Background: gRPC is a powerful open source RPC (Remote Procedure Call) framework for building scalable and fast APIs. It allows client and server applications to communicate transparently and develop connected systems. Many leading tech companies have adopted gRPC.
Vulnerability details:
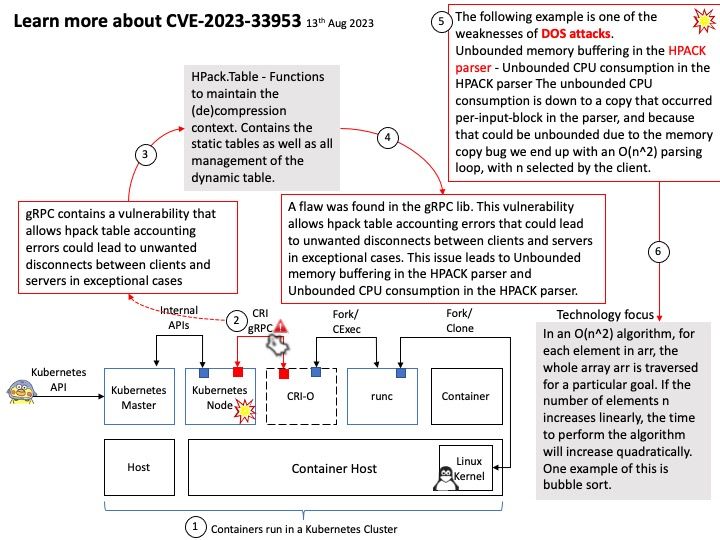
Three vectors were found that allow the following DOS attacks:
– Unbounded memory buffering in the HPACK parser – Unbounded CPU consumption in the HPACK parser The unbounded CPU consumption is down to a copy that occurred per-input-block in the parser, and because that could be unbounded due to the memory copy bug we end up with an O(n^2) parsing loop, with n selected by the client.
The unbounded memory buffering bugs:
– The header size limit check was behind the string reading code, so we needed to first buffer up to a 4 gigabyte string before rejecting it as longer than 8 or 16kb.
– HPACK varints have an encoding quirk whereby an infinite number of 0’s can be added at the start of an integer. gRPC’s hpack parser needed to read all of them before concluding a parse.
– gRPC’s metadata overflow check was performed per frame, so that the following sequence of frames could cause infinite buffering: HEADERS: containing a: 1 CONTINUATION: containing a: 2 CONTINUATION: containing a: 3 etc…
RedHat Official announcement: Openshift uses gRPC lib with Kuryr component. In Openshift, Kuryr is not configured to run the code using gRPC lib. Hence, The impact for Openshift is set to moderate. For details, please refer to the link – https://access.redhat.com/security/cve/cve-2023-33953