Preface: To do the remedy of CVE-2020-0688, you need to install the security update in addition to the Cumulative Updates.
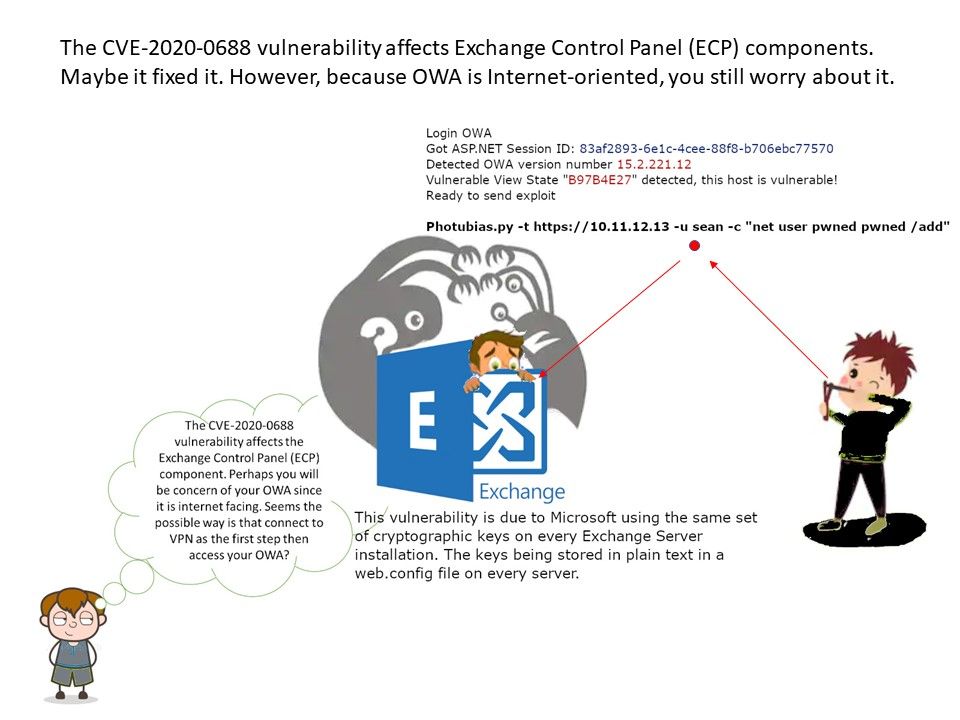
Vulnerability Background: Microsoft using the same set of cryptographic keys on every Exchange Server installation. The keys being stored in plain text in a web.config file on every server.
Details: Microsoft release the patch on 11th Feb, 2020. Less than 2 weeks later. Researchers released proof of concept (POC) exploits for this vulnerability on February 24, 2020. If you have chosen publish Exchange externally. This patch must be applied.
Attacker exploit this vulnerability is easy. The social network sometimes unintentionally leave the finger print (company email address). When attacker got the email address on hand. The elaborate email subject and content presents challenges for traditional security tools, because it is designed specifically to evade detection. If victim fall to the trap (phishing mail) which lure they provide the credential. Even though it is a non privileges user.Attacker can activated this vulnerability to conduct the remote code execution.
“They will try to locate you OWA server. If your existing Exchange SRV is vulnerable. The attack channel can pass through your OWA.”
Remedy: Official announcement – https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0688
Does your site have a contact page? I’m having
trouble locating it but, I’d like to shoot you an email.
I’ve got some recommendations for your blog you might be
interested in hearing. Either way, great blog
and I look forward to seeing it grow over time.