Preface: iSCSI is popular in the implementation of SAN systems because of their block level storage structure. When data arrives at its destination the iSCSI protocol separates the SCSI commands so that the Operating System will see the storage as a local device and allow formatting as usual.
Background: iSCSI is a block protocol for storage networking and runs the very common SCSI storage protocol across a network connection which is usually Ethernet. iSCSI, like Fibre Channel, can be used to create a Storage Area Network (SAN). iSCSI traffic can be run over a shared network or a dedicated storage network.
Design concept:
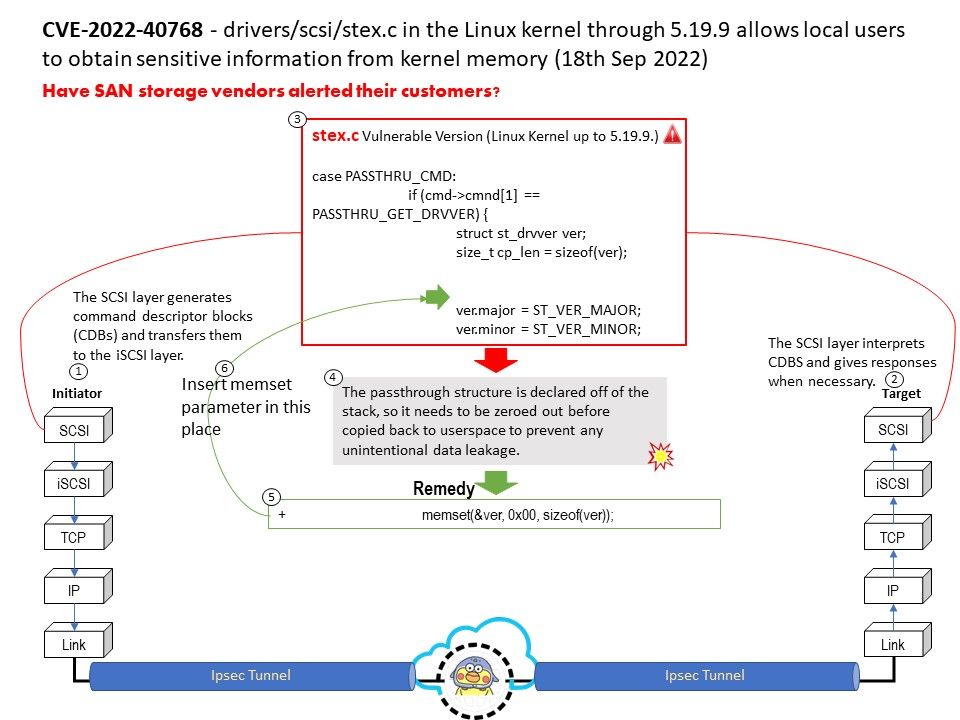
Initiator – The SCSI layer generates command descriptor blocks (CDBs) and transfers them to the iSCSI layer. The iSCSI layer generates iSCSI protocol data units (PDUs) and send them to the targer over an IP network.
Target – The iSCSI layer receives PDUs and sends CDBs to the SCSI layer.The SCSI layer interprets CDBS and gives responses when necessary.
Vulnerability details: A vulnerability was found in Linux Kernel up to 5[.]19[.]9. The design weakness occurs in the function stex_queuecommand_lck of the file drivers/scsi/stex[.]c. The manipulation leads to information disclosure.
Remedy: The passthrough structure is declared off of the stack, so it needs to be zeroed out before copied back to userspace to prevent any unintentional data leakage.
References to Advisories – Please refer to the link for details:
https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/log/drivers/scsi/stex.c
https://lore.kernel.org/all/20220908145154.2284098-1-gregkh@linuxfoundation.org/
https://www.openwall.com/lists/oss-security/2022/09/09/1