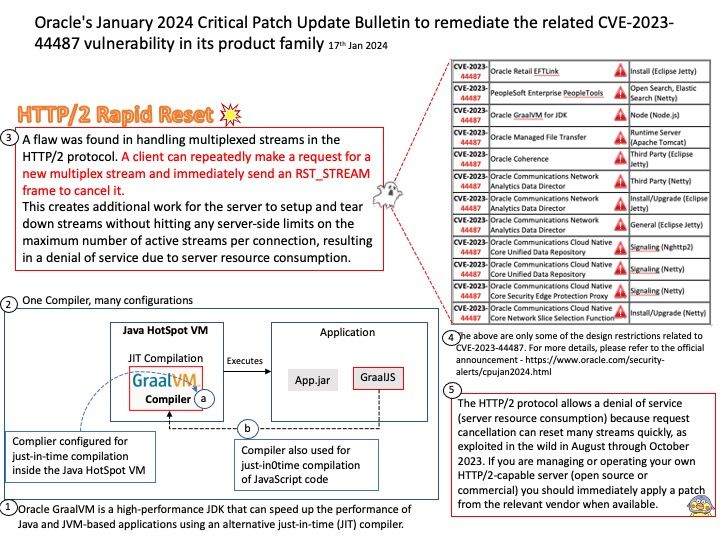
Preface: HTTP/2 Rapid Reset, based on stream multiplexing. HTTP/2 Rapid Reset attacks mostly affect the large infrastructure providers. Software smaller providers use, such as NGINX, Apache Server, ….etc
Background: Oracle GraalVM is a high-performance JDK that can speed up the performance of Java and JVM-based applications using an alternative just-in-time (JIT) compiler.
Vulnerability details: The HTTP/2 protocol allows a denial of service (server resource consumption) because request cancellation can reset many streams quickly, as exploited in the wild in August through October 2023.
If you are managing or operating your own HTTP/2-capable server (open source or commercial) you should immediately apply a patch from the relevant vendor when available.
Official announcement: Please refer to the link for details – https://www.oracle.com/security-alerts/cpujan2024.html
The patch for CVE-2023-44487 also addresses CVE-2023-36478, CVE-2023-40167, CVE-2023-42794, CVE-2023-42795, and CVE-2023-45648.
The patch for CVE-2023-44487 also addresses CVE-2023-45143.
The patch for CVE-2023-45648 also addresses CVE-2023-42794, CVE-2023-42795, and CVE-2023-44487.
The patch for CVE-2023-44487 also addresses CVE-2023-36478.