Preface: A system call is a way for programs to interact with the operating system. A computer program makes a system call when it makes a request to the operating system’s kernel. System call provides the services of the operating system to the user programs via Application Program Interface(API).
The ioctl() system call manipulates the underlying device parameters of special files.
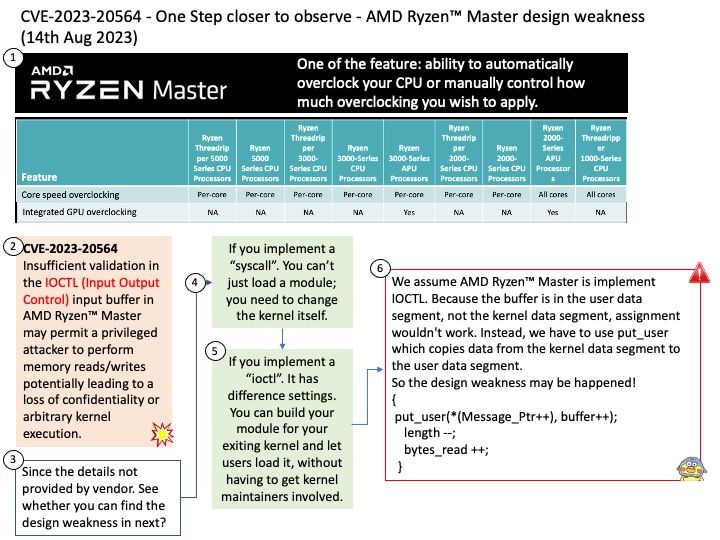
Background: The AMD Ryzen™ Master Monitoring SDK is a public distribution that allows software developers to add processor and memory functions to their own utility in conjunction with AMD Ryzen™ and AMD Ryzen™ Threadripper™ processor products.
All AMD Ryzen CPUs are overclock-ready so you can skip checking if your processor supports overclocking if you have a Ryzen laptop. However, you do still need to check if your motherboard supports overclocking. Ryzen supplies its own overclocking utility called Ryzen Master.
Vulnerability details: Insufficient validation in the IOCTL (Input Output Control) input buffer in AMD RyzenTM Master may permit a privileged attacker to perform memory reads and writes, potentially leading to a loss of confidentiality or arbitrary kernel execution.
Official announcement: For details, please refer to below links
(Amazon Linux Security Center) – https://explore.alas.aws.amazon.com/CVE-2023-20564.html
(AMD Security Bulletin) – https://www.amd.com/en/resources/product-security/bulletin/amd-sb-7004.html