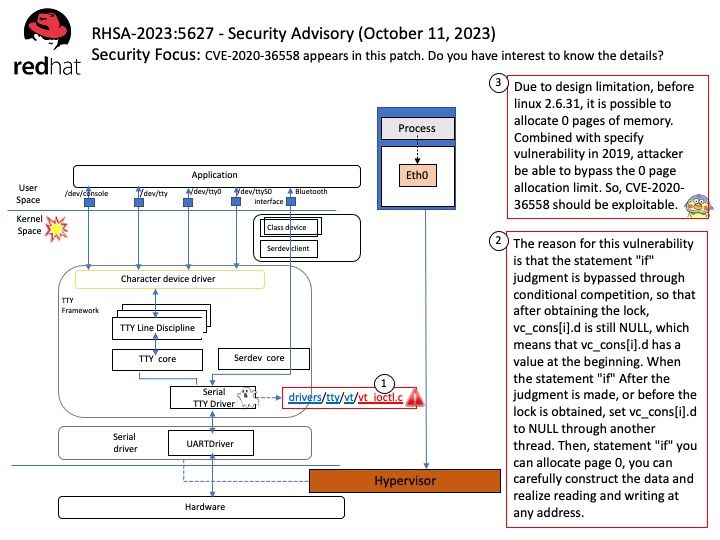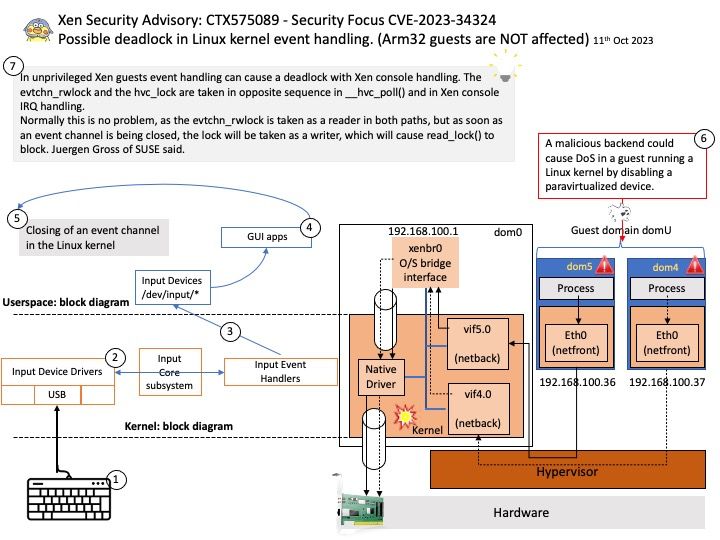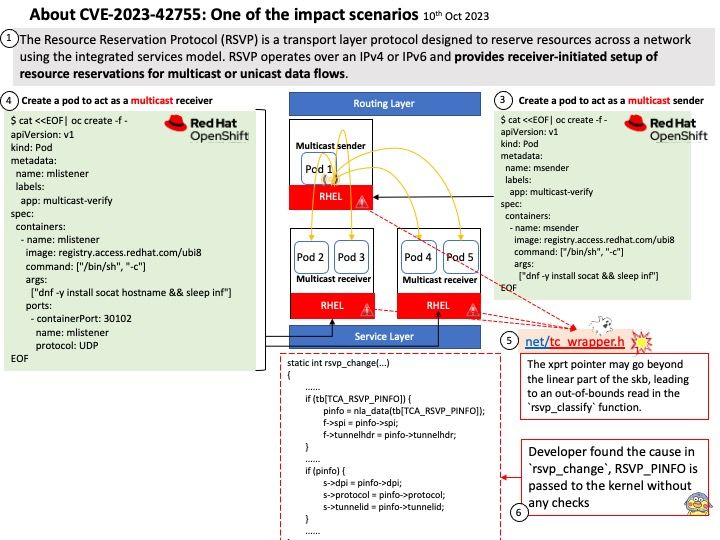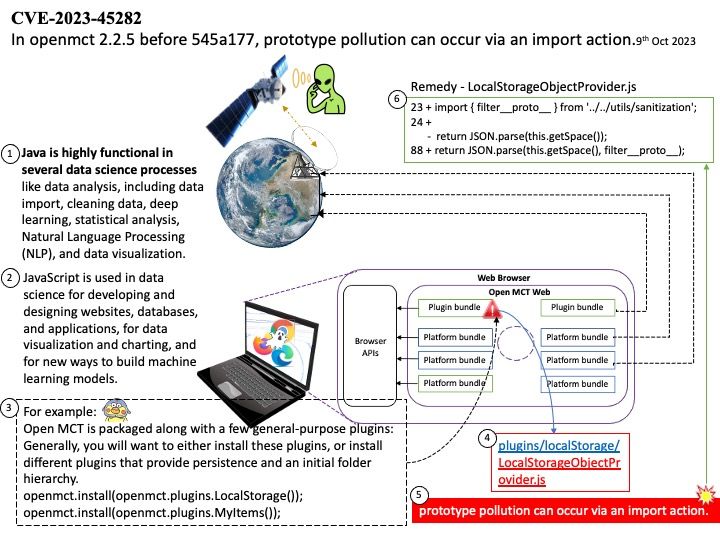
Preface: Infrastructure as code (IaC) is the process of dynamically managing and provisioning infrastructure through code instead of through a manual process to simplify app development, configuration, and runtime. IaC uses DevOps methodology and versioning with a descriptive model to define and deploy infrastructure. For example: Cloud comupting platform structure components includes networks, virtual machines, load balancers, and connection topologies.
Infrastructure as code (IaC) uses DevOps methodology and versioning with a descriptive model to define and deploy infrastructure. For example: Cloud comupting platform structure components includes networks, virtual machines, load balancers, and connection topologies.
Remark: A general example of descriptive modeling is business reporting in the form of graphs, charts, and dashboards.
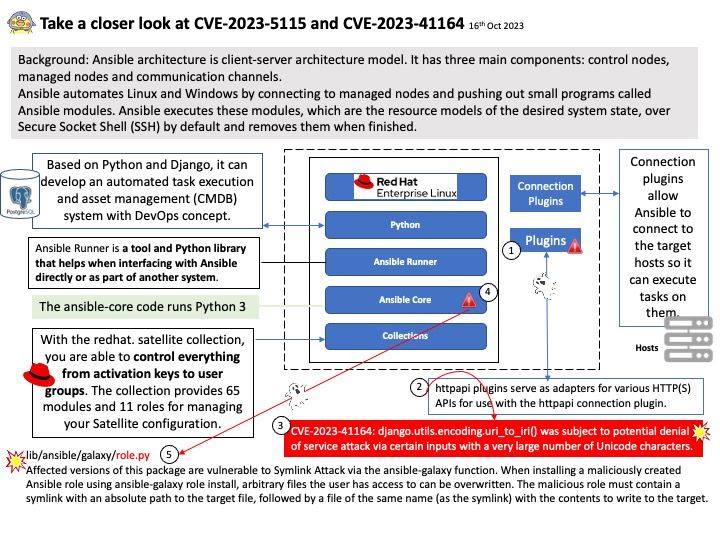
Background: Ansible is an tool for simple automation tasks. Python tool provides more flexibility and control over automation and is an excellent tool for complex automation tasks. Based on Python and Django, it can develop an automated task execution and asset management (CMDB) system with DevOps concept.
Ansible architecture is client-server architecture model. It has three main components: control nodes, managed nodes and communication channels.
Ansible automates Linux and Windows by connecting to managed nodes and pushing out small programs called Ansible modules. Ansible executes these modules, which are the resource models of the desired system state, over Secure Socket Shell (SSH) by default and removes them when finished.
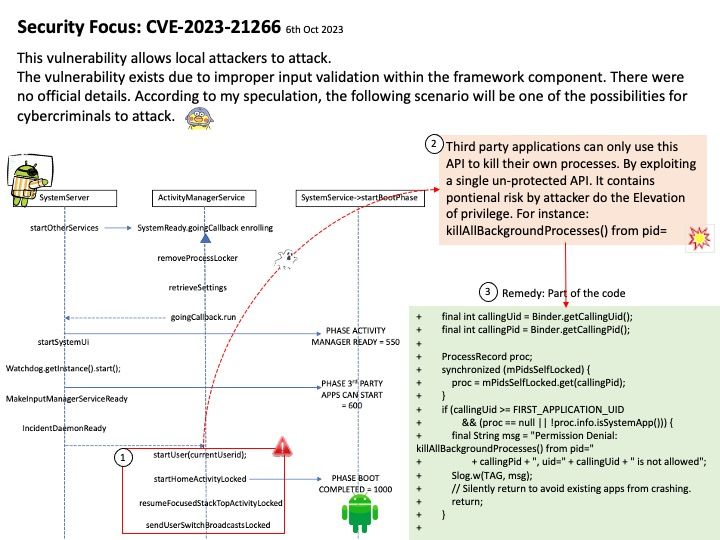
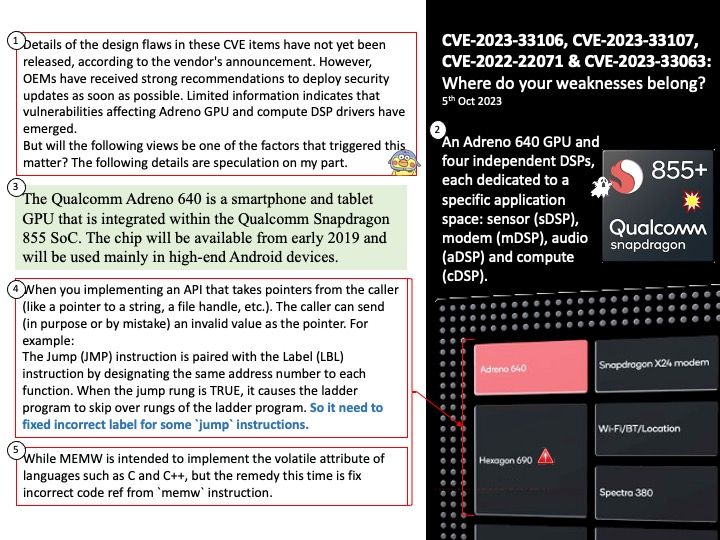
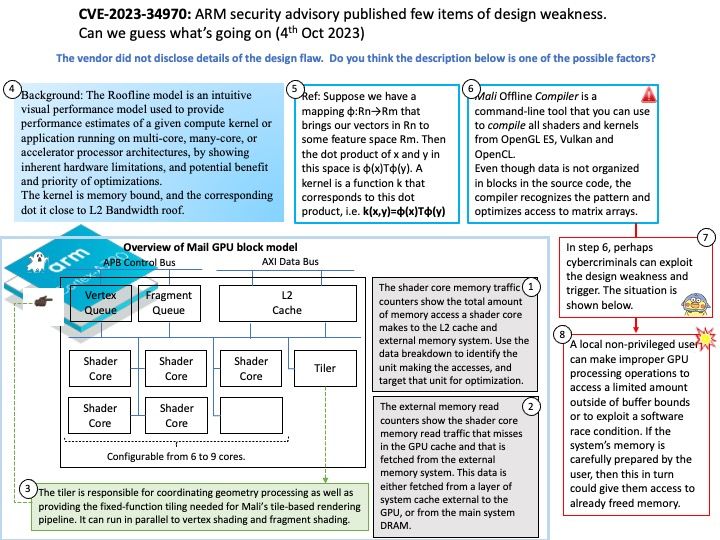
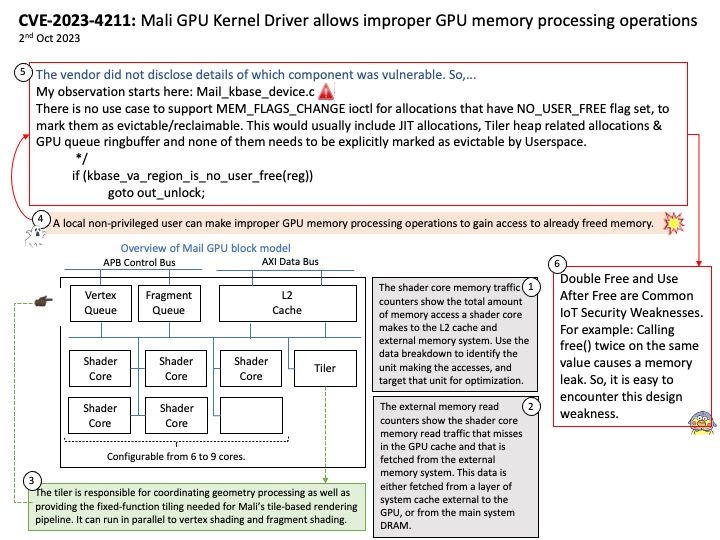
Vulnerability details:
CVE-2023-5115 – ansible-core: malicious role archive can cause ansible-galaxy to overwrite arbitrary files
CVE-2023-41164 – automation-controller: Django: Potential denial of service vulnerability in django.utils.encoding.uri_to_iri()
Official announcement: Please refer to the link for details –