Quote: A technical discussion on devblogs.microsoft.com – https://devblogs.microsoft.com/oldnewthing/20200113-00/?p=103322
This is not a vulnerability. In Windows, you can put a file in a directory that the user does not have access to, but if the user can produce the name of the file, they can still access it. This works because Windows by default enables “bypass traversal checks”, which means that you can access anything you can name.
Background: Trend Micro Apex One as a Service is a centrally managed anti-malware solution that protects endpoints (servers, desktops, and portable endpoints) from a wide variety of Internet threats.
– CVE-2022-40139: Improper Validation of Rollback Mechanism Components RCE Vulnerability
– CVE-2022-40140: Origin Validation Error Denial-of-Service Vulnerability
– CVE-2022-40141: Information Disclosure Vulnerability
– CVE-2022-40142: Agent Link Following Local Privilege Escalation Vulnerability
– CVE-2022-40143: Link Following Local Privilege Escalation Vulnerability
– CVE-2022-40144: Login Authentication Bypass Vulnerability
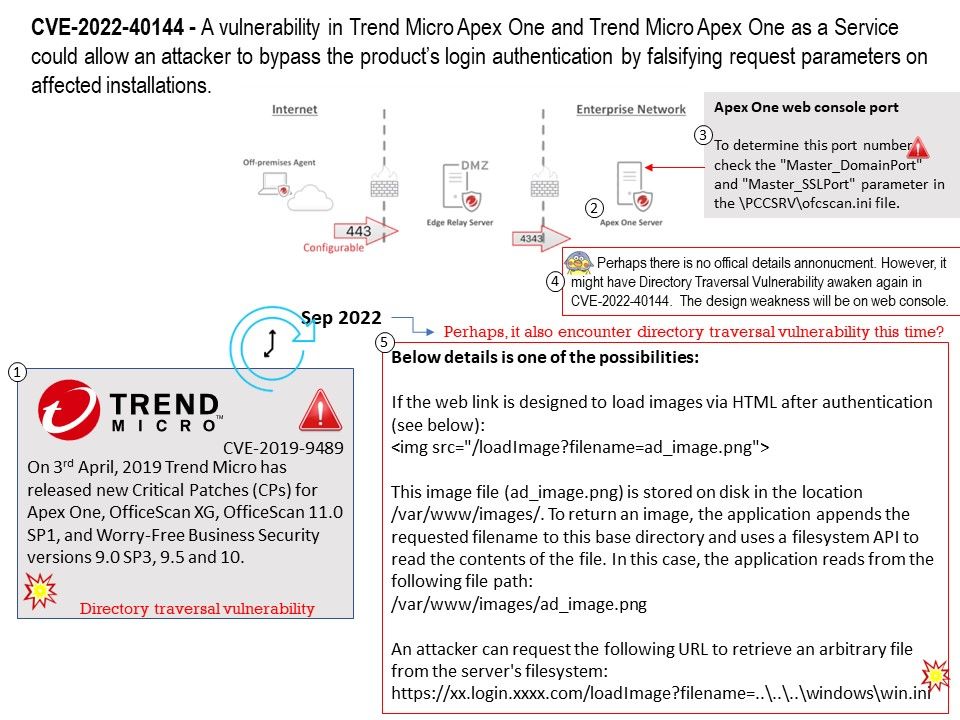
On this discussion, I am focusing on CVE-2022-40144. On 2019, Directory Traversal Vulnerability discovered in Trend Micro Apex One, OfficeScan and Worry-Free Business Security. Since the vulnerability details annouce by vendor lure my interested. Perhaps there is no offical details annonucment. However, it might have Directory Traversal Vulnerability awaken again in CVE-2022-40144. The design weakness will be on web console.
Vulnerability details: CVE-2022-40144 – A vulnerability in Trend Micro Apex One and Trend Micro Apex One as a Service could allow an attacker to bypass the product’s login authentication by falsifying request parameters on affected installations.
Remark: Trend Micro has released a new Service Pack for Trend Micro Apex One (On Premise) and Critical Patches for Apex One as a Service (SaaS) that resolve multiple vulnerabilities in the product.
Zero-Day-Initiative – CVE-2022-40140, CVE-2022-40142 and CVE-2022-40143
Remedy: To address multiple vulnerabilities in their product, follow their recommendations for fixes. For details, please refer to the following link for reference.
https://success.trendmicro.com/dcx/s/solution/000291528?language=en_US