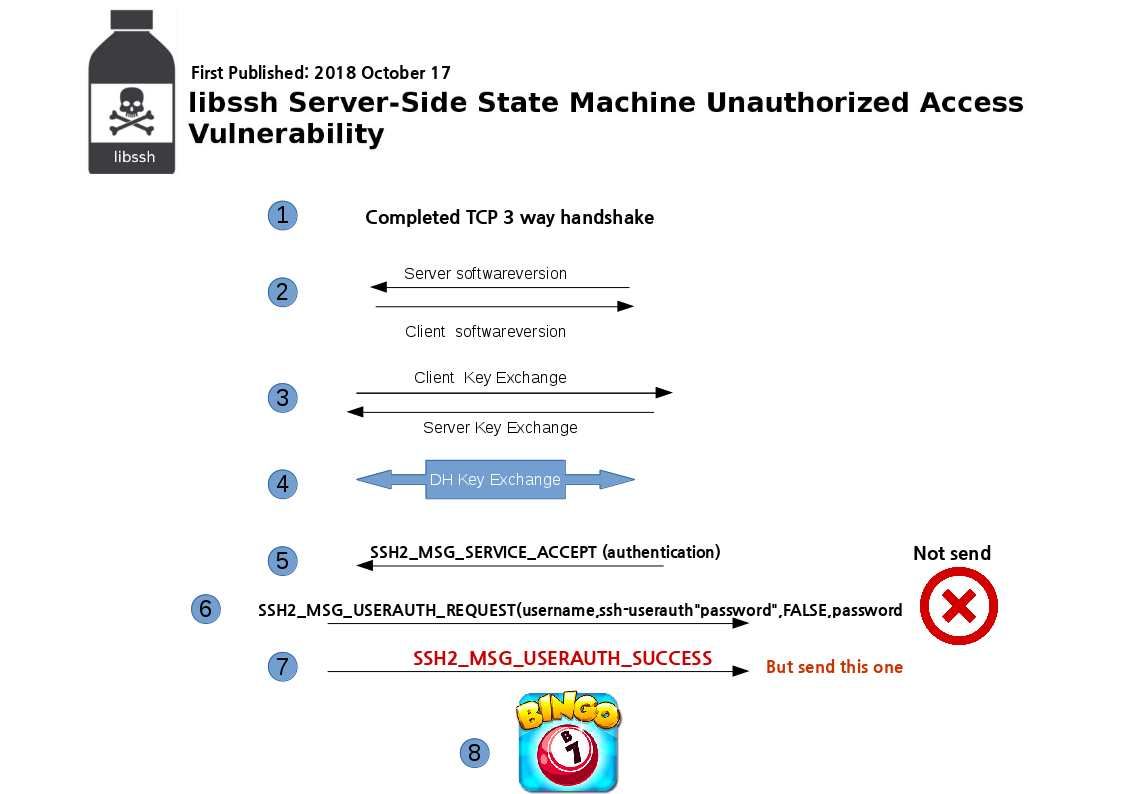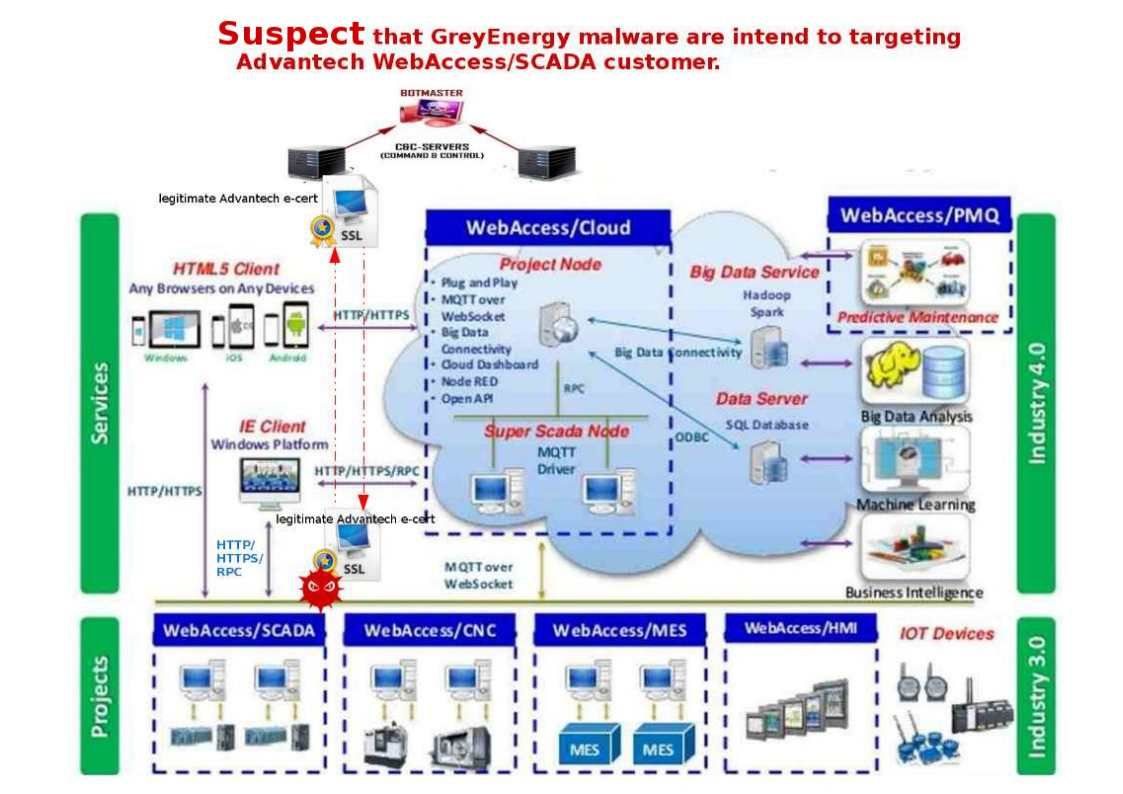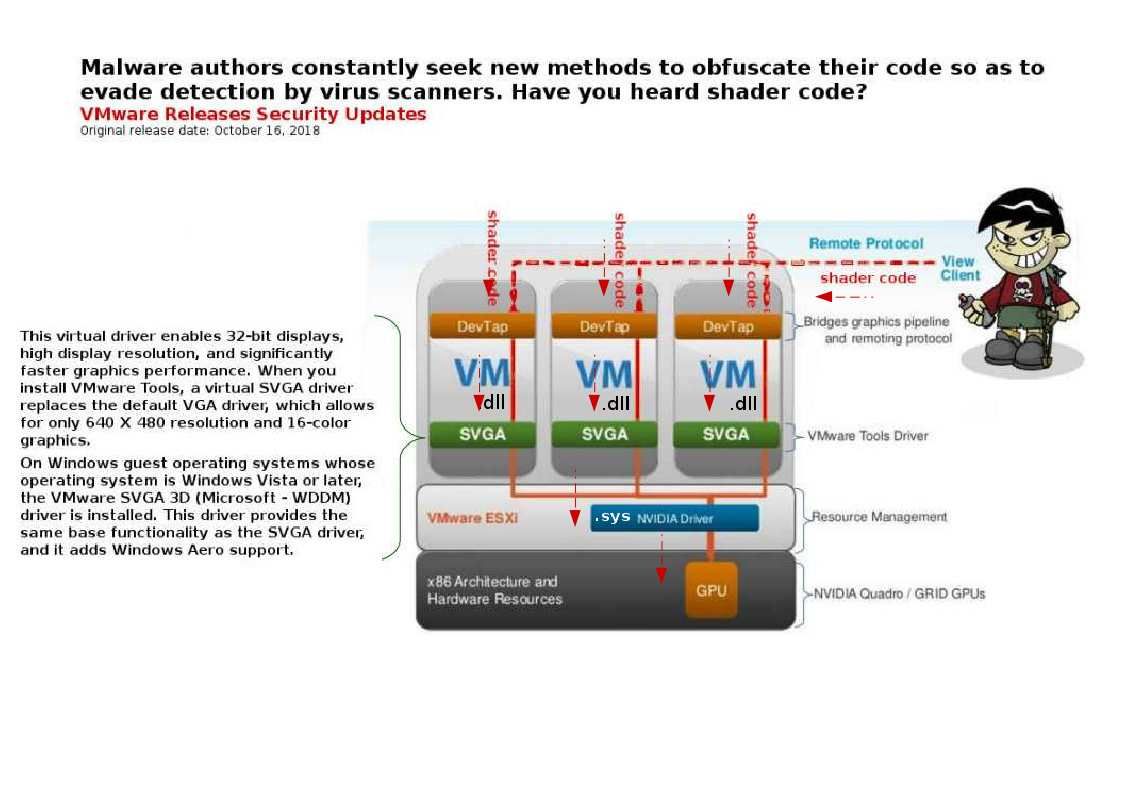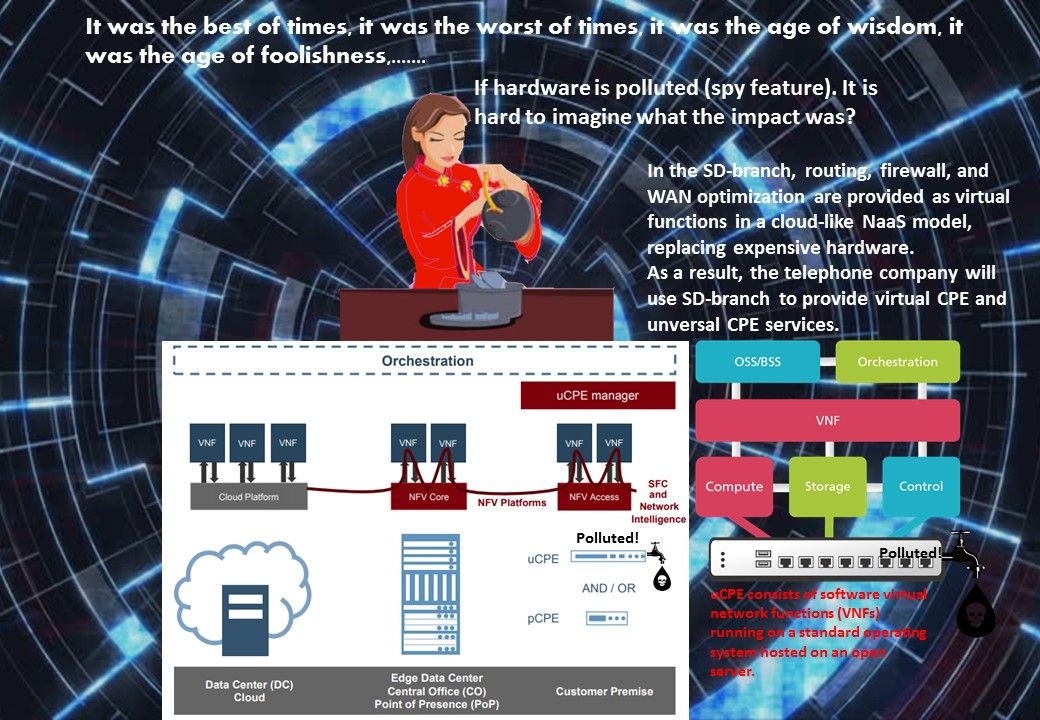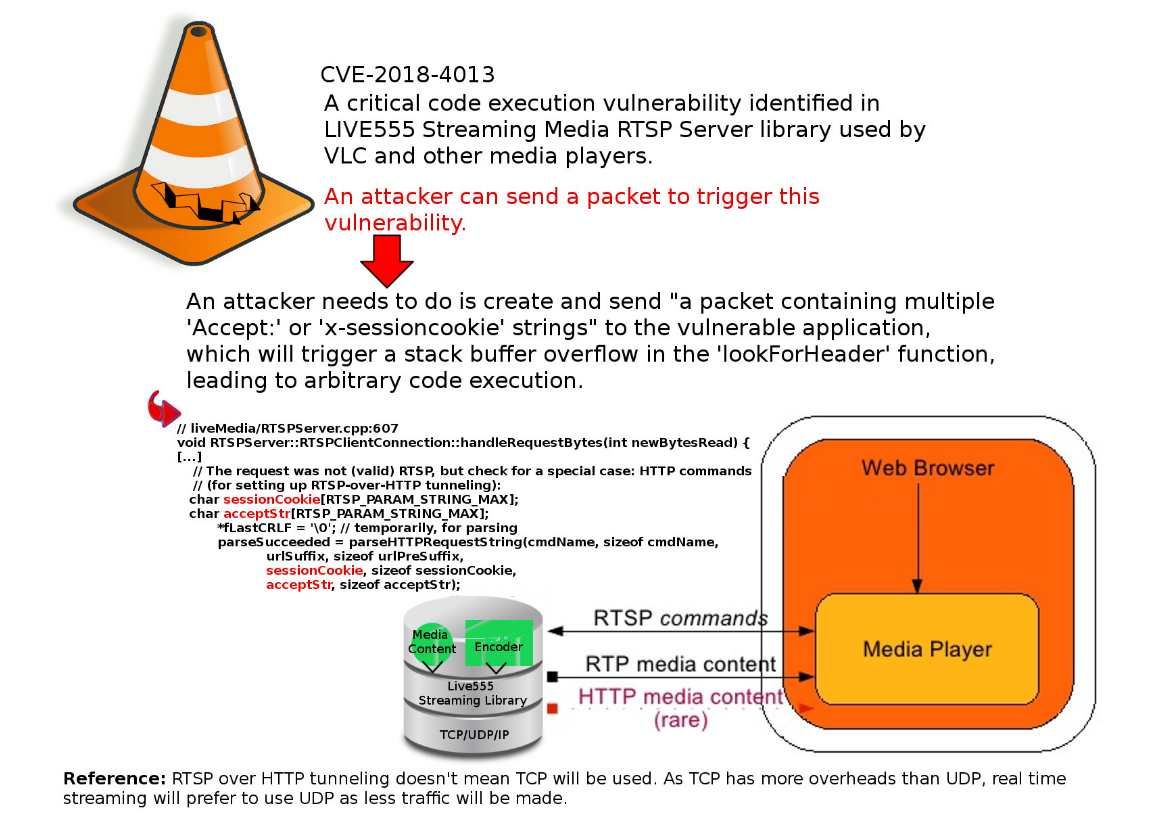
The VLC is a packet-based media player it plays almost all video content. It can play some, even if they’re damaged, incomplete, or unfinished, such as files that are still downloading via a peer-to-peer (P2P) network. So it is very popular in the IoT Environments especially video streaming in vehicular IoT (VSV-IoT) environments. However security researchers have discovered a serious code execution vulnerability in the LIVE555 streaming media library.
If above vulnerability occurs in your devices, what will be happened?
If the stack buffer is filled with data supplied from an untrusted user then that user can corrupt the stack in such a way as to inject executable code into the running program and take control of the process. As a result this method is able for attacker to gain unauthorized access to a computer.
So your vulnerable IoT device will be involuntary join into the IoT Botnet army. So please be careful.
The vendor released security patches on October 17 (see below):
http://www.live555.com/liveMedia/public/
Remark: RTSP over HTTP tunneling doesn’t mean TCP will be used. As TCP has more overheads than UDP, real time streaming will prefer to use UDP as less traffic will be made.