Preface: Netfilter is an infrastructure; it is the basic API that the Linux 2.4 kernel offers for applications that want to view and manipulate network packets.
Background: It can not only block unwanted traffic but also block malicious software from infecting the system. In the Linux ecosystem, iptables is a popular firewall that interfaces with the netfilter framework on the Linux kernel. Most of the modern Linux systems come with these tools pre-built.
Tables and Chains in Iptables, inside each table of iptables, rules are further organized within separate “chains”. While the table represents the type of rules they are holding, the chains describe the netfilter hooks that trigger the rules. In short, chains determine when the rule will be evaluated.
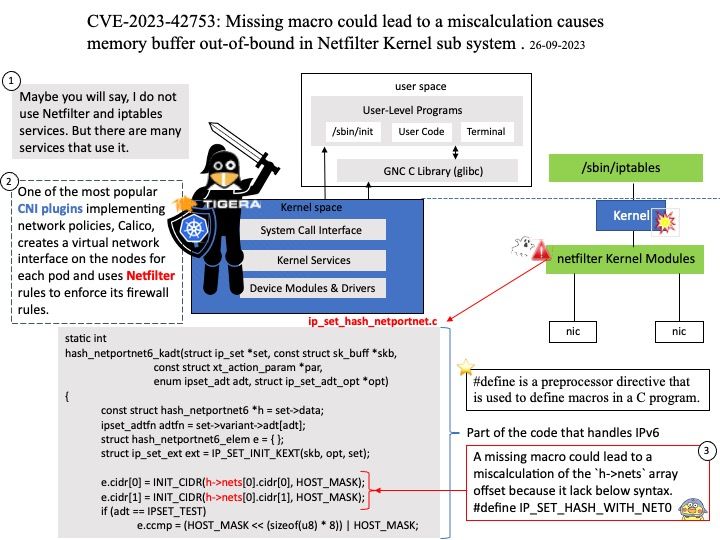
One of the most popular CNI plugins implementing network policies, Calico, creates a virtual network interface on the nodes for each pod and uses Netfilter rules to enforce its firewall rules.
Ref: Calico has emerged as one of the most popular CNI plugins for Kubernetes cluster networking.
Vulnerability details: An array indexing vulnerability was found in the netfilter subsystem of the Linux kernel. A missing macro could lead to a miscalculation of the `h->nets` array offset, providing attackers with the primitive to arbitrarily increment/decrement a memory buffer out-of-bound. This issue may allow a local user to crash the system or potentially escalate their privileges on the system.
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2023-42753