Preface: The classes in the java. util. zip package support two widespread compression formats: GZIP and ZIP. Both of these are based on the ZLIB compression algorithm, which is discussed in RFC 1950, RFC 1951, and RFC 1952.
Background: Compression Ratio: Gzip generally achieves a higher compression ratio than Snappy. If storage space is a primary concern, Gzip may be the better choice. Speed: Snappy is designed for speed. If the speed of data processing is a primary concern, Snappy may be the better choice. The snappy-java is a Java port of the snappy, a fast C++ compresser/decompresser developed by Google.
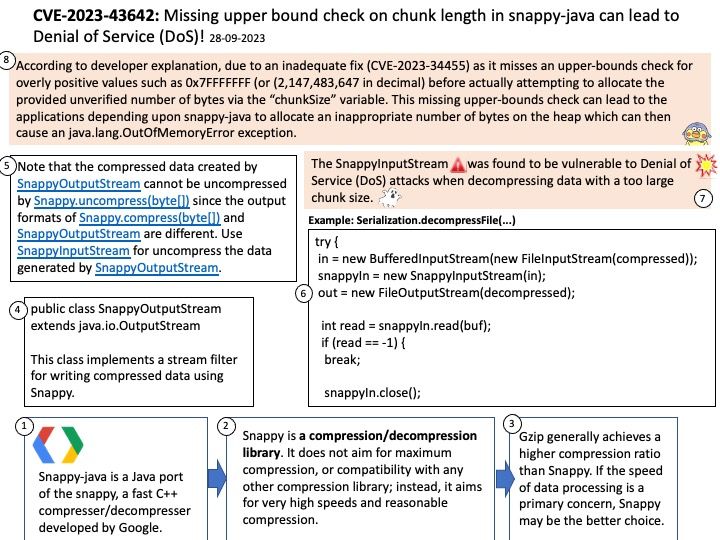
Vulnerability details: The SnappyInputStream was found to be vulnerable to Denial of Service (DoS) attacks when decompressing data with a too large chunk size. Due to missing upper bound check on chunk length, an unrecoverable fatal error can occur.
Impact: All versions of snappy-java including the latest released version 1.1.10.3 are vulnerable to this issue.
Remedy: A fix has been introduced in commit `9f8c3cf74` which will be included in the 1.1.10.4 release. Users are advised to upgrade. Users unable to upgrade should only accept compressed data from trusted sources.
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2023-43642