Preface: Whether it is correct or not, this is a spirit for learning.
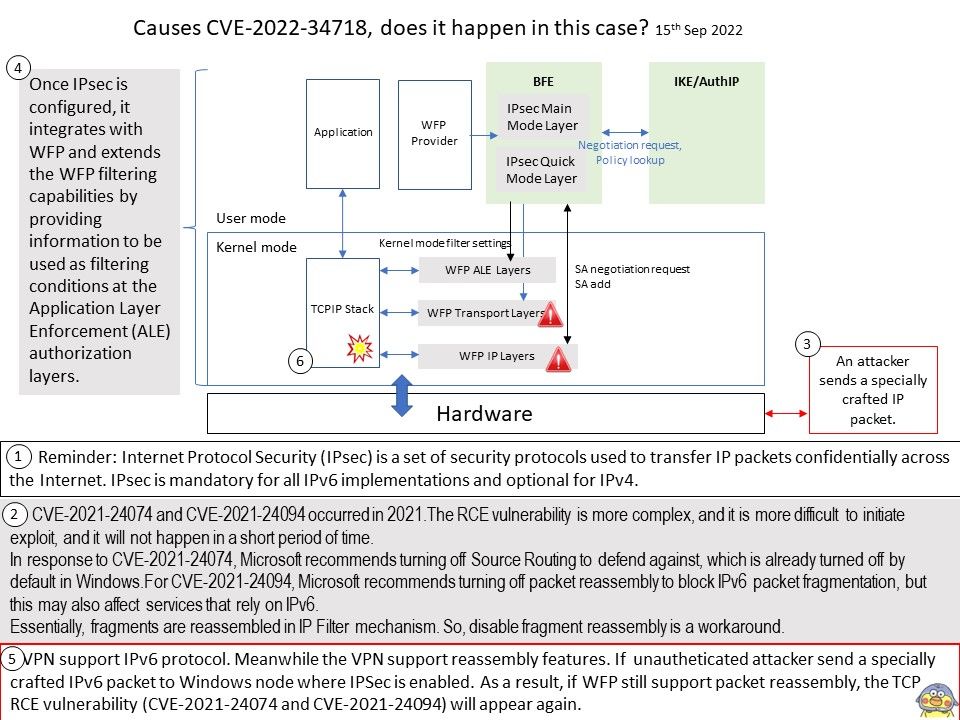
Background: The critical CVE (CVE-2022-34718 ) impacts Windows TCP/IP, allowing an unauthenticated attacker to send a specially crafted IPv6 packet to Windows node where IPSec is enabled. But the supplier didn’t reveal too many details.
My observation: CVE-2021-24074 and CVE-2021-24094 occurred in 2021.The RCE vulnerability is more complex, and it is more difficult to initiate exploit, and it will not happen in a short period of time.
In response to CVE-2021-24074, Microsoft recommends turning off Source Routing to defend against, which is already turned off by default in Windows.
For CVE-2021-24094, Microsoft recommends turning off packet reassembly to block IPv6 packet fragmentation, but this may also affect services that rely on IPv6.
Essentially, fragments are reassembled in IP Filter mechanism. So, Disable fragment reassembly is a workaround.
VPN support IPv6 protocol. Meanwhile the VPN support reassembly features. If unautheticated attacker send a specially crafted IPv6 packet to Windows node where IPSec is enabled. As a result, if WFP still support packet reassembly, the TCP RCE vulnerability (CVE-2021-24074 and CVE-2021-24094) will appears again.
Official detail:Please go to the link for details https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2022-34718