Preface: To be or not to be, AMD is not aware of any exploit of “CVE-2023-20569” outside of the research environment in this moment.
Background: There are 2 phenomena that enable an unprivileged attacker to leak arbitrary information on AMD Zen3 and Zen4 CPU products.
- Phantom speculation – Trigger misprediction without any branch at the source of the misprediction.
- Training in Transient Execution – Potential manipulate future mispredictions through a previous misprediction that attacker trigger.
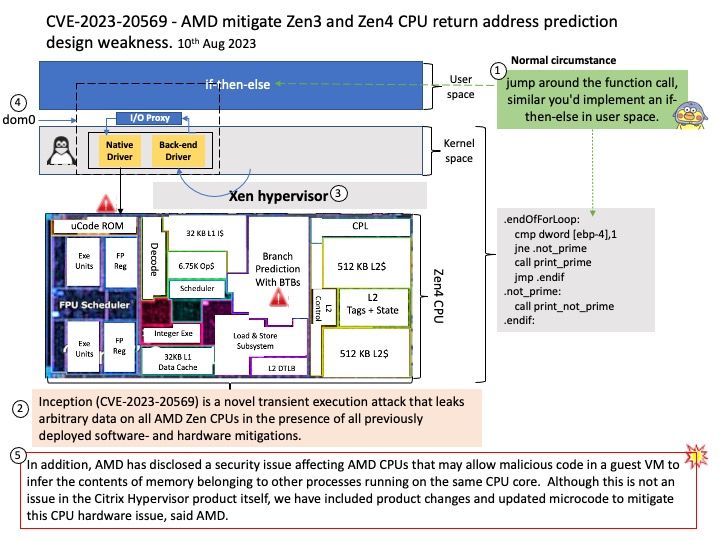
Vulnerability details: A side channel vulnerability in some of the AMD CPUs may allow an attacker to influence the return address prediction. This may result in speculative execution at an attacker-controlled instruction pointer register, potentially leading to information disclosure. Inception (CVE-2023-20569) is a novel transient execution attack that leaks arbitrary data on all AMD Zen CPUs in the presence of all previously deployed software- and hardware mitigations.
Furthermore, AMD has disclosed a security issue affecting AMD CPUs that may allow malicious code in a guest VM to infer the contents of memory belonging to other processes running on the same CPU core. Although this is not an issue in the Citrix Hypervisor product itself, AMD have included product changes and updated microcode to mitigate this CPU hardware issue.
Remark: Citrix XenServer is an open source server virtualization platform based on the Xen hypervisor.
Official announcement: Citrix Hypervisor Security Bulletin for CVE-2023-20569. For details, please refer to the link – https://support.citrix.com/article/CTX569353/citrix-hypervisor-security-bulletin-for-cve202320569-cve202334319-and-cve202240982