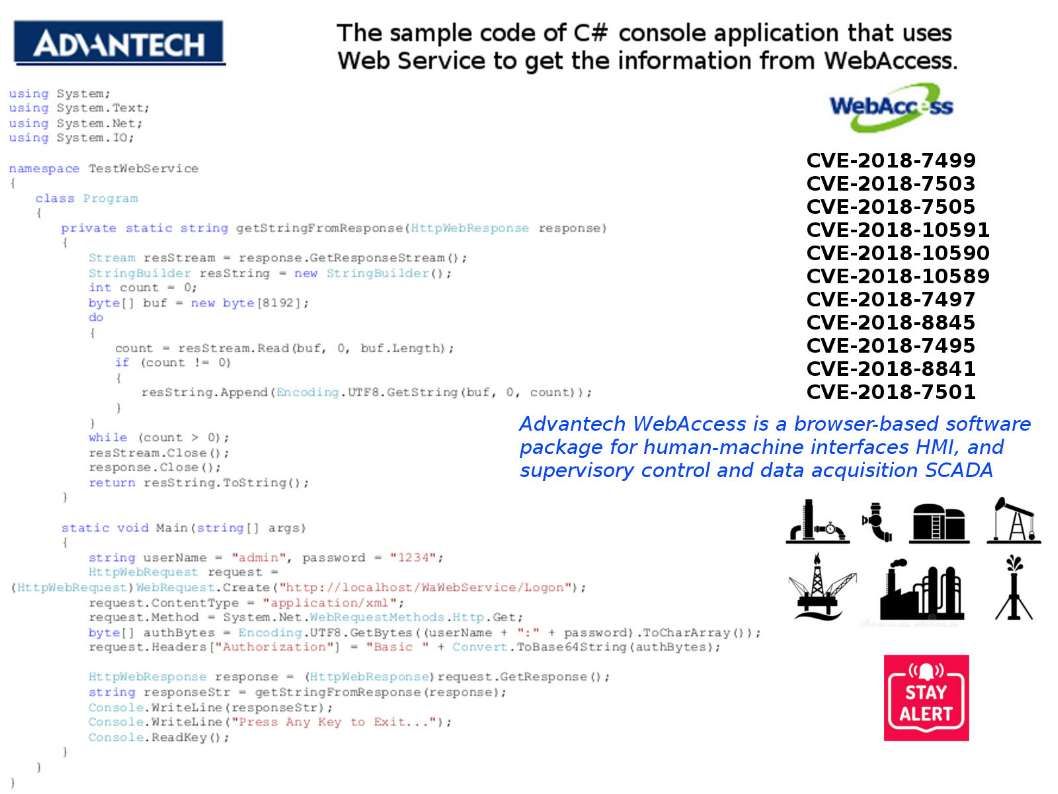
The cyber attacks are wreak havoc today. In order to protect the power facility, water supply, Gas supply and petroleum industry daily operations. The SCADA control system vendor implemented security control in their system infrastructure. However when vulnerabilities encounter on their products. The remediation step of the vendor response sometimes not in effecient. For instance, Advantech one of the key player of SCADA WebAccess. But it lack of motivation to drive the remedation solution on their products. There is no official announcement how to do the remedation on their products so far. Vulnerabilities are shown as below:
CVE-2018-7499 – buffer overflow vulnerabilities which may allow an attacker to execute arbitrary code
CVE-2018-7503 – a path transversal vulnerability which may allow an attacker to disclose sensitive
CVE-2018-7505 – information on the target TFTP application has unrestricted file uploads to the web application without authorization, which may allow an attacker to execute arbitrary code.
CVE-2018-10591 – allow an attacker can create a malicious web site, steal session cookies, and access data of authenticated users.
CVE-2018-10590 – exposure vulnerability through directory listing has been identified, which may allow an attacker to find important files that are not normally visible.
CVE-2018-10589 – WebAccess Scada Node versions prior to 8.3.1, and WebAccess/NMS 2.0.3 and prior, a path transversal vulnerability has been identified, which may allow an attacker to execute arbitrary code.
CVE-2018-7497 – several untrusted pointer dereference vulnerabilities have been identified, which may allow an attacker to execute arbitrary code.
CVE-2018-8845 – a heap-based buffer overflow vulnerability has been identified, which may allow an attacker to execute arbitrary code.
CVE-2018-7495 – an external control of file name or path vulnerability has been identified, which may
CVE-2018-8841- allow an attacker to delete files.
an improper privilege management vulnerability may allow an authenticated user to modify files when read access should only be given to the user.
CVE-2018-7501 – several SQL injection vulnerabilities have been identified, which may allow an attacker to disclose sensitive information from the host.