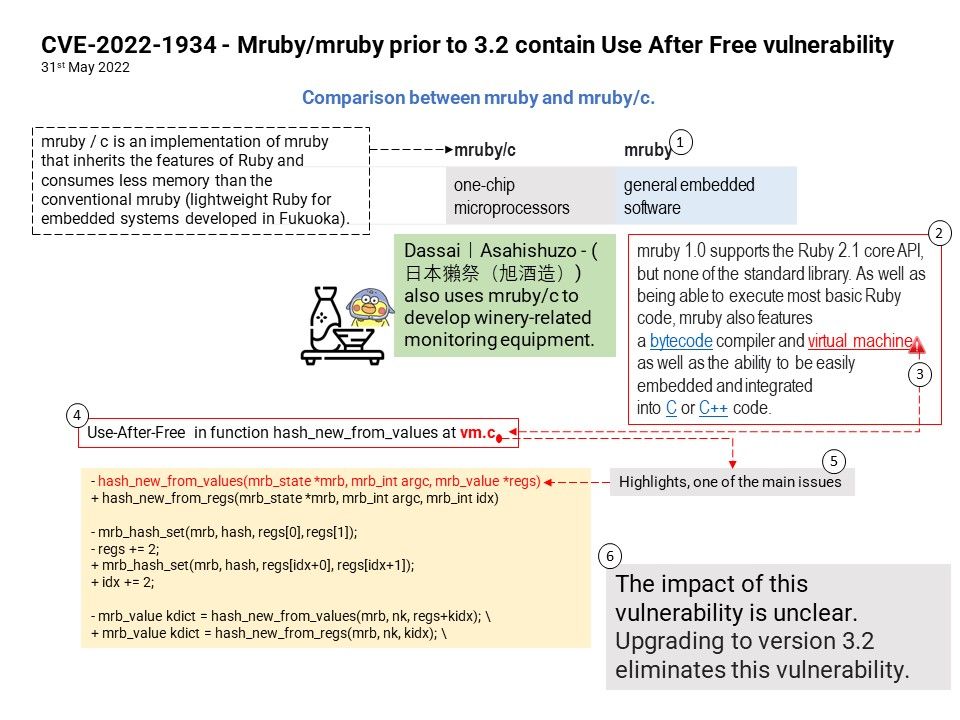
Preface: mruby or mruby/c, mruby / c is an implementation of mruby that inherits the features of Ruby and consumes less memory than the conventional mruby (lightweight Ruby for embedded systems developed in Fukuoka).
Dassai|Asahishuzo – (日本獺祭(旭酒造)) also uses mruby/c to develop winery-related monitoring equipment.
Background: mruby is a Fukuoka-developed programming language for embedded software. It’s a version of the high-efficiency development language “Ruby” that has been lightened in order to use less memory, making it suitable for embedded software.
It works using 1/4 the amount of code that C languages do and because it is also highly readable, some of its strengths are high productivity, easy trial-and-error debugging and maintenance, and it’s simple to learn.
Vulnerability details: Mruby/mruby prior to 3.2 contain Use After Free vulnerability. Use-After-Free in function hash_new_from_values in Mruby/mruby.
Remedy: The impact of this vulnerability is unclear. Upgrading to version 3.2 eliminates this vulnerability.
Official announcement: https://github.com/mruby/mruby/commit/aa7f98dedb68d735a1665d3a289036c88b0c47ce