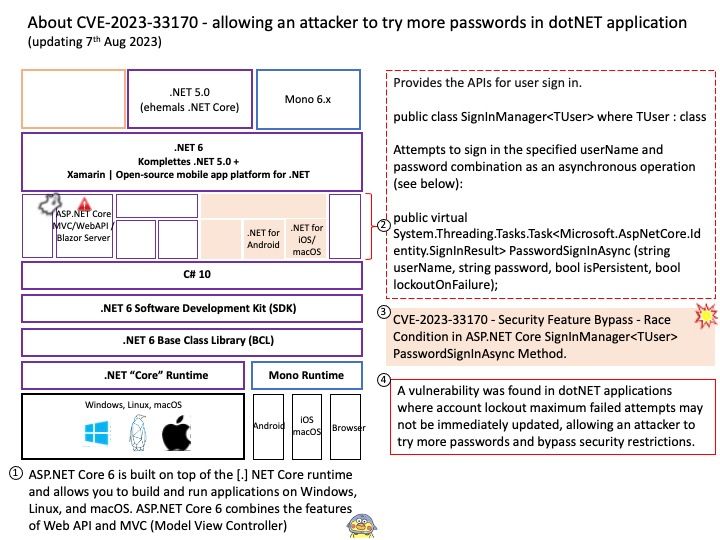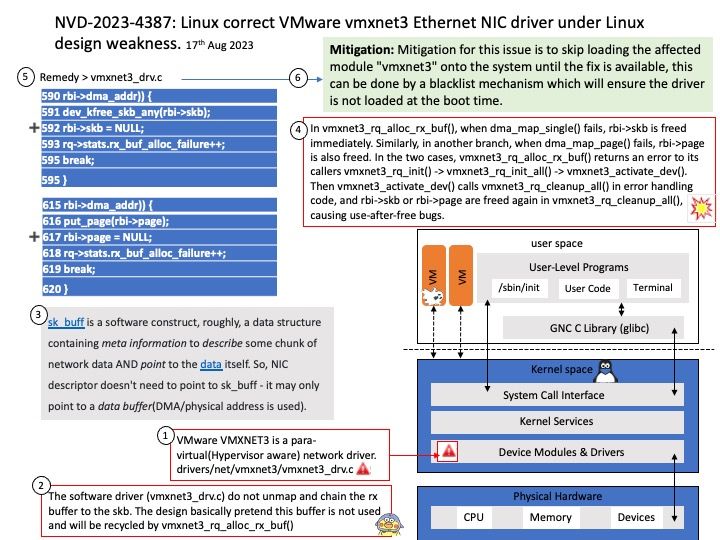
Background: VMware VMXNET3 is a para-virtual(Hypervisor aware) network driver. The goal to designed and developed to address the network complexities in a virtualized infrastructure. A para-virtual driver is a high-performance driver that significantly reduces the overhead caused by the emulation of the corresponding physical device. VMXNET3 is aware of the hypervisor and does not require an emulation layer, thereby enhancing the performance by almost 20% and reducing the overall CPU consumption.
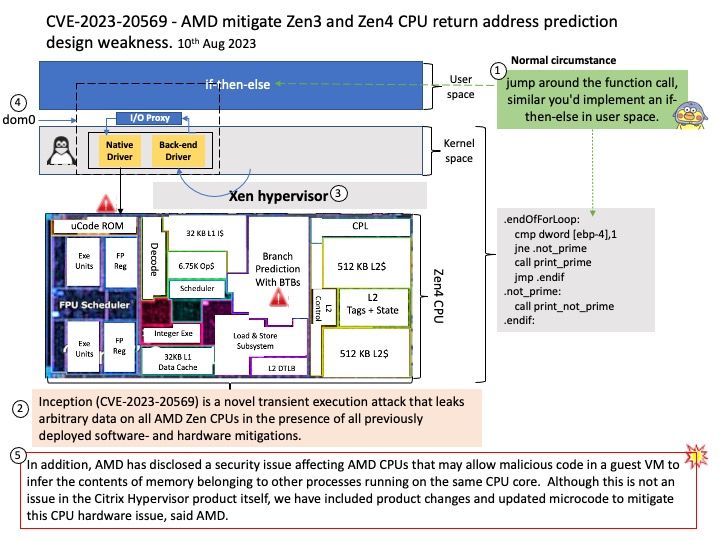
Vulnerability details: A use-after-free flaw was found in vmxnet3_rq_alloc_rx_buf in drivers/net/vmxnet3/vmxnet3_drv[.]c in VMware’s vmxnet3 ethernet NIC driver in the Linux Kernel. This issue could allow a local attacker to crash the system due to a double-free while cleaning up vmxnet3_rq_cleanup_all, which could also lead to a kernel information leak problem.
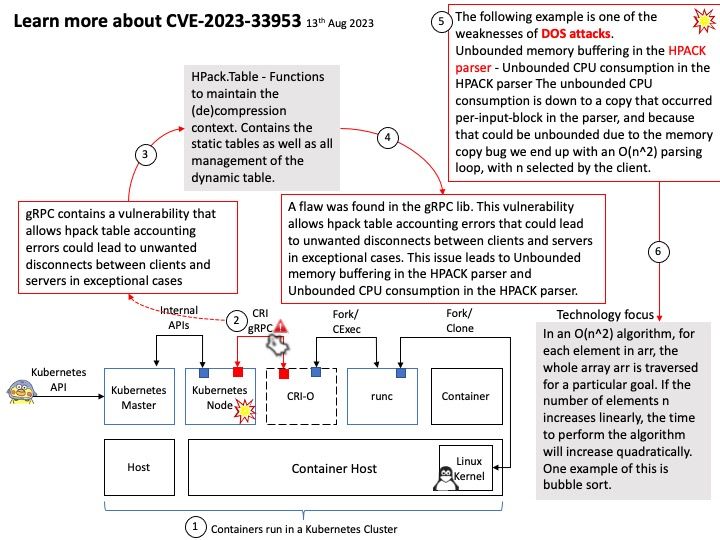
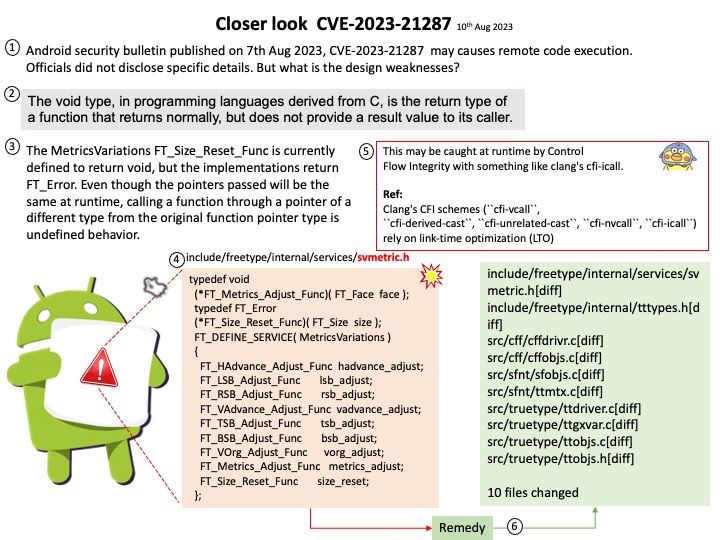
Mitigation: Mitigation for this issue is to skip loading the affected module “vmxnet3” onto the system until the fix is available, this can be done by a blacklist mechanism which will ensure the driver is not loaded at the boot time.
Official announcement: For details, please refer to the link – https://nvd.nist.gov/vuln/detail/CVE-2023-4387