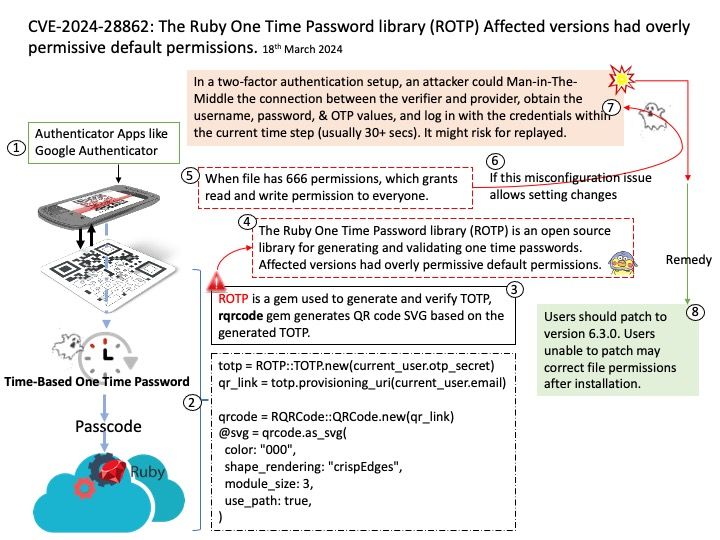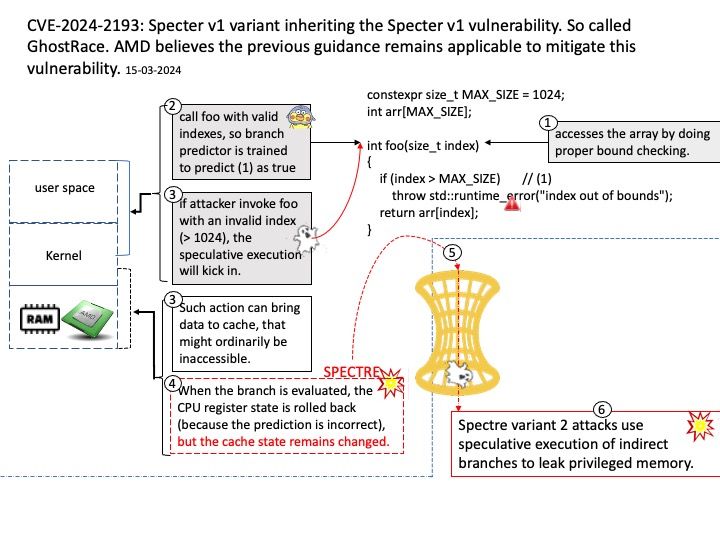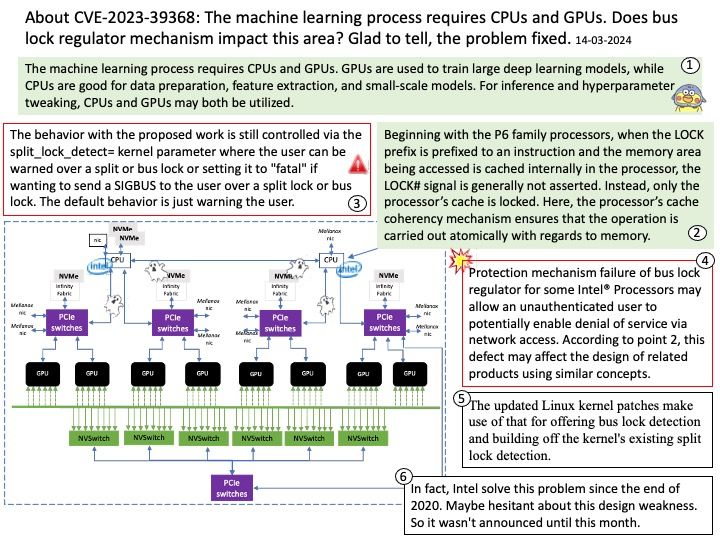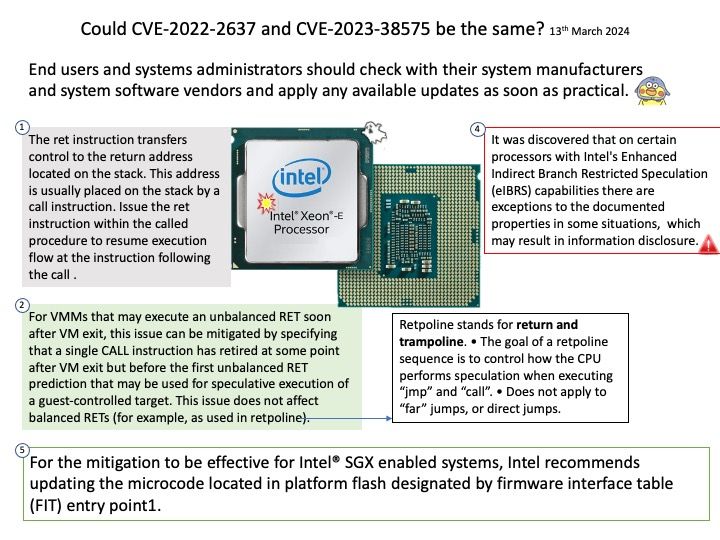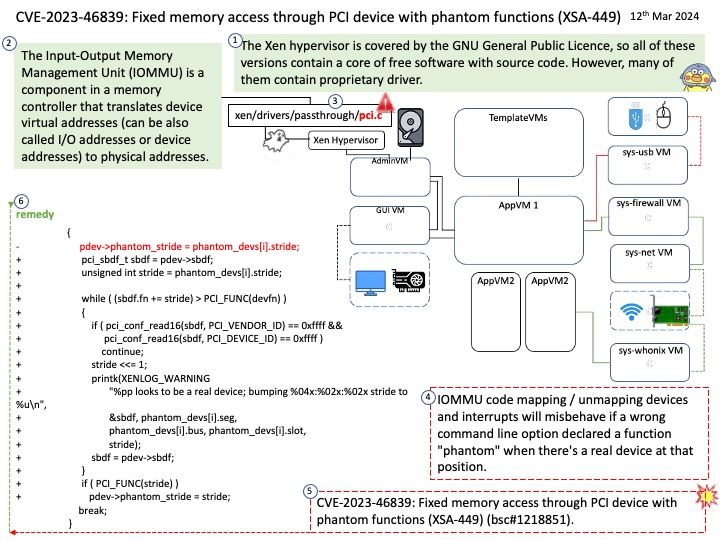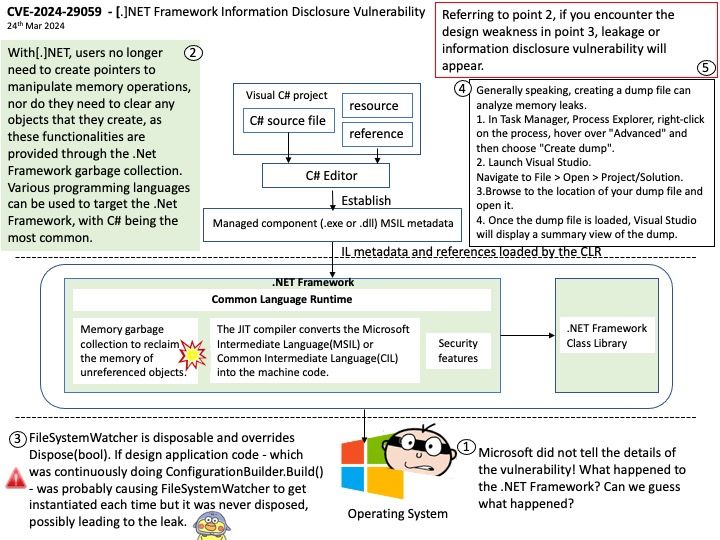
Preface: Microsoft did not tell the details of the vulnerability! What happened to the .NET Framework? Can we guess what happened?
[.]NET is a platform framework. Currently, there are two types: the [.]NET Framework exclusive to the Windows platform and the cross-platform .NET Core.
Background: The [.]NET Framework works with applications developed in C#, F#, or Visual Basic and compiled to Common Intermediate Language (CIL). The Common Language Runtime (CLR) runs [.]NET applications on a given machine, converting the CIL to machine code.
The Common Language Runtime (CLR), the virtual machine component of Microsoft .NET Framework, manages the execution of .NET programs
Vulnerability details: [.]NET Framework Information Disclosure Vulnerability
Official announcement: Please see the link below for details –
https://nvd.nist.gov/vuln/detail/CVE-2024-29059
If you are interested in my speculation, please see the attached picture.