out-of-array access.
References to Advisories: https://github.com/torvalds/linux/commit/7f14c7227f342d9932f9b918893c8814f86d2a0d