Preface: Double Free and Use After Free are Common IoT Security Weaknesses.
For example: Calling free() twice on the same value causes a memory leak. So, it is easy to encounter this design weakness.
Background: Arm Mali-G720, is designed on the Arm 5th Gen architecture to deliver improved performance while reducing memory bandwidth usage, power consumption, and CPU load. Even more powerful than its predecessor, the Mali-G715 GPU, Mali-G720 takes full advantage of advanced GPU technologies that can power immersive games and intelligent AI applications across a broad range of devices.
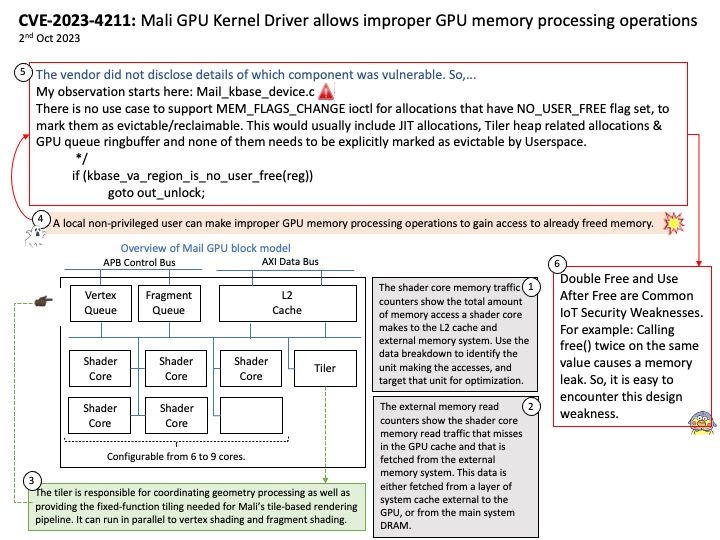
Vulnerability details: A local non-privileged user can make improper GPU memory processing operations to gain access to already freed memory.
Impact will occur on these specific products:
Midgard GPU Kernel Driver: All versions from r12p0 – r32p0
Bifrost GPU Kernel Driver: All versions from r0p0 – r42p0
Valhall GPU Kernel Driver: All versions from r19p0 – r42p0
Arm 5th Gen GPU Architecture Kernel Driver: All versions from r41p0 – r42p0
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2023-4211