Preface: Bounds checking is a compiler-based technique that adds run-time bounds information for each allocated block of memory, and checks all pointers against those at run- time. For C and C++, bounds checking can be performed at pointer calculation time or at dereference time.
Background: The calloc () function allocates memory for an array of nmemb elements of size bytes each and returns a pointer to the allocated memory. The memory is set to zero. If nmemb or size is 0, then calloc () returns either NULL, or a unique pointer value that can later be successfully passed to free ().
The Difference Between Malloc and Calloc is that calloc allocates the memory and initializes every byte in the allocated memory to 0. In contrast, malloc allocates a memory block of a given size and doesn’t initialize the allocated memory.
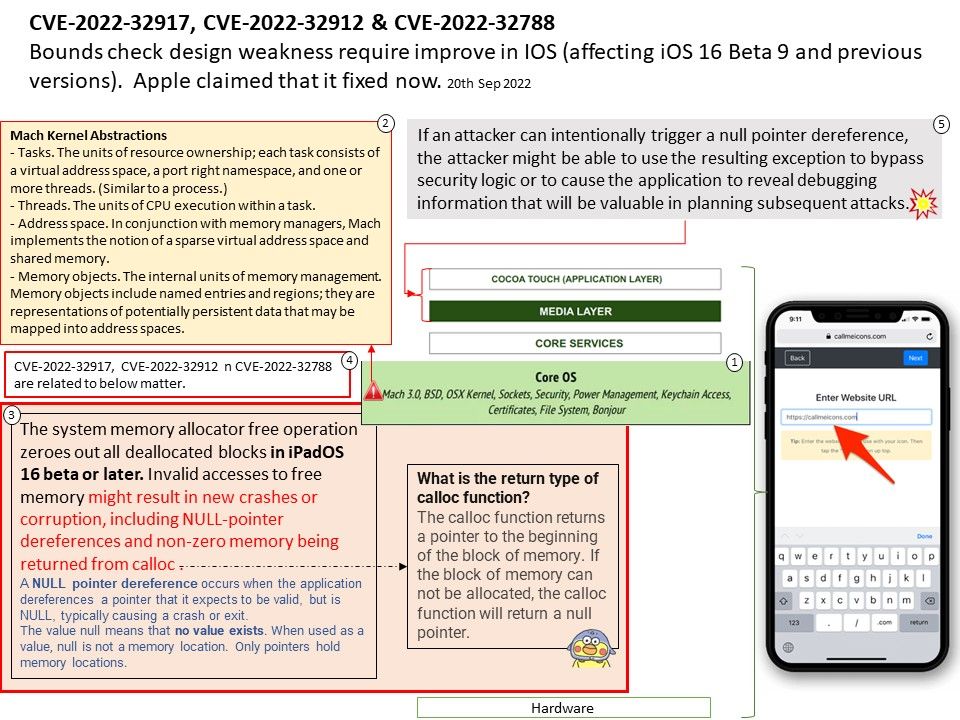
Mach Kernel Abstractions:
Mach provides a small set of abstractions that have been designed to be both simple and powerful. These are the main kernel abstractions:
- Tasks. The units of resource ownership; each task consists of a virtual address space, a port right namespace, and one or more threads. (Similar to a process.)
- Threads. The units of CPU execution within a task.
- Address space. In conjunction with memory managers, Mach implements the notion of a sparse virtual address space and shared memory.
- Memory objects. The internal units of memory management. Memory objects include named entries and regions; they are representations of potentially persistent data that may be mapped into address spaces.
- Ports. Secure, simplex communication channels, accessible only via send and receive capabilities (known as port rights).
- IPC. Message queues, remote procedure calls, notifications, semaphores, and lock sets.
- Time. Clocks, timers, and waiting.
Vulnerability details:
CVE-2022-32917 The issue was addressed with improved bounds checks – https://nvd.nist.gov/vuln/detail/CVE-2022-32917
CVE-2022-32912 An out-of-bounds read was addressed with improved bounds checking – https://www.tenable.com/cve/CVE-2022-32912
CVE-2022-32788 A buffer overflow was addressed with improved bounds checking – https://nvd.nist.gov/vuln/detail/CVE-2022-32788