Preface:If the operating system itself contains unknown technical matter. When 3rd party application installed, a vulnerability merely encounter on the specified software. Do you think operating system vendor should do the remedy? Or third party vendor take the responsibility?
Background: Cybersecurity related to functional safety will be included Powergrid, public facilities and manufacturing industry. SCADA systems are used in many different industries to collect and analyze real-time data, as well as to control functions, which makes them a target to malicious hackers.
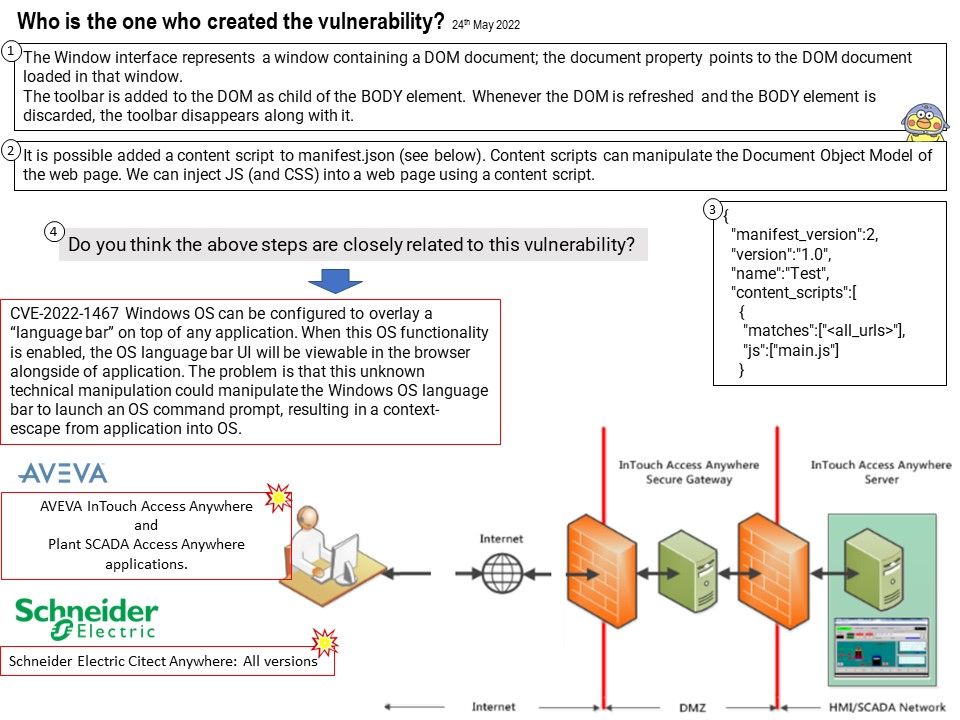
AVEVA InTouch Access Anywhere enables you to remotely view a running InTouch application from a desktop computer or a mobile device including tablets, smartphones, or laptops. You view and control the application through a secure web browser without requiring a separate client application.
InTouch Access Anywhere provides the following features:
– Provides secure and remote access to InTouch applications.
– Incorporates image compression, packet shaping, and whole frame rendering to improve Internet performance.
– Automatically adjusts the size of your InTouch Access Anywhere session to the web browser window showing the application.
– Supports finger gestures on touch screen devices.
– Works on devices that only support web applications like Chromebooks
– Provides an expandable session toolbar with icons to disconnect your InTouch Access Anywhere sessions, access system keys, and copy application data to your Windows clipboard.
Vulnerability details: Certain versions of AVEVA InTouch Access Anywhere from AVEVA contain the following vulnerability:
Windows OS can be configured to overlay a “language bar” on top of any application. When this OS functionality is enabled, the OS language bar UI will be viewable in the browser alongside the AVEVA InTouch Access Anywhere and Plant SCADA Access Anywhere applications. It is possible to manipulate the Windows OS language bar to launch an OS command prompt, resulting in a context-escape from application into OS.
Remedy:
Application Software Vendor Security Updates – https://www.aveva.com/en/support-and-success/cyber-security-updates/
ICS Advisory (ICSA-22-130-05) – https://www.cisa.gov/uscert/ics/advisories/icsa-22-130-05