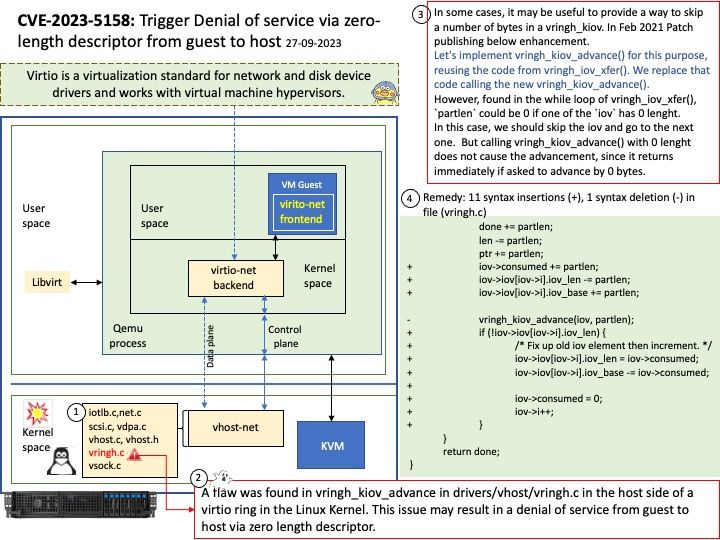
Preface: In the virtio protocol, the host side provides emulation of the device, and the guest side is responsible for driving the device. The relationship between host and guest is the relationship between device and driver. We usually use the method of reading and writing temporary registers to control and drive physical devices, but for emulated devices in virtio, memory organized in the form of virtqueue is used.
Background: Specific to the network devices in virtio, the driver on the guest side is called “virtio-net”. On the host side, the early classic implementation used the QEMU, that is, the user mode program on the host side provides emulation of the device. Called “vhost-user”.
Like KVM, vhost-net cannot be used alone, but must be used with QEMU, because some setting information still needs to be given from QEMU in user mode.
Vulnerability details: A flaw was found in vringh_kiov_advance in drivers/vhost/vringh[.]c in the host side of a virtio ring in the Linux Kernel. This issue may result in a denial of service from guest to host via zero length descriptor.
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2023-5158