Preface: In 2021, Linux has been one of the most popular software packages for client devices. According to Digital TV Europe, 800 million set-top boxes are powered by this platform worldwide.
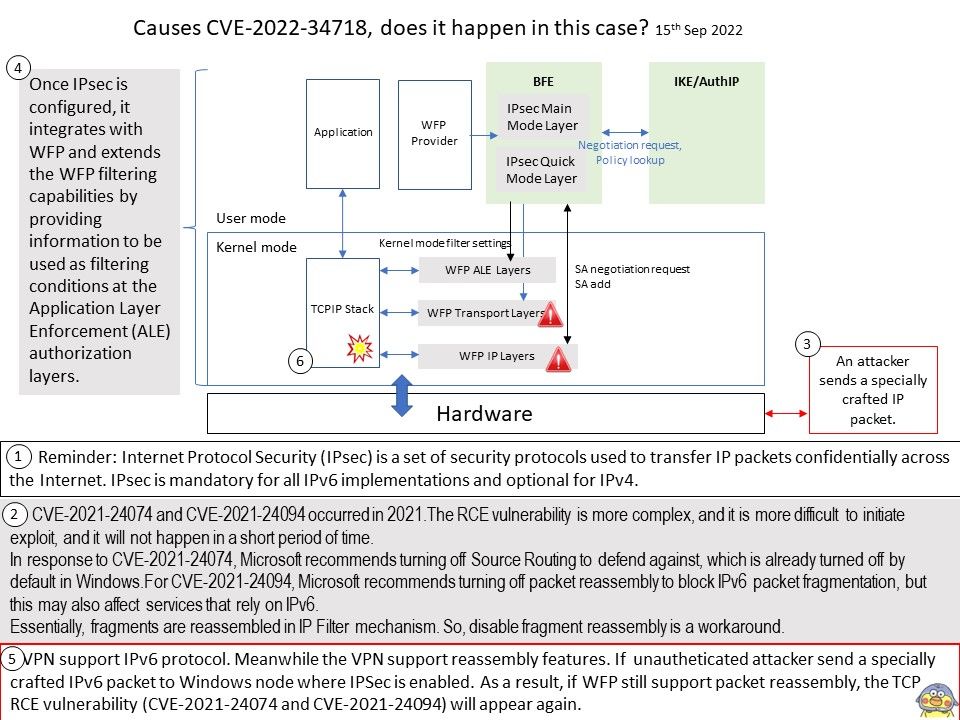
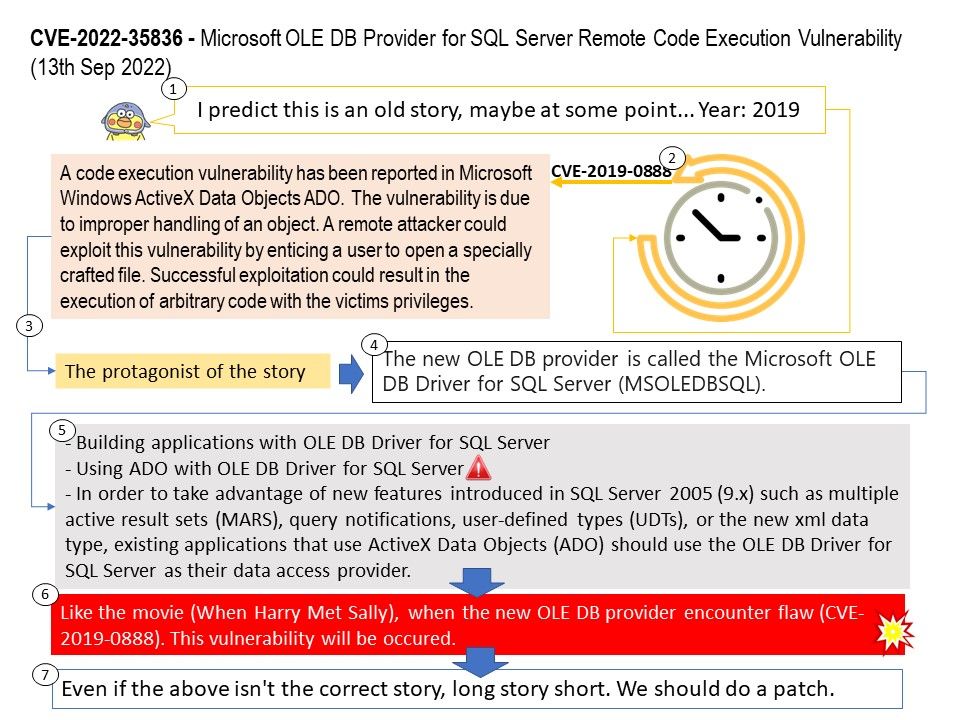
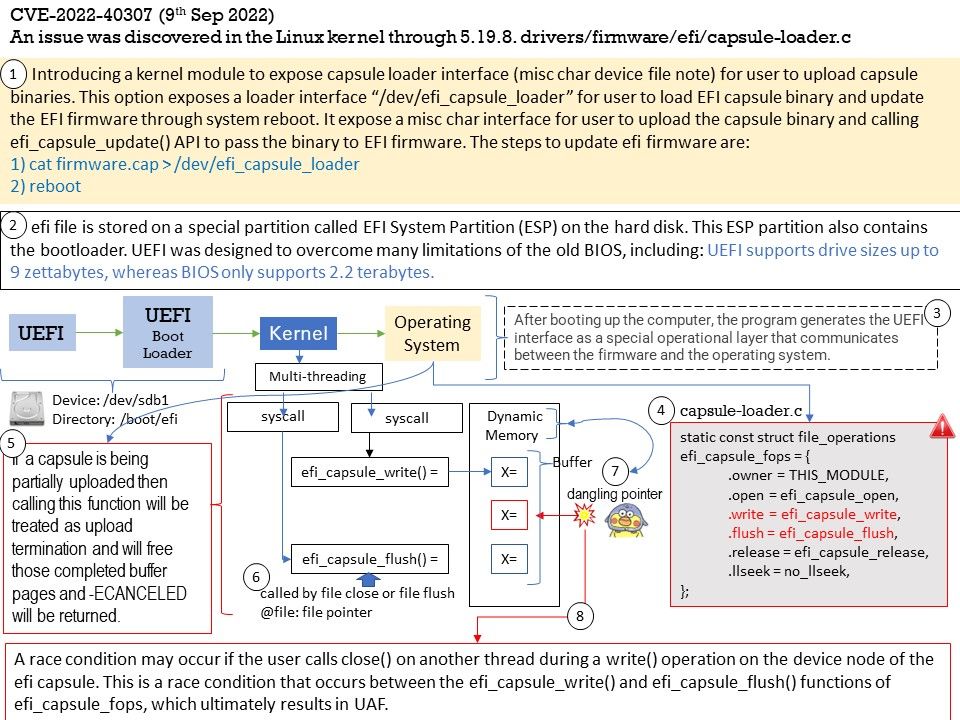
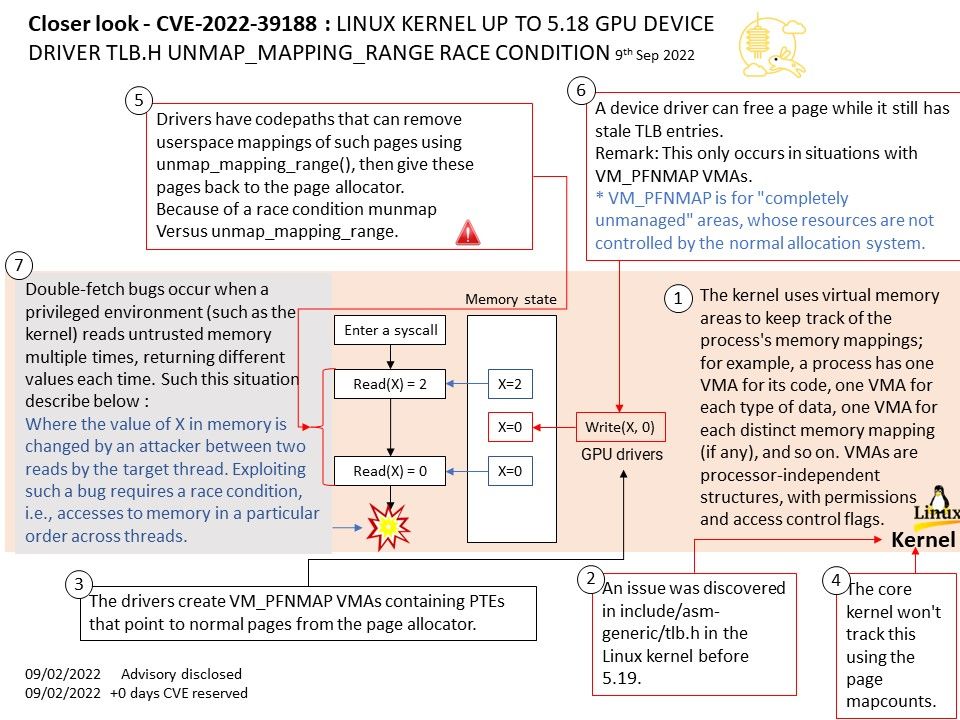
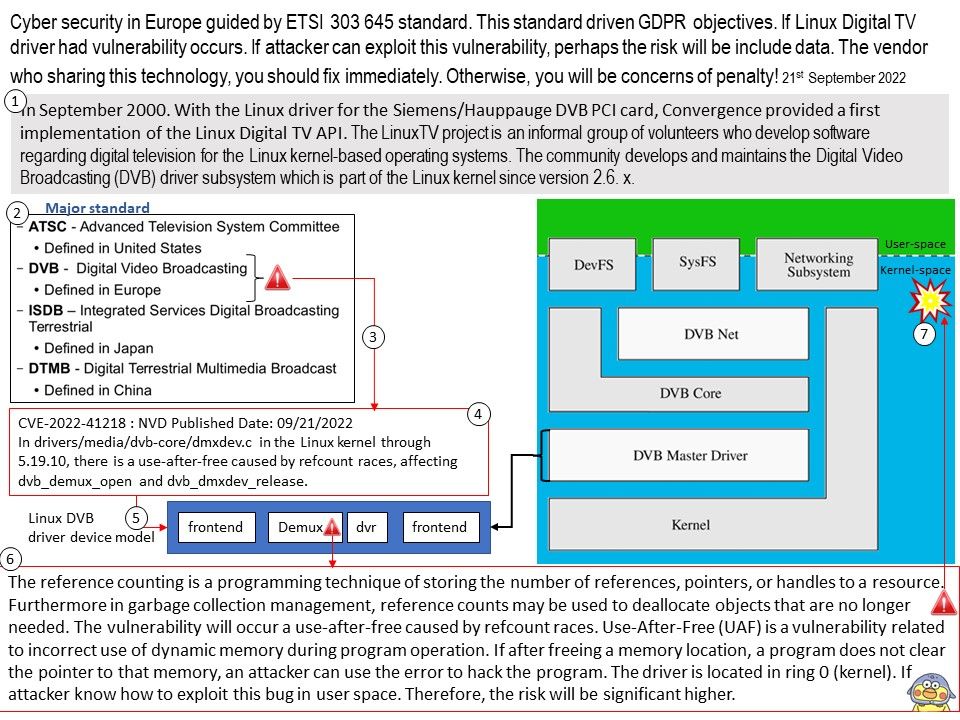
Background: The LinuxTV project is an informal group of volunteers who develop software regarding digital television for the Linux kernel-based operating systems. The community develops and maintains the Digital Video Broadcasting (DVB) driver subsystem which is part of the Linux kernel since version 2.6. x.
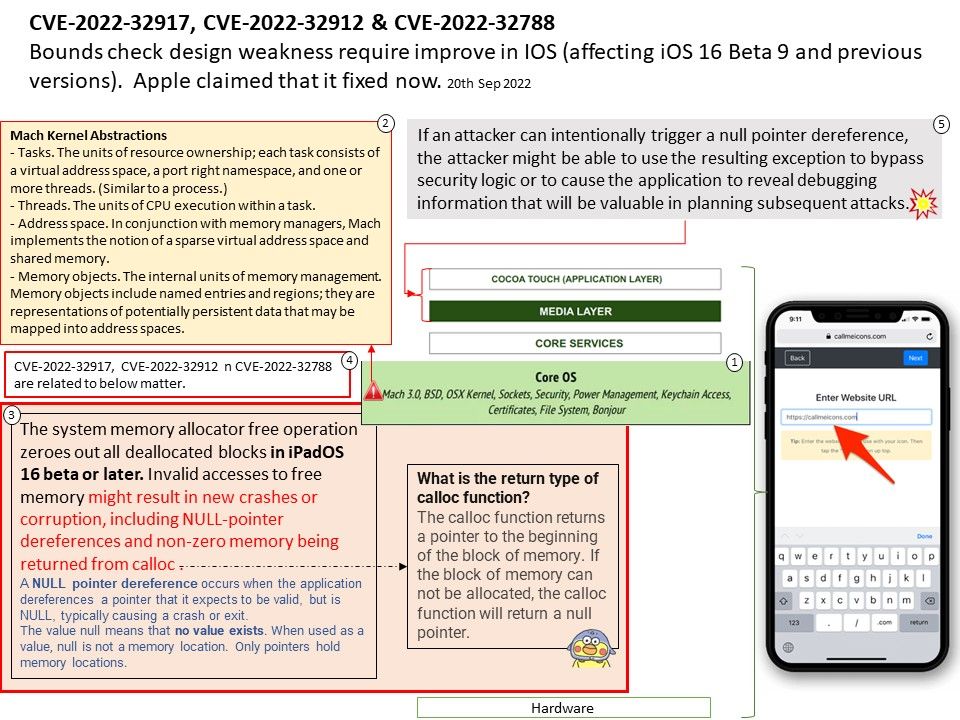
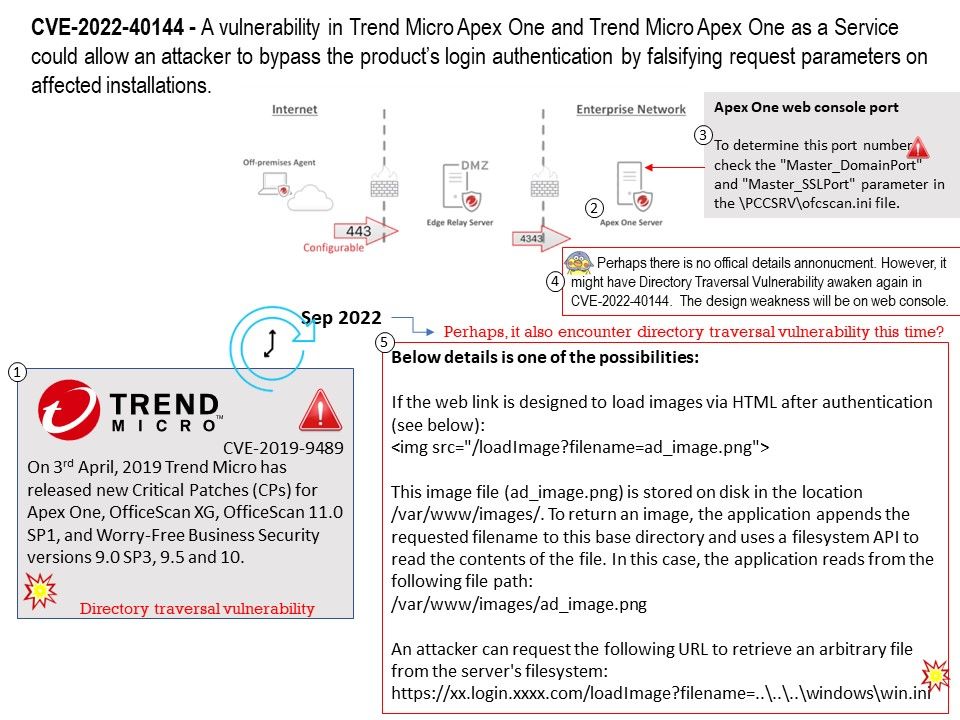
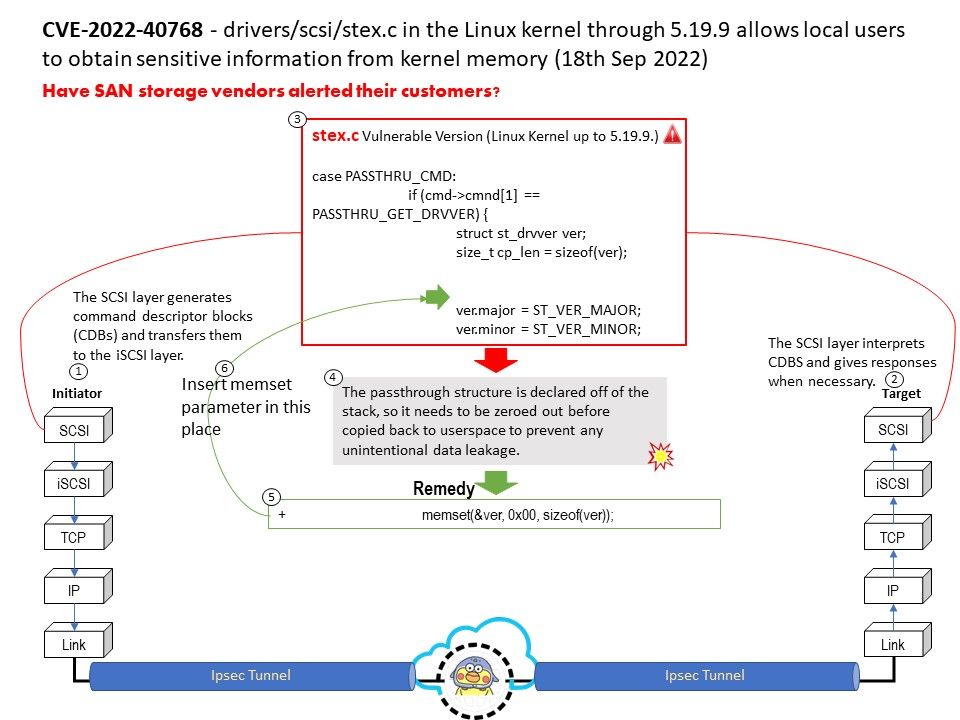
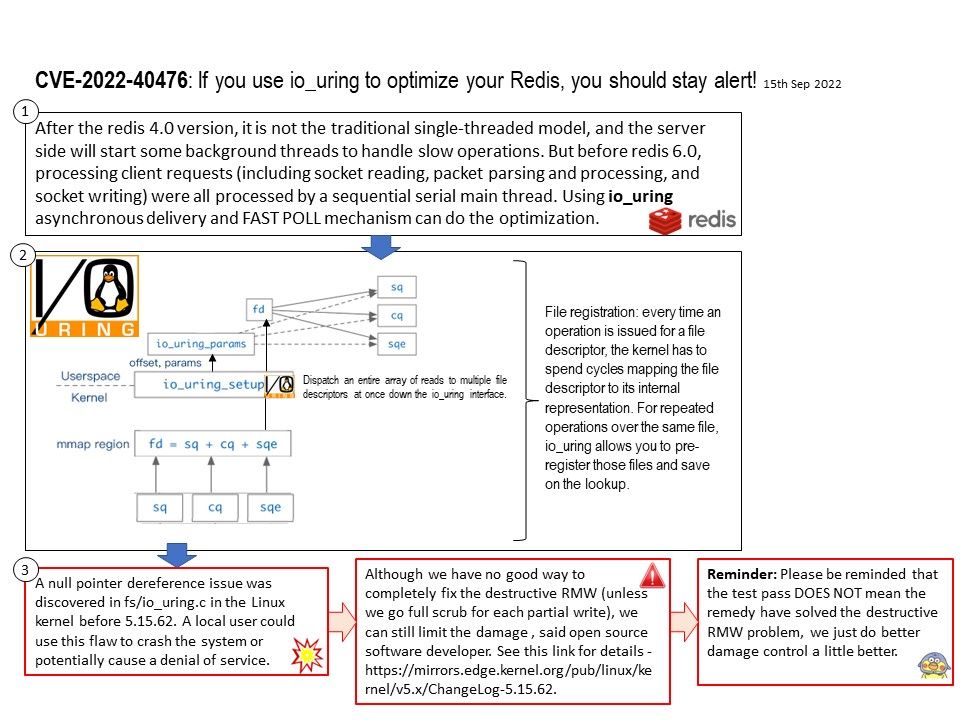
Vulnerability details: In drivers/media/dvb-core/dmxdev.c in the Linux kernel through 5.19.10, there is a use-after-free caused by refcount races, affecting dvb_demux_open and dvb_dmxdev_release.
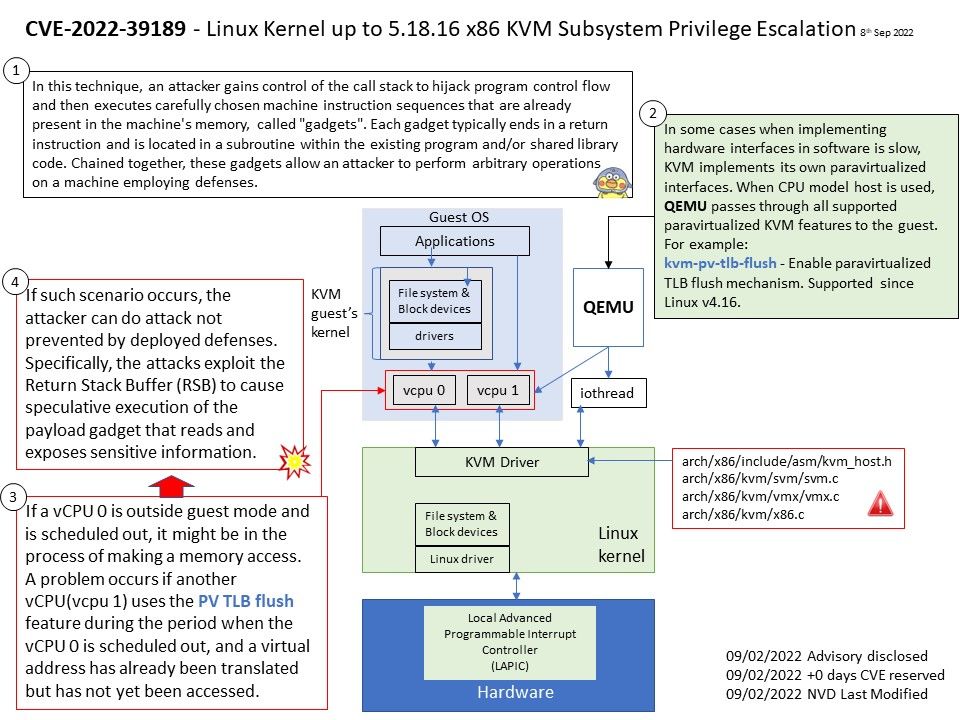
Ref: In computer world, reference counting is a programming technique of storing the number of references, pointers, or handles to a resource, such as an object, a block of memory, disk space, and others.
Furthermore in garbage collection management, reference counts may be used to deallocate objects that are no longer needed.
Reference counts can be used when tracking how many objects contain a reference to a particular resource, such as in memory management or garbage collection. Race condition causes reference counter to be decremented prematurely, leading to the destruction of still-active object and an invalid pointer dereference.
An invalid pointer reference occurs when a pointer’s value is referenced even though the pointer doesn’t point to a valid block.
My observation:
The reference counting is a programming technique of storing the number of references, pointers, or handles to a resource. Furthermore in garbage collection management, reference counts may be used to deallocate objects that are no longer needed. The vulnerability will occurs a use-after-free caused by refcount races. Use-After-Free (UAF) is a vulnerability related to incorrect use of dynamic memory during program operation. If after freeing a memory location, a program does not clear the pointer to that memory, an attacker can use the error to hack the program. The driver is located in ring 0 (kernel). If attacker know how to exploit this bug in user space. Therefore, the risk will be significant higher.
Solution and official details: Please refer to this link – https://nvd.nist.gov/vuln/detail/CVE-2022-41218