Preface: A message can be considered a packet of data conforming to a specific protocol that contains information in well defined fields.
Background: MSMQ(Microsoft Message Queuing) provides a distributed and decoupled way of sending and receiving messages between applications. MSMQ acts as a queue manager that easily decides when applications should be isolated and work even if other applications they interact with are down or unavailable.
The Code Block Component is used to extend the functionality of the XML comments <code> tag.
Syntax highlighting of code blocks in <code> tags. Languages supported include C#, VB[.]NET, JScript[.]NET, C++, J#, C, JavaScript, VBScript, XAML, XML, HTML, SQL script, Python, PowerShell script, and batch file script.
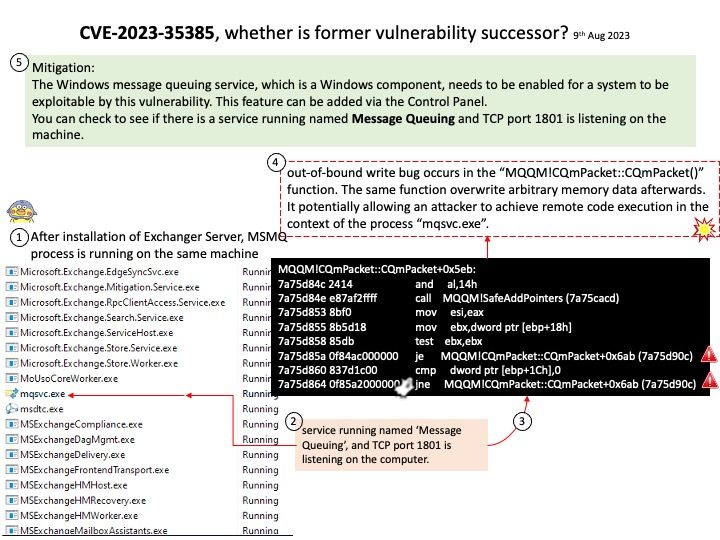
Vulnerability details: A remote unauthenticated attacker can exploit this vulnerability by sending malicious MSMQ packets to a vulnerable MSMQ server leading to arbitrary code execution. However, in order to exploit this flaw, the Message Queuing service needs to be enabled on the vulnerable server. Microsoft says if the service is enabled, it runs under the service name “Message Queuing” and is listening on TCP port 1801.
Messages can have no more than 4 MB of data. This restriction is due to the memory mapped files used by Message Queuing to store the message data. These memory-mapped files are stored in the MSMQ\Storage folder on the computer where the queue resides.
Official announcement: For details, please refer to the link – https://nvd.nist.gov/vuln/detail/CVE-2023-35385
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2023-35385