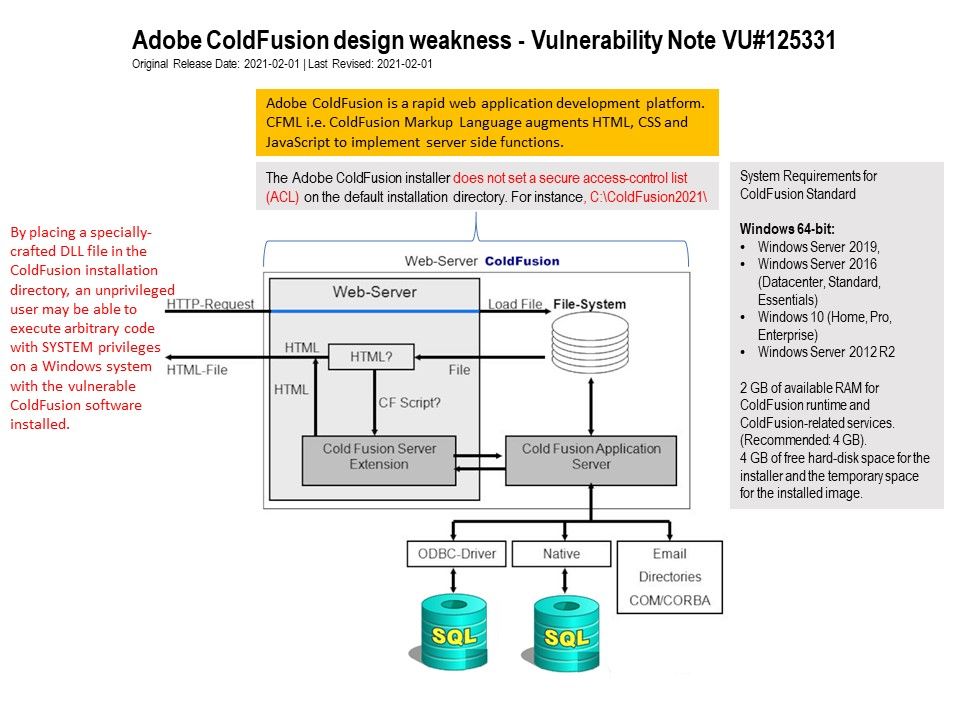
Background: Adobe ColdFusion is a development platform that uses CFML to quickly build modern web apps. Unlike other programming languages, ColdFusion is tag-based. It’s easy to use and can be the backbone of numerous development modules and functionalities.
Dynamic-link library loading mechanism: The DLL loaded once and all programs share the same in-memory copy of code. The read-only sections of the DLL loader uses a technique called “memory mapping” to map the DLL into the process’s address space. The pages are only loaded into physical memory once for all processes, even though they may have the page mapped to different address in their virtual address space. If no design weakness occurs, dynamically-allocated memory is not shared.
Question: Can the .dll file be replaced while the application is running? If you would like to update DLLs that applications use in Windows without terminating the process. Yes, it is possible, but the application must have special machanism to unload the current running DLL and reload the new DLL file.
Vulnerability Details:
- By placing a malicious DLL with the same name as an ambiguously specified DLL in a location that Windows searches before the legitimate DLL. By default C:[\]ColdFusion2021.
- 2. Remote DLL preloading attacks occur when a program sets its current directory to a remote location such as a Web share before loading a DLL. Or Modify the program loads DLLs by replacing an existing DLL or modifying a .manifest or .local redirection file, directory, or junction to cause the program to load a different DLL.
Reference article: About Adobe ColdFusion is vulnerable to privilege escalation due to weak ACLs – https://kb.cert.org/vuls/id/125331