Git community disclosed a high serverity of vulnerabilies (CVE-2018-11235). Since the impact of this vulnerabilities might influence many software application.
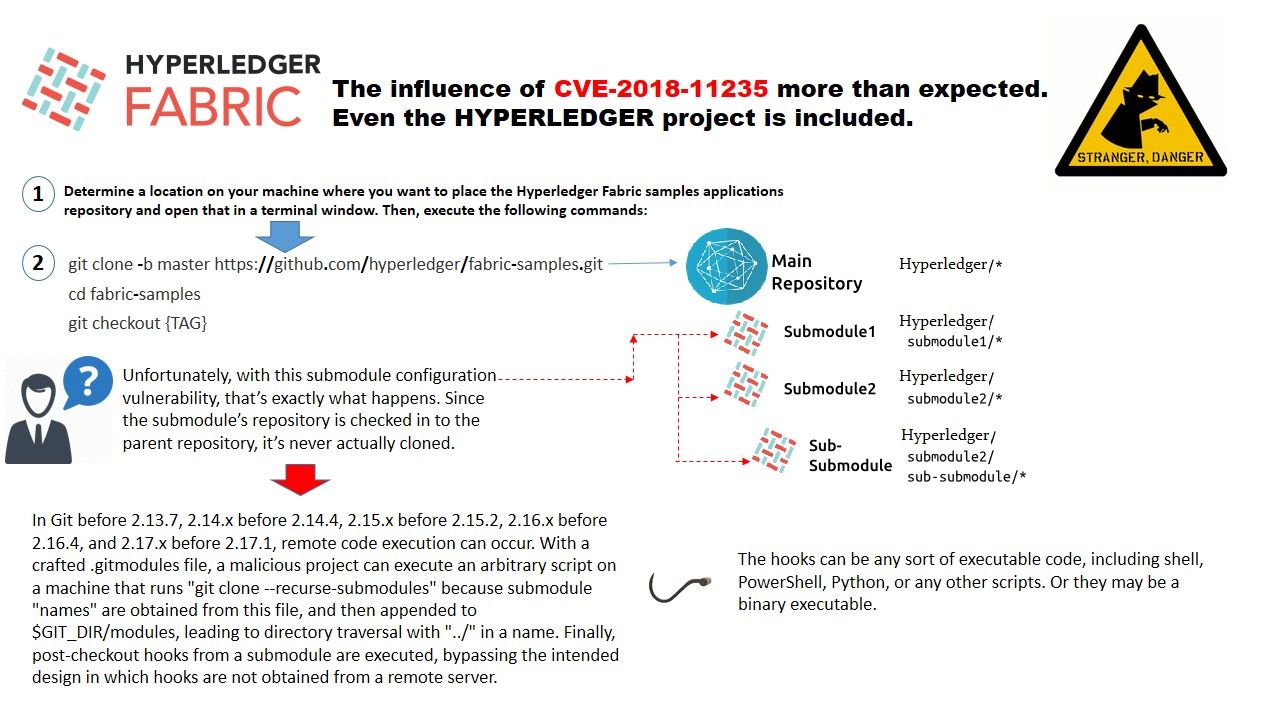
The major design weakness of this vulnerability is that when you git clone a repository, there is some important configuration that you don’t get from the server includes .git/config file, and things like hooks, which are scripts that will be run at certain points within the git workflow. For instance, the post-checkout hook will be run anytime git checks files out into the working directory. As a result hacker can appended to $GIT_DIR/modules, leading to directory traversal with “../” in a name. Finally, post-checkout hooks from a submodule are executed, bypassing the intended design in which hooks are not obtained from a remote server. As a result, hacker has way to implant malware to the library.
This vulnerability also jeopardizing hyperledger project. Please refer to above diagram for reference.
For details of vulnerability. Please refer below:
https://nvd.nist.gov/vuln/detail/CVE-2018-11235
Solution
- Examine submodule’s folder names closely.
- No longer contain .. as a path segment, and they cannot be symbolic links.
The programming parameter must be within the .git repository folder.
I just like the helpful info you supply to your articles.
I’ll bookmark your blog and check again right here regularly.
I am somewhat certain I’ll be informed a lot of new stuff right right here!
Best of luck for the following!