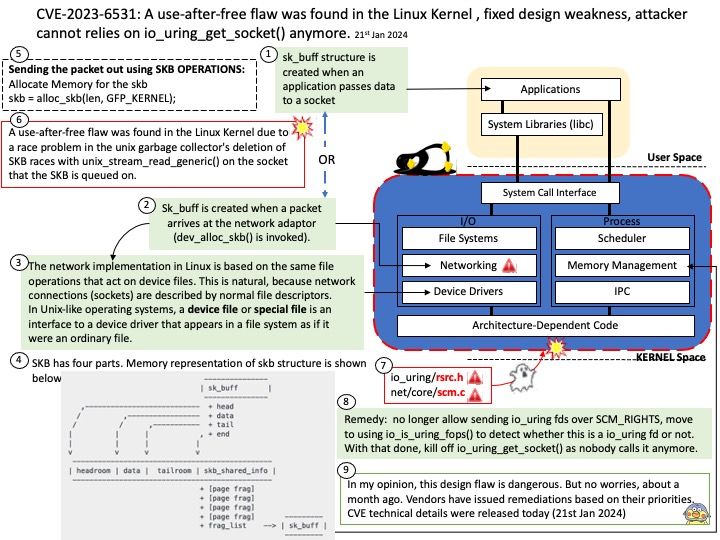
Preface: In my opinion, this design flaw is dangerous. But no worries, about a month ago. Vendors have issued remediations based on their priorities. CVE technical details were released today (21st Jan 2024).
Background: io_uring is applicable to most businesses and applications with a demand for asynchronous I/O. As of now, io_uring has been integrated into multiple mainstream open-source applications, such as RocksDB, Netty, QEMU, SPDK, PostgreSQL, MariaDB, etc.
What is io_uring? io_uring is an asynchronous I/O interface for the Linux kernel. An io_uring is a pair of ring buffers in shared memory that are used as queues between user space and the kernel:
Submission queue (SQ): A user space process uses the submission queue to send asynchronous I/O requests to the kernel.
Completion queue (CQ): The kernel uses the completion queue to send the results of asynchronous I/O operations back to user space.
Many io_uring features will soon be available in Red Hat Enterprise Linux 9.3, which ships with core version 5.14. Fedora 37 currently provides the latest io_uring functionality.
Vulnerability details: A use-after-free flaw was found in the Linux Kernel due to a race problem in the unix garbage collector’s deletion of SKB races with unix_stream_read_generic() on the socket that the SKB is queued on.
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2023-6531