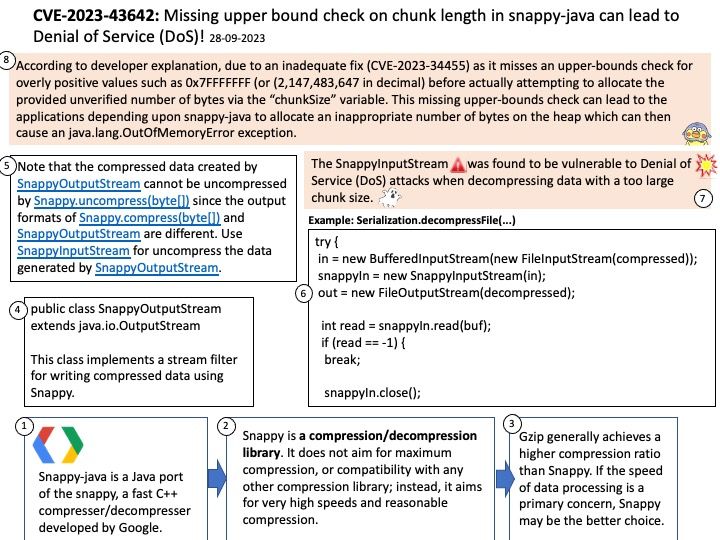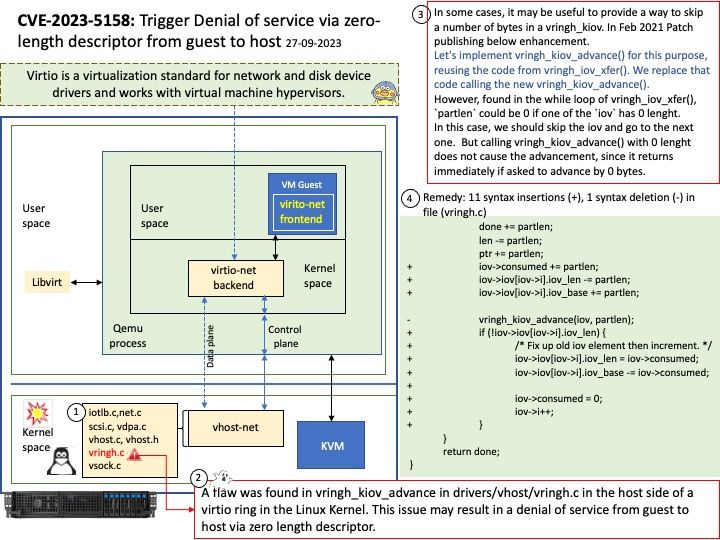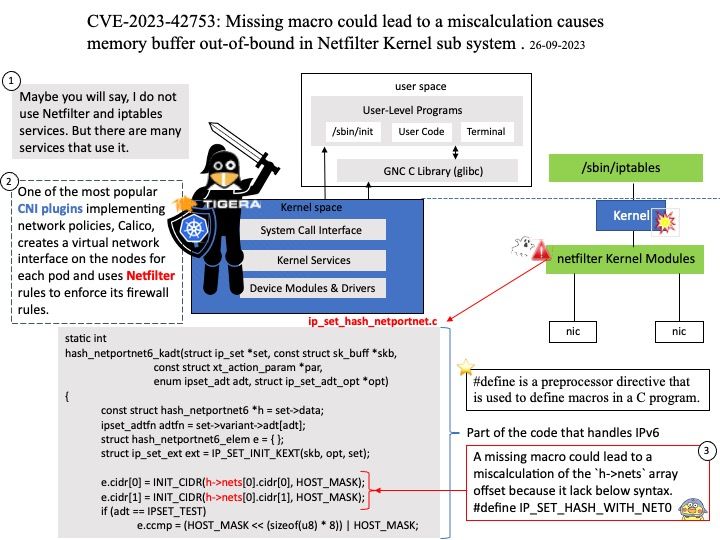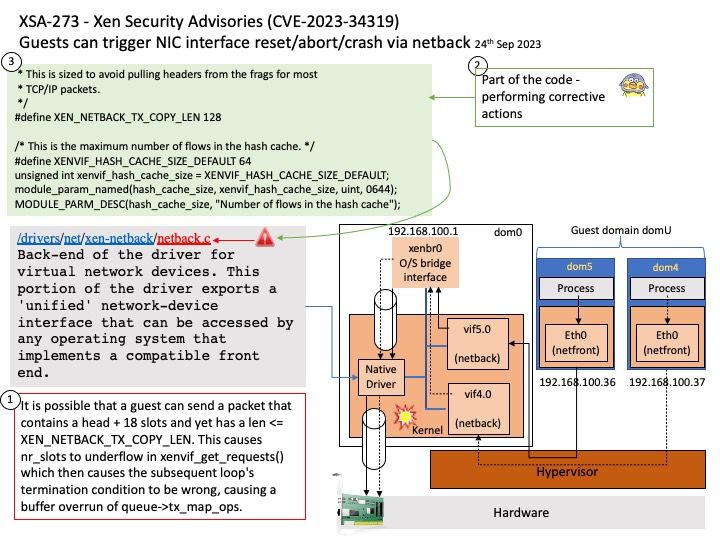
Preface: Smartphone is a digital world microcosm. We know that our digital world includes web services, repositories, virtual machines, high-speed networks, multi-core CPUs, and GPUs. But the average smartphone already includes the infrastructure components just mentioned. Therefore, the security level of smartphones is no less than that of enterprise servers, because this micro world is more strict than you think.
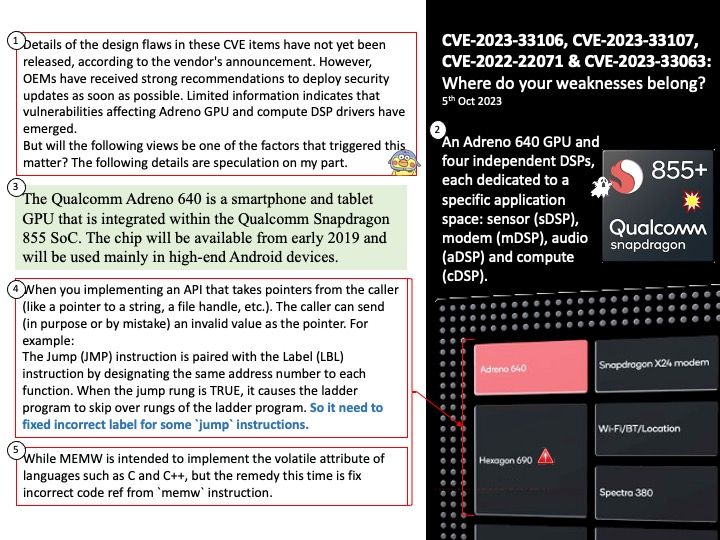
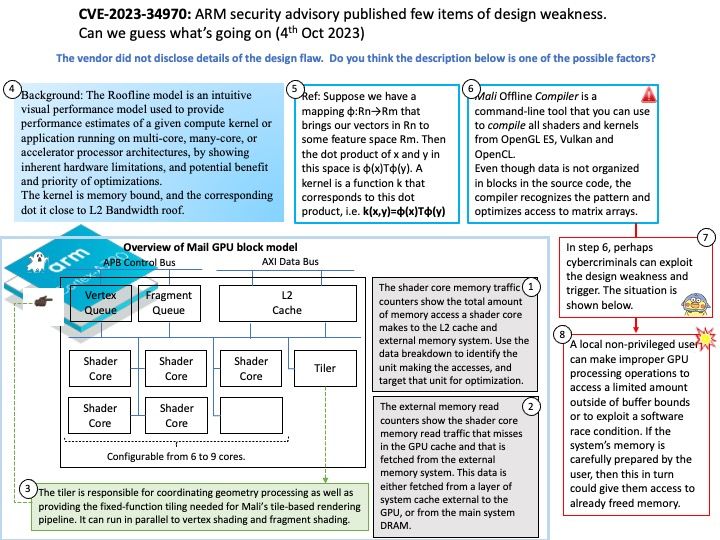
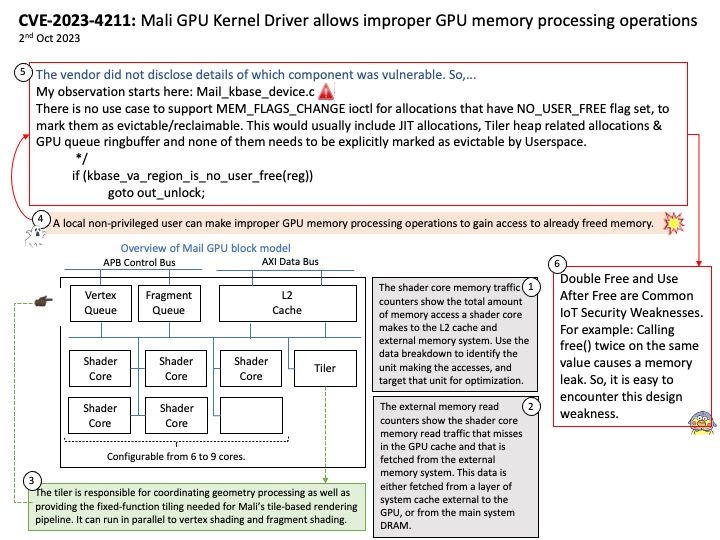
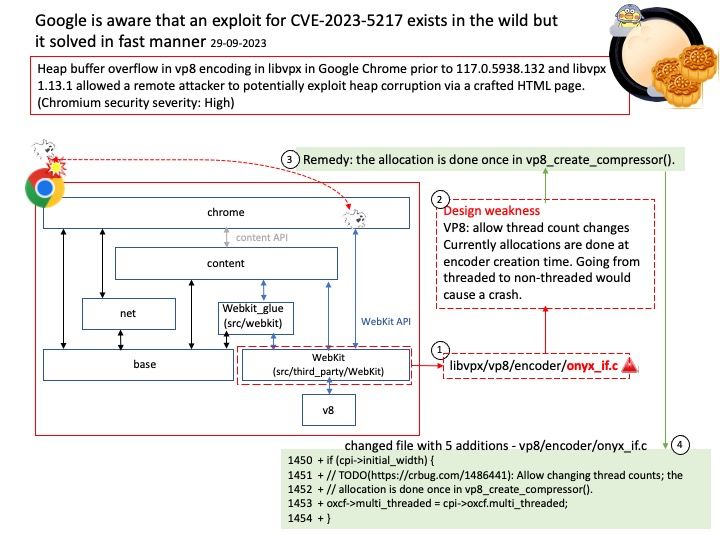
Background: Android 13 builds on the tablet optimizations introduced in Android 12 and the 12L feature drop—including optimizations for the system UI, better multitasking, and improved compatibility modes. AndroidManagerService is the most important service of Android. It is mainly responsible for the startup, switching, scheduling and management of application processes of four components. It plays the role of management process and scheduling module of the operating system.
ActivityManagerService is the process manage and dispatch center in java platform. Furthermore system_server is a system process, it will be included in ActivityManagerService manage scope.
What exactly did ActivityManagerService do when it was constructed? Established execution threads: ServiceThread, mUiHandler, sKillThread, CpuTracker.
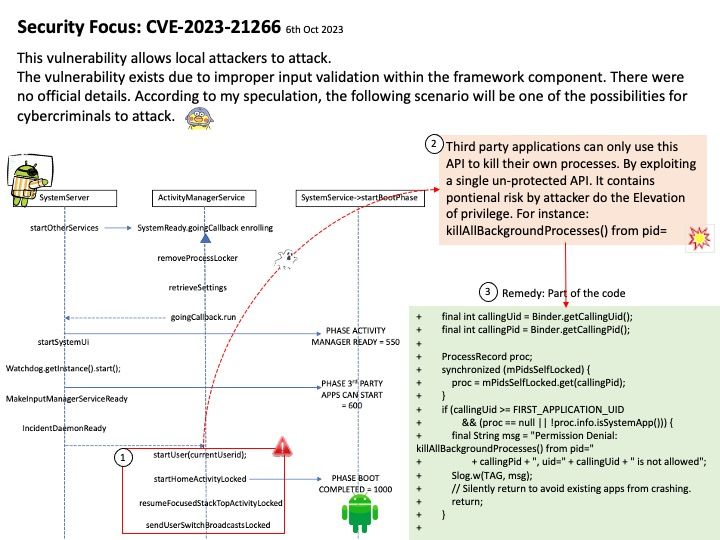
Vulnerability details: CVE-2023-21266 could lead to local escalation of privilege with no additional execution privileges needed.
Affected Android versions: 11, 12, 12L, 13
Vulnerability Type: Elevation of privilege
Official announcement: Please refer to the link for details – https://source.android.com/docs/security/bulletin/2023-10-01