Preface
A fascinating, unusual story which creates an eerie atmosphere. The security report issued by Kaspersky on 10th May 2018 driven my interest to do this study. So the report equivalent to enlightenment my conception.
Background
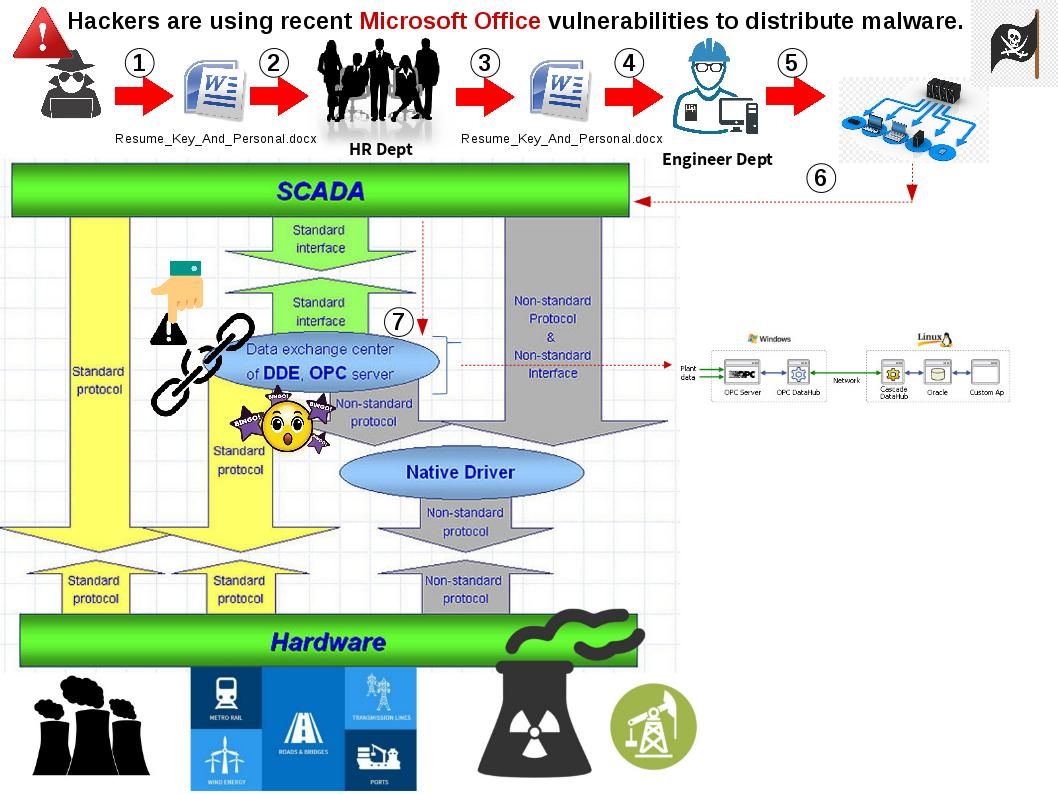
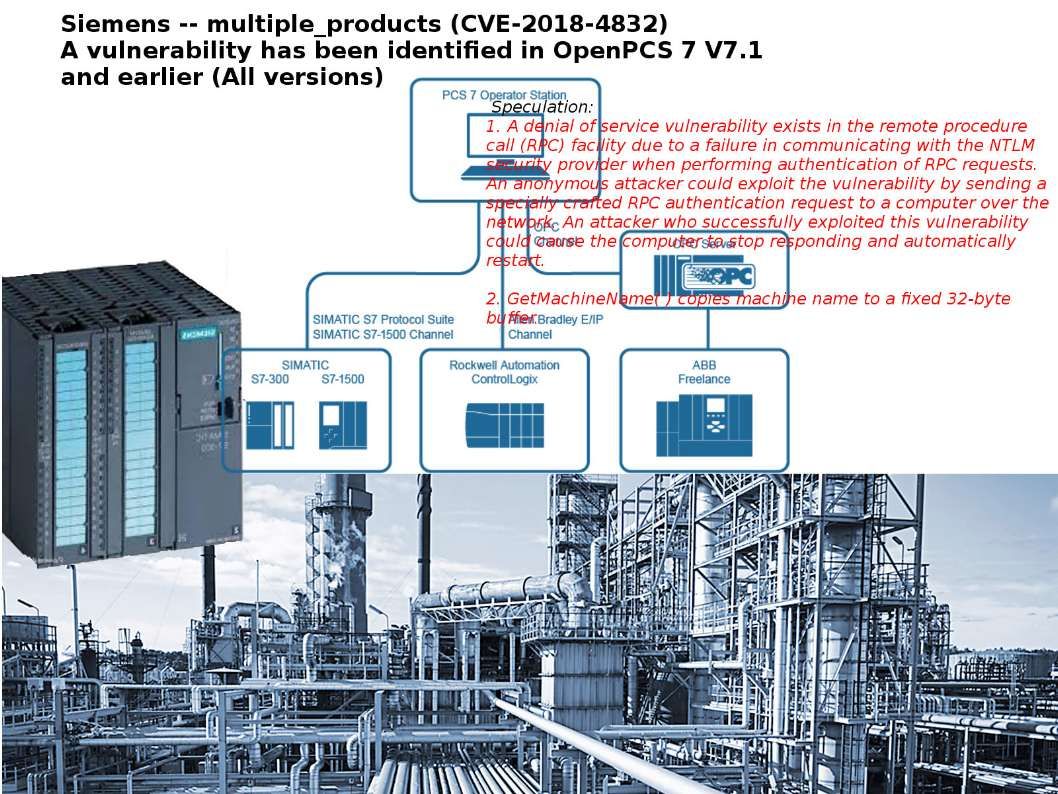
A tremendous potential cyber attack found by Cisco. Thereby it announced to public last week. They reveal this unknown story to the world. And therefore the major security focus shift to a new malware. As a result, we know the technical specifications of malware so called “VPNFilter”. However, similar cyber attacks was encountered in past. A similarity of those cyber attacks are focusing the public facilities especially nuclear power facility , gas and water supply system as the major target. We bring your attentions today for OPC UA (Object Linking and Embedding for Process Control Unified Automation) to OPC Unified Architecture (OPC UA) system vulnerabilities. Those vulnerabilities are not running in high profile. But it requires technical people for attention.
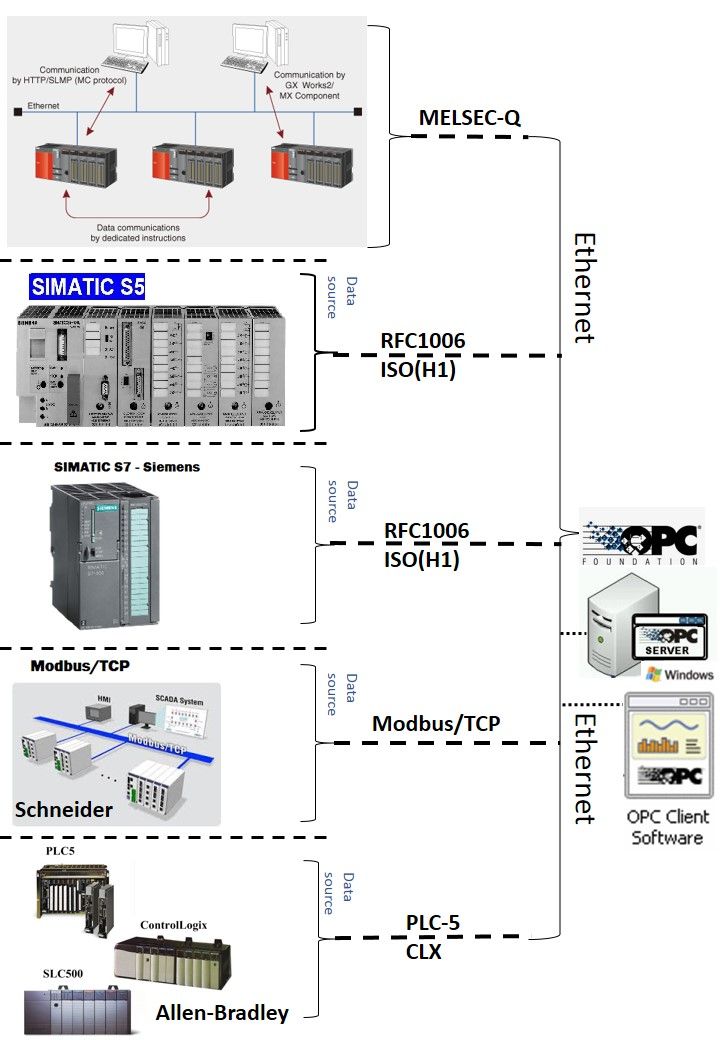
About OPC & OPC Unified Architecture
OPC is an industry standard, it defines methods for exchanging realtime automation data between PC-based clients using Microsoft operating systems. The organization that manages this standard is the OPC Foundation. OPC Unified Architecture (OPC UA) is a machine to machine communication protocol for industrial automation developed by the OPC Foundation.
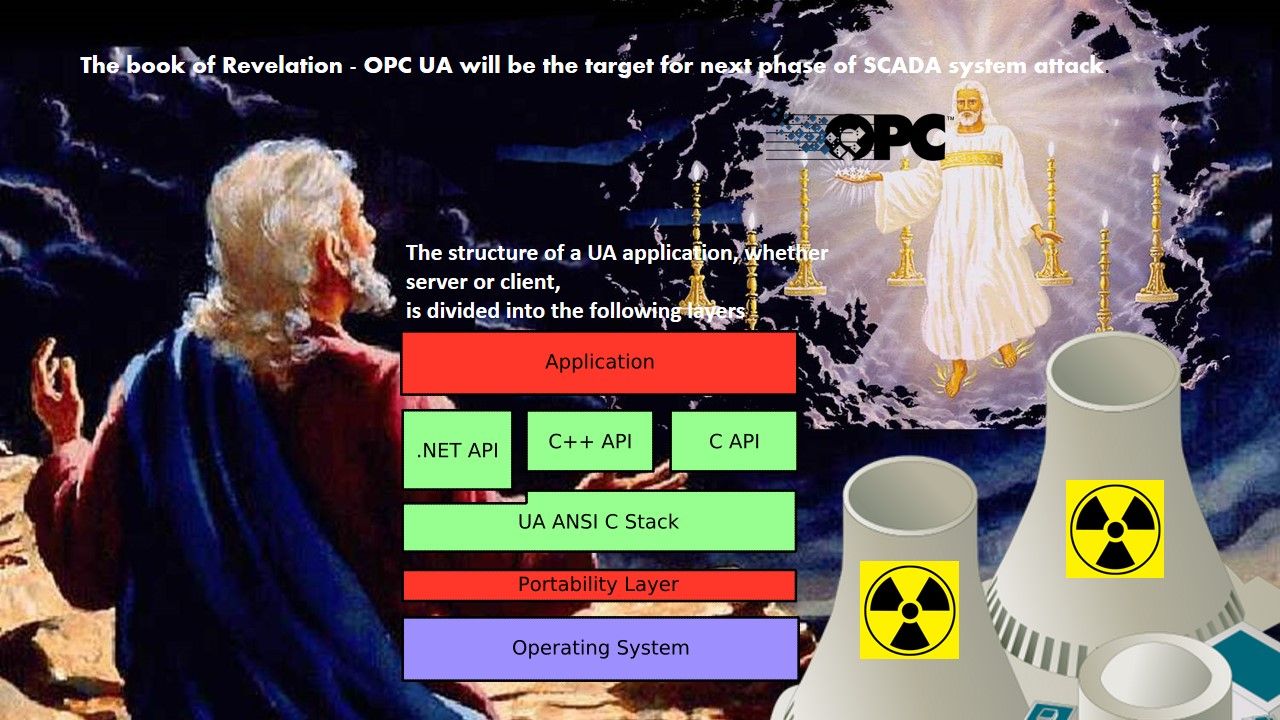
Overview of OPC Unified Architecture
Kaspersky technical findings
Referring to technical report announced by Kaspersky on 10th May 2018. The key critical design flaws are shown as below:
- Quote: OPC UA was designed to support data transport for two data types: the traditional binary format (used in previous versions of the standard) and SOAP/XML. Today, data transfer in the SOAP/XML format is considered obsolete in the IT world and is almost never used in modern products and services. The prospects of it being widely used in industrial automation systems are obscure, so we decided to focus our research on the binary format.
………………………….
It turned out that part of the network services in the system we analyzed communicated over the OPC UA protocol and most executable files used a library named “uastack.dll”. ………
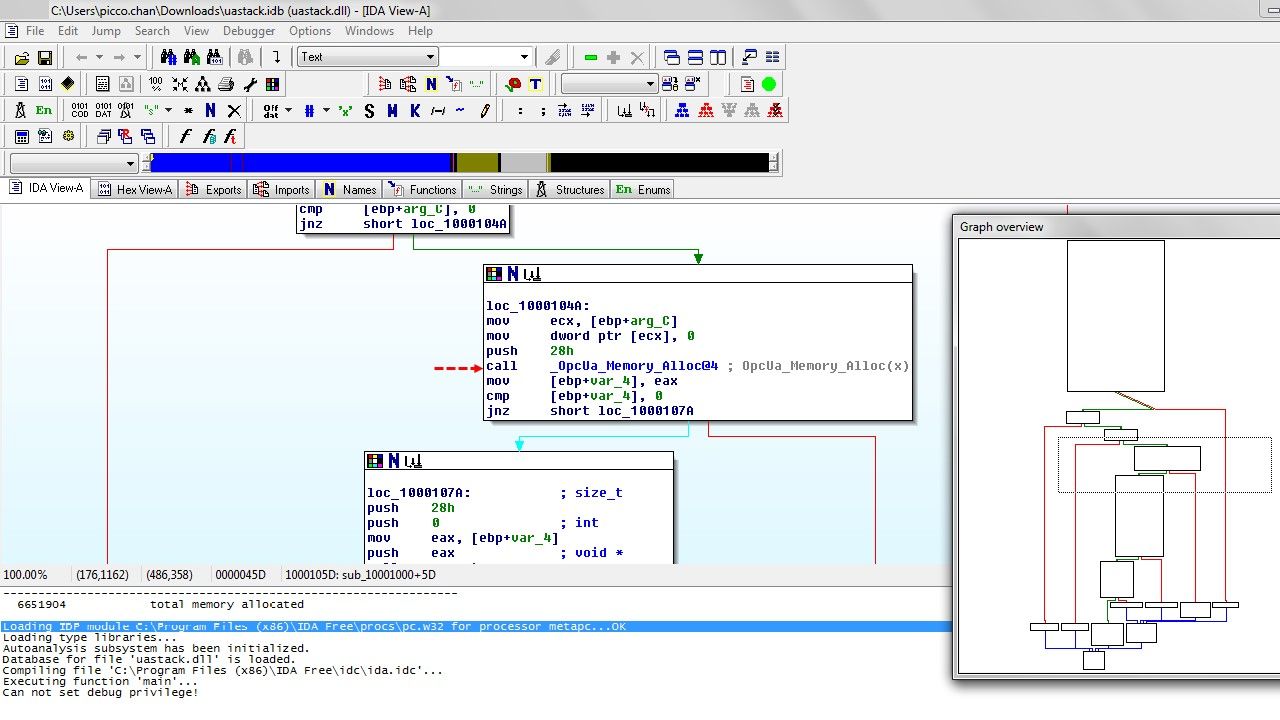
…………After developing a basic set of mutations (bitflip, byteflip, arithmetic mutations, inserting a magic number, resetting the data sequence, using a long data sequence), we managed to identify the first vulnerability in uastack.dll. It was a heap corruption vulnerability, successful exploitation of which could enable an attacker to perform remote code execution (RCE), in this case, with NT AUTHORITY/SYSTEM privileges.
Hints – See whether below assembly language source code (call OpcUa-memory_Alloc@4) can provides any idea to you in this regard.
2. In the process of analyzing the application, found that it used the XmlDocument function, which was vulnerable to XXE attacks for .NET versions 4.5 and earlier.
Hints: What is XXE attack? Below picture shown traditional XXE attack for reference.This XXE attack so called billion laughs attack .

Remark: By disabling DTDs, application developers are also able to strengthen the parser’s ability to protect itself against DoS (denial of service) attacks.
My observation:
Upon inspection, the OPC UA requires the following library files.
libeay32.dll, ssleay32.dll, and uastack.dll
The above library file (ssleay32.dll) belongs to OpenSSL 1.0.2j. It was configured and built with the options no-idea, no-mdc2, no-ntt, and no-rc5 to avoid patent issues. If bugs are found in the version of OpenSSL. You may compile and use your own version because this is a open source program.
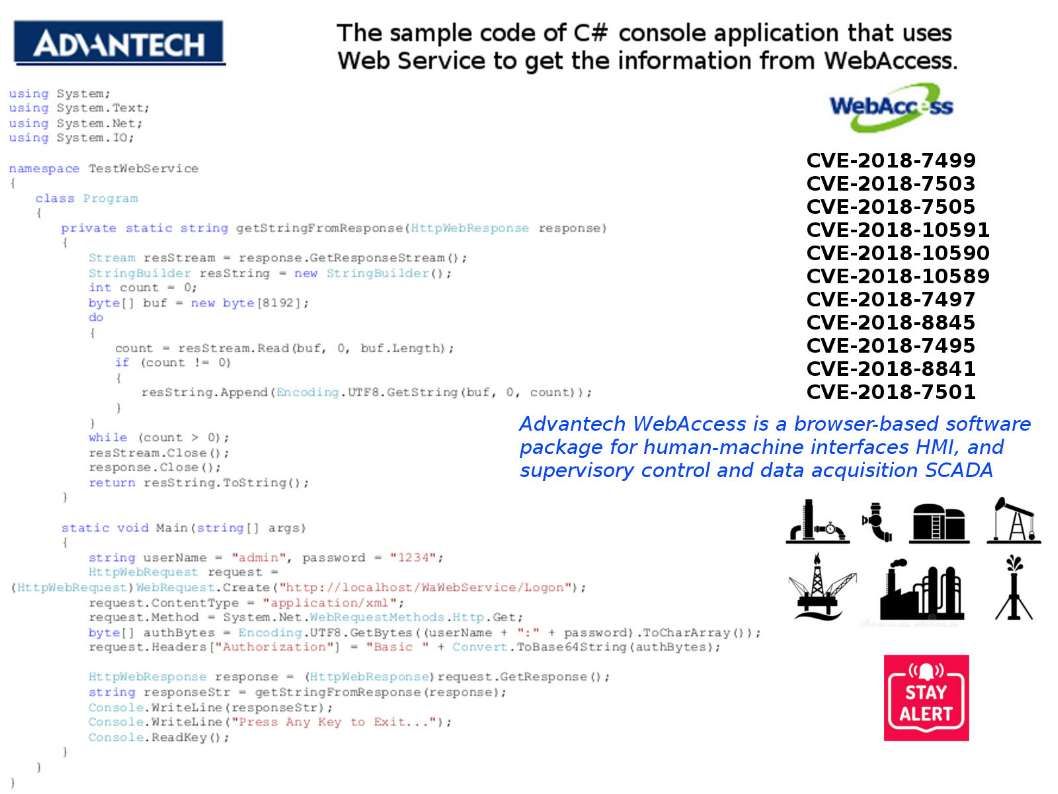
Reminder: Kaspersky Labs identified 17 zero-day vulnerabilities in OPC Foundation open source code. For more details about the report, please refer below url for reference.
https://opcfoundation.org/news/press-releases/review-kaspersky-labs-report-confirms-opc-foundations-transparent-open-source-opc-ua-implementations-strategy-improves-security/
— End —